Modernizing Legacy Applications to Reduce Technical Debt
Modernizing Legacy Applications to Reduce Technical Debt
Modernizing Legacy Applications to Reduce Technical Debt
Managing technical debt in legacy systems means systematically identifying, prioritising and fixing the architectural, code and infrastructure shortcuts that make critical older platforms risky and expensive to change. In 2025, CIOs in the US, UK and EU are leaning on structured audits, risk-based prioritisation and phased modernization (refactor, replatform, rehost or replace) to cut outages, reduce compliance risk and unblock AI and data initiatives.
Introduction.
Legacy technical debt has moved from a “developer headache” to a board-level risk as outages, compliance fines and stalled AI programmes stack up across US, UK and EU enterprises. Boards are now asking not just “Why is this system down?” but “Why are we still running the bank/NHS trust/insurer on 30-year-old code?”
Recent surveys estimate that outdated technology and technical debt can cost large enterprises around $300–$370 million per year in lost productivity, failed transformation and maintaining legacy systems alone (IT Pro [1]). Another study found that legacy tech upgrades cost the average business about $2.9 million in 2023, with most organisations spending over $2 million annually just to keep old platforms alive.
Think of a US bank in New York with a mainframe core patched to expose Open Banking APIs, a UK NHS trust in Manchester juggling multiple EHR systems, or a German insurer in Munich constrained by decades-old policy admin software. Each has bolted on integrations, workarounds and manual processes to “go digital” without touching the core. The result: brittle systems, spiralling costs and regulatory scrutiny under GDPR, UK-GDPR, DORA, HIPAA and PCI DSS.
This guide looks at what technical debt in legacy systems really means in 2025, its business and compliance impact, how to measure and prioritise it, and a practical modernization roadmap for US, UK and EU organisations including where a partner like Mak It Solutions fits into your software modernization journey.
What Technical Debt in Legacy Systems Really Means in 2025
Technical debt in legacy systems is the accumulated architectural, code and infrastructure compromises that make critical, often decades-old platforms expensive, risky and slow to change. It’s not just “old code”; it’s the gap between how your core systems work today and how they need to work to safely support modern digital, AI and regulatory demands.
Technical Debt vs “Old Code” vs Maintenance Backlog
Not all old systems are a technical debt crisis. A COBOL mainframe in New York that’s stable, well-documented and rarely changed may be “old code” but not an active fire. A maintenance backlog, meanwhile, is simply the queue of tickets and upgrades you haven’t done yet.
True legacy technical debt sits where:
The architecture fights every change request.
Quick fixes have layered on complexity.
You’re paying high “interest” in incidents, workarounds and lost opportunities.
Typical examples include:
Mainframes with decades of point-to-point integrations in US banks.
On-prem SAP instances heavily customised for German tax and HR rules.
Custom Java or .NET monoliths serving retail and insurance portals in London, Berlin or Frankfurt.
When boards talk about legacy systems technical debt risks, they’re usually pointing at these critical systems where a single change request can take months and six figures in consulting spend.
How Legacy Systems Create Compounding Technical Debt
Legacy technical debt compounds because every workaround today makes the next change harder tomorrow. Common causes include:
Tactical fixes to meet regulatory deadlines or client demands.
Vendor lock-in and hard-coded integrations to specific platforms.
Heavy customisation of ERP/CRM and core platforms.
Unsupported middleware and libraries.
Shadow IT solutions built around system gaps.
Industry analysis suggests unaddressed technical debt can grow by roughly 20% per year as complexity and risk accumulate (Profound Logic [5]). That means a system with $1 million in estimated debt today can effectively double in under four years if you delay action.
Patterns differ by region:
US enterprises often have complex multi-cloud estates and aggressive product roadmaps — quick fixes pile up around legacy cores.
UK public sector and the NHS must meet stringent availability, safety and data protection requirements, so they added layers of risk controls instead of replacing unstable cores.
German Mittelstand manufacturers frequently run ageing on-prem ERP and MES systems, tweaked over decades for custom processes and local regulations.
At this point, a structured legacy code refactoring strategy and digital transformation of core systems stops being optional and becomes a risk-management requirement.

Early Warning Signs You Have a Legacy Tech-Debt Problem
You don’t need a full assessment to spot trouble. Common warning signs for CIOs and Heads of Engineering in the US, UK and EU include:
Long change lead times: simple changes take weeks or months.
High incident frequency: recurring outages or “brownouts” on the same systems.
“No one wants to touch that system”: tribal knowledge concentrated in a few experts or ageing contractors.
Regulatory exceptions and manual controls: spreadsheets, manual reconciliations or “temporary” workarounds for GDPR, DORA or HIPAA gaps.
Failed integrations: modern SaaS or API initiatives keep stalling on legacy constraints.
Once you see this pattern, you’re ready for a structured technical debt audit and remediation programme rather than more heroics.
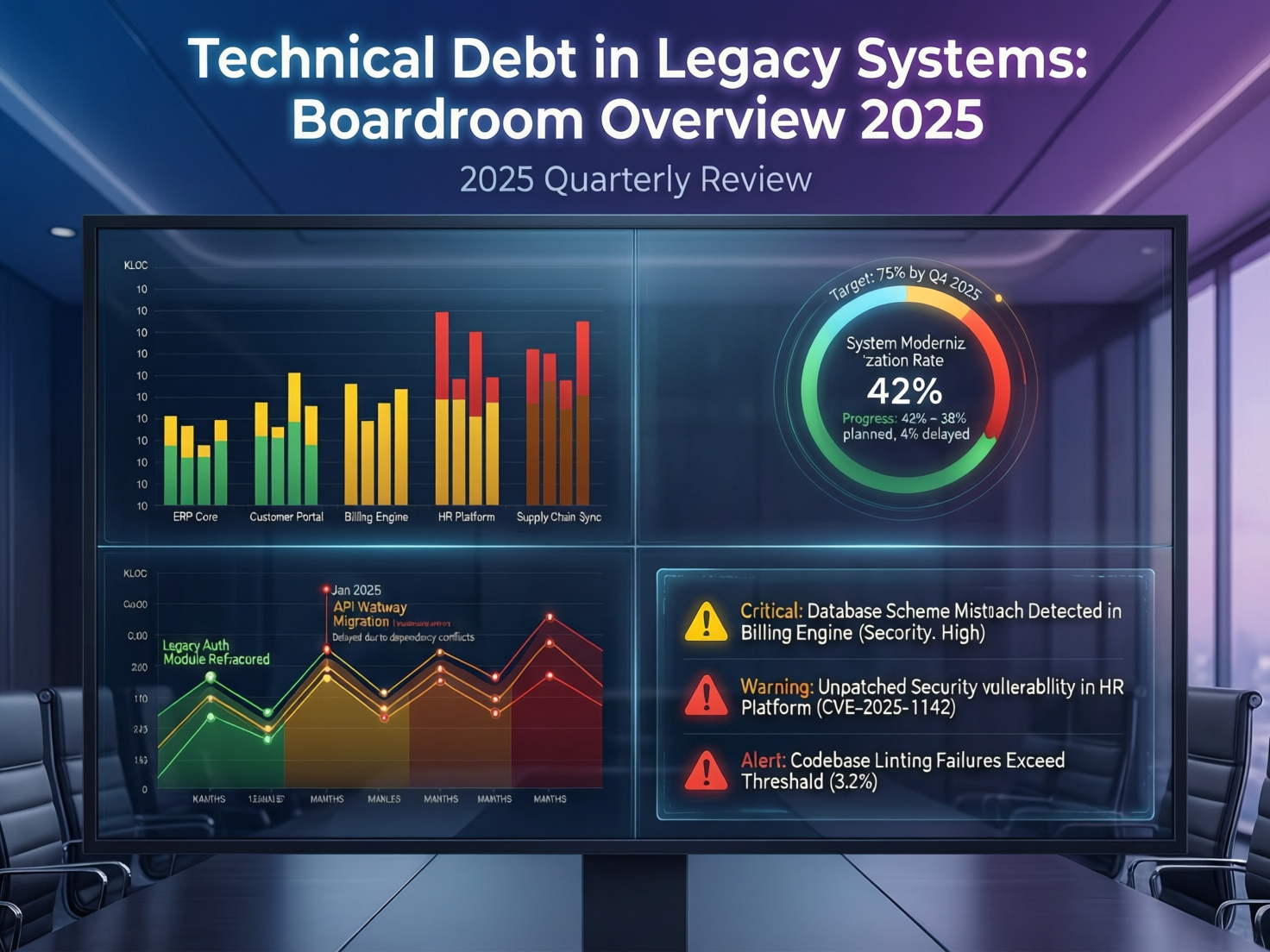
Business, Risk and Compliance Impact of Legacy Technical Debt
Unmanaged technical debt in legacy systems drives hard financial losses, operational fragility and growing regulatory exposure across the US, UK and EU. It shows up in P&L, risk dashboards and audit findings not just in engineering backlogs.
Cost of Legacy Systems and Technical Debt for Enterprises
Legacy platforms hit budgets in three main ways.
Direct maintenance and upgrade spend
Surveys suggest that organisations spend millions per year per legacy platform, with one analysis estimating the average cost of operating and maintaining a single legacy system at roughly $30 million, and global maintenance spend exceeding $1 trillion annually.
Indirect costs and opportunity loss
Technical debt drives failed transformation projects, lost deals and slow time-to-market. Some enterprises report over $130 million per year in wasted spend from failed modernization initiatives and maintaining outdated systems
Data and AI drag
In US healthcare, UK financial services and German manufacturing, legacy systems fragment data and block real-time analytics, raising the cost of every AI or data platform initiative (Mak it Solutions [8]).
By 2025, some forecasts suggest around 40% of IT budgets are effectively spent just keeping technical debt under control instead of funding innovation.
Regulatory and Security Risks.
Old databases, brittle logging and manual access controls often fail modern regulatory expectations:
GDPR/DSGVO & UK-GDPR require demonstrable control over personal data lifecycle, access and breach notification. Legacy apps with unclear data flows, shared accounts or incomplete logs make this hard to evidence.
DORA (Digital Operational Resilience Act) forces EU financial entities to prove ICT resilience, incident response and third-party risk controls including around legacy banking cores and payment systems.
HIPAA in the US healthcare sector demands strict safeguards for electronic protected health information (ePHI); ageing EHR or billing systems often struggle to meet updated Security Rule expectations.
PCI DSS and SOC 2 require strong access control, encryption, monitoring and change management around cardholder and customer data areas where legacy stacks often rely on shared accounts, manual changes and limited audit trails (PCI Security Standards Council.
BaFin guidance (BAIT, MaRisk) pushes German financial institutions to strengthen IT governance and security, putting pressure on ageing cores in Frankfurt, Berlin and Munich.
Regulators such as BaFin, EIOPA and national data protection authorities now explicitly expect credible modernization and operational resilience plans, not perpetual “temporary measures”.
Impact on AI, Innovation and Open Banking / PSD2
Technical debt in legacy systems doesn’t just slow releases; it can stall entire innovation themes:
AI and analytics:
Batch-only data, inconsistent schemas and missing metadata make it hard to build reliable AI models or modern lakehouse architectures across US and EU entities (Mak it Solutions [8]).
Open Banking / PSD2
Many European banks still expose PSD2 APIs around core systems that were never designed for real-time, high-volume API traffic. This adds latency, fragility and security risk.
SaaS and ecosystem integration
Legacy ERPs and policy systems often can’t easily connect to modern SaaS CRMs, billing systems or insurtech platforms without brittle custom integration.
For many boards, the question has quietly shifted from “What does modernization cost?” to “What are we losing every quarter by not modernizing?”
How to Measure and Prioritise Technical Debt in Legacy Applications
Measuring legacy technical debt requires a structured audit, risk scoring and a prioritisation matrix that balances regulatory risk, business value and engineering effort. The practical question is: which systems must we modernise first, and how?
Designing a Technical Debt Audit Framework for Legacy Systems
A pragmatic technical debt audit framework for legacy systems covers four dimensions:
Scope definition
Applications (core systems, channels, integration layers)
Integrations (APIs, ESBs, batch jobs, file transfers)
Infrastructure (on-prem, cloud, network, DR)
Data (stores, pipelines, quality, lineage)
Key metrics
Change failure rate and time-to-restore for each system
Lead time for change (requirements → production)
Code complexity and test coverage (where possible)
Unsupported components (EoL middleware, databases, OS)
Security findings: known vulnerabilities, pen-test issues, audit findings
Risk and compliance lens
Data categories (personal, health, payment, regulated financial data)
Regulatory mapping (GDPR/UK-GDPR, HIPAA, PCI DSS, DORA, BaFin)
Business criticality (revenue, safety, customer impact)
Software modernization roadmap
For each system, propose a target state: refactor, replatform, rehost, replace or retire.
This gives CIOs and Chief Risk Officers a shared view of where technical debt audit and remediation should start, especially in US enterprises under HIPAA/SOC 2 and EU banks under DORA.

Prioritisation Matrix for Legacy Apps (Risk × Value × Effort)
A technical debt prioritisation matrix for legacy apps scores each system on three axes:
Risk: regulatory exposure, security, operational resilience.
Value: revenue, strategic importance, user impact.
Effort: complexity, dependencies, change volume.
You can then map, for example.
An NHS EHR system in Leeds: high risk (patient safety, UK-GDPR), very high value, high effort candidate for phased refactor and platform uplift with strong clinical engagement.
A US e-commerce platform in Seattle: high revenue value, medium regulatory risk (PCI DSS, privacy), lower effort if already cloud-hosted — a strong candidate for incremental microservices and performance work.
A German SAP instance in Frankfurt: high regulatory and BaFin relevance, medium–high value, high effort targeted components may be replatformed to S/4HANA or cloud while others remain on-prem short term.
This matrix helps US, UK and EU organisations sequence modernization waves instead of trying to “boil the ocean”.
Paying Down Debt Without Freezing New Features
Engineering leaders can’t simply stop shipping features for two years of refactoring. Common patterns for managing technical debt in legacy systems include:
Debt sprints: allocate entire sprint(s) per quarter to refactoring, test automation or dependency upgrades on priority systems.
5–15% capacity for remediation: bake a fixed percentage of each team’s time into the roadmap for debt work, tied to explicit risk-reduction goals.
Opportunistic refactors: when touching a legacy feature for business reasons, improve adjacent code, tests or pipelines as part of the same change.
Technical debt governance: a cross-functional steering group (CIO, Head of Architecture, platform leads, risk) reviews the debt backlog quarterly and re-prioritises.
Mak It Solutions often helps CIOs stand up this governance layer and measure progress against KPIs, as outlined in our Top CIO Priorities 2025 guidance for US and European enterprises.
Modernising Legacy Systems to Reduce Technical Debt Options & Trade-Offs
To reduce technical debt, CIOs must choose the right blend of refactor, replatform, rehost or replace, based on business criticality, compliance and long-term strategy not just the easiest migration path.
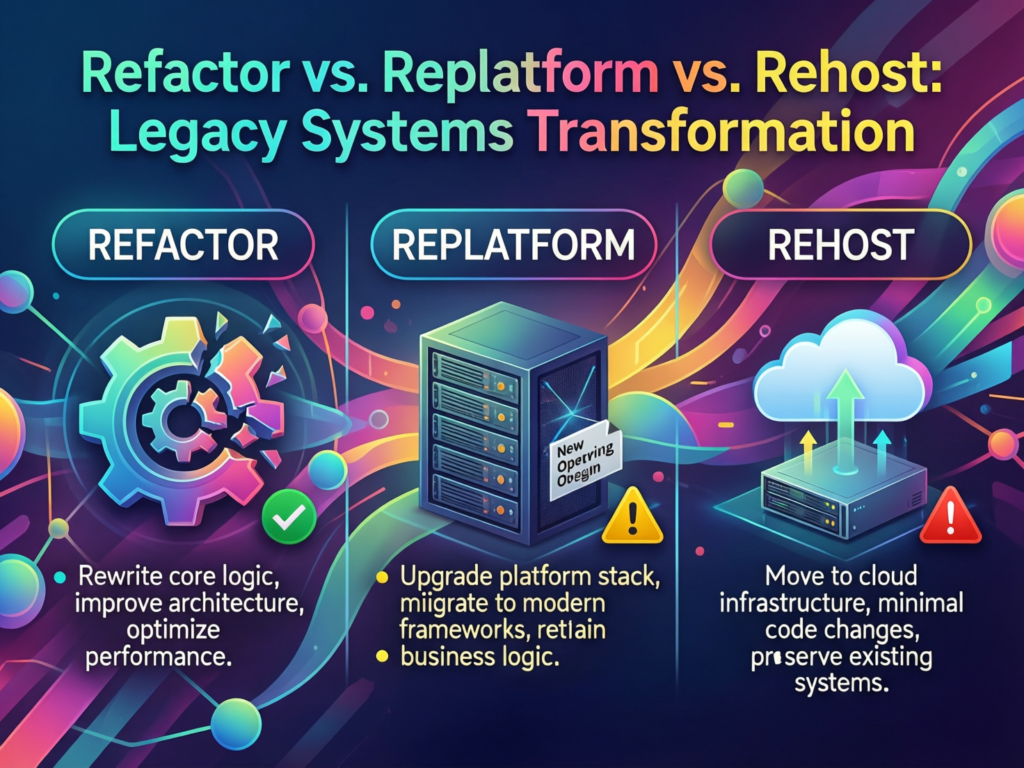
Refactor vs Replatform vs Rehost.
A simple way to compare:
Rehost (“lift and shift”)
Move the system as-is to cloud infrastructure.
Pros: fastest, minimal code change, quick infrastructure wins.
Cons: most technical debt (architecture, code) remains; you may increase cloud spend without gaining agility.
Replatform
Change the underlying platform (e.g. database, app server, container platform) with limited code change.
Pros: modern runtime, better resilience and security; easier to add cloud-native capabilities.
Cons: architecture debt persists; some risky changes; careful testing required.
Refactor
Restructure the code and architecture (e.g. monolith-to-microservices, domain-driven decomposition).
Pros: directly attacks technical debt, unlocks speed and innovation.
Cons: highest engineering effort; requires strong product and architecture leadership.
For mainframe modernization technical debt, a hybrid pattern is common: expose APIs around stable mainframe functions, then gradually “strangle” high-change domains into microservices and event-driven architectures.
Cloud Migration Strategies for Legacy Applications (AWS, Azure, Google Cloud)
Common patterns for legacy migration to AWS, Microsoft Azure or Google Cloud include:
Lift-and-shift to IaaS as a first step, followed by optimisation and refactoring.
Strangler-fig pattern, where new services gradually replace parts of the monolith behind a stable API or gateway.
Domain-based decomposition, prioritising high-change and high-value domains for microservices or serverless (e.g. AWS Lambda, Azure Functions, Cloud Run)
Cloud-native migration from monoliths, moving directly to managed databases, messaging, identity and observability.
The goal is to avoid simply moving technical debt from on-premises to the cloud. Good practice includes:
Modern CI/CD and automated testing.
Observability (logs, metrics, traces) for legacy and new components.
Strong identity and access management, aligned to SOC 2/PCI/GDPR expectations.
Mak It Solutions regularly helps clients in New York, London, Berlin and across wider Europe compare AWS vs Azure vs Google Cloud for modernization programmes.
When to Fully Replace a Legacy Core System
Sometimes the honest answer is: replace the core.
Decision triggers include:
Unmaintainable stacks with no vendor support and scarce skills.
Repeated regulatory or audit failures tied directly to the legacy platform.
Unsustainable costs compared to modern alternatives.
Inability to meet DORA-level resilience or GDPR/UK-GDPR data protection requirements.
Big-bang replacement is risky, especially in banking, healthcare and critical public services. Many US hospitals, NHS trusts and BaFin-regulated banks adopt phased coexistence, where new cloud-native cores run in parallel with legacy, migrating products, regions or cohorts over time.
GEO-Specific Modernization Playbooks (US, UK, Germany/EU)
The core modernization patterns are similar, but US, UK and EU organisations must tailor their approach to local regulators, funding models and ecosystem partners.
US Enterprises: Cloud-First, AI-Ready Modernization
In the United States, enterprises, SaaS vendors and healthcare providers face a triple squeeze:
Modern customer expectations.
HIPAA, SOC 2 and PCI DSS requirements.
Pressure to show AI and cloud ROI to boards and investors.
For US hospital systems in New York or Seattle, legacy EHR and billing platforms must be modernised with the HIPAA Privacy and Security Rules in mind encryption, access controls, audit logging and incident response.
US SaaS providers in San Francisco often use modernization as part of SOC 2 and ISO 27001 journeys, showing that their core platforms meet security and availability controls expected by enterprise customers.
Mak It Solutions supports US and EU clients with cloud-native migration from monoliths and multi-cloud architectures that balance resilience, cost and regulatory needs.
UK Public Sector & NHS: Safely Managing Technical Debt in Critical Systems
In the UK, public sector IT and the NHS must modernise without jeopardising safety, continuity or UK-GDPR compliance.
Typical patterns include.
Introducing API gateways and integration layers in front of legacy EHR and patient systems.
Consolidating overlapping applications across trusts in London, Manchester, Leeds, Edinburgh and Cardiff.
Using phased module-by-module refactors, with strong clinical governance and change management.
Searches like “managing technical debt in NHS legacy systems safely” often lead to strategies that blend technical debt audit and remediation with national digital programmes and cloud frameworks.
Germany & EU Financial Institutions under DORA and BaFin
For banks and insurers in Germany and the wider EU, DORA and BaFin guidance (BAIT, MaRisk) are changing the game.
Key impacts include.
Mandatory ICT risk assessments spanning legacy cores, third-party providers and cloud services.
Stronger expectations for resilience, incident response and testing (including threat-led penetration tests).
Tighter oversight of outsourcing, including core banking and payment systems that rely on legacy COBOL/SAP stacks.
Modernization roadmaps for banks in Frankfurt, Berlin, Munich, Amsterdam, Zurich and Dublin increasingly combine legacy banking system modernization with Open Banking/PSD2 initiatives and data lakehouse platforms for risk and reporting.
Building a Sustainable Technical Debt Management Strategy
Sustainable technical debt management turns modernization from a one-off project into an ongoing governance practice embedded in architecture, funding and delivery. It’s how you avoid recreating 2025’s legacy in 2030.
Roles, RACI and Operating Model for Legacy Tech Debt
A robust operating model clarifies who owns what:
CIO/CTO: overall modernization strategy and investment.
Chief Risk Officer: alignment with enterprise risk and DORA/GDPR/SOC 2 expectations.
Head of Architecture: standards, reference architectures and review gates.
Platform/DevOps teams: shared cloud platforms, observability, CI/CD.
Product and engineering leads: prioritisation and execution of debt work.
A cross-regional steering group for US, UK and EU entities can review technical debt management strategies quarterly, adjust priorities and track KPIs (incident reduction, lead time, compliance findings).
Tooling, Automation and Cloud-Cost Controls
Modern toolchains make it easier to see and reduce technical debt:
Static code analysis and SCA to surface complexity, vulnerabilities and outdated dependencies.
Architecture decision records (ADRs) to document trade-offs and avoid repeated mistakes.
CMDBs and application inventories to keep a live map of systems and dependencies.
Observability platforms (logging, metrics, tracing) to understand real-world behaviour of legacy stacks.
FinOps practices to tie cloud cost spikes back to technical debt in legacy apps.
AI-assisted code analysis and modernization accelerators from AWS, Azure and Google Cloud are increasingly used to scan legacy codebases and suggest refactors or migration patterns
Choosing the Right Partners and Modernization Vendors
For many organisations, the missing piece is capacity and pattern expertise. When selecting partners in the USA, UK or Germany/EU:
Look for proven work in regulated industries (NHS, BaFin-regulated banks, US healthcare).
Ask for reference architectures, sample roadmaps and measurable outcomes (incident reduction, DORA readiness, cloud savings).
Check their multi-cloud and data platform credentials (AWS, Azure, Google Cloud, lakehouse, BI and integration).
Mak It Solutions combines web, mobile, data and cloud expertise with a strong focus on modernization projects for US/UK/EU enterprises from choosing the right hyperscaler to designing data lakehouse architectures and BI platforms that coexist with legacy systems.
2025–2026 Roadmap: From Legacy Technical Debt to Modern Core Systems
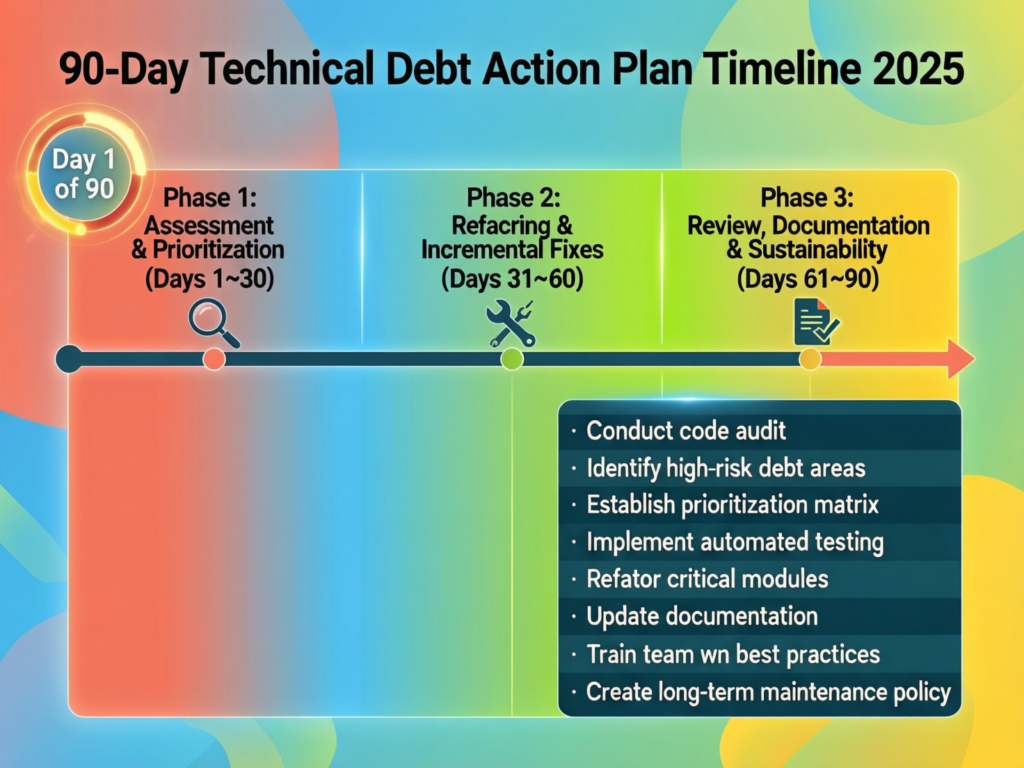
A pragmatic 18–24 month roadmap starts with a focused legacy debt audit, delivers quick wins in the first 90 days, and sequences modernization waves aligned to business outcomes, regulatory milestones and cloud strategy.
90-Day Action Plan to Get Technical Debt Under Control
A practical first-quarter playbook.
Inventory and classify systems
Catalogue core applications, integrations and data stores; flag those touching regulated data (GDPR, HIPAA, PCI DSS, DORA-scoped systems).
Run a quick-scan audit
Use the audit framework to score each system on risk, value and effort, combining engineering, risk and business input.
Prioritise top 5–10 systems
Build a simple prioritisation matrix and agree the first candidates for modernization or heavy remediation.
Pilot modernization on 1–2 systems
Pick a system in New York, London or Berlin where refactor/replatform can show visible progress in 90 days, and use that to refine your approach.
This “test-and-learn” cycle sets up the broader legacy application modernization roadmap.
Building the Business Case for Legacy System Modernization in 2025
Boards in the US, UK and EU want numbers they can track:
Incident and outage reduction, especially where DORA or BaFin oversight applies.
Fines and enforcement action avoided under GDPR/UK-GDPR, HIPAA or PCI DSS.
Revenue protected or unlocked (faster product launches, new open banking use cases).
Cloud and infrastructure cost savings from retiring duplicate legacy platforms.
Map these benefits into a multi-year investment view, aligned to regulatory timelines (for example, DORA’s 2025/2026 requirements for EU financial entities) (EIOPA [14]).
How Your Organisation Can Support Modernization at Scale
To deliver modernization at scale, you’ll typically need:
Internal squads owning specific domains (payments, patient records, underwriting).
A shared platform team running cloud, security and observability.
External partners providing assessments, modernization pods and managed services.
Mak It Solutions can help you run a technical debt audit, design a phased modernization roadmap, and deliver web, mobile, data and integration workstreams across AWS, Azure and Google Cloud for US, UK and EU portfolios.
If your board is finally asking hard questions about technical debt in legacy systems, this is the moment to act before the next outage or audit does it for you. Mak It Solutions works with CIOs across New York, London, Berlin and wider Europe to modernise legacy cores, reduce risk and unblock AI initiatives.
Share a shortlist of your highest-risk legacy platforms and we’ll help you structure a 90-day technical debt audit and modernization plan aligned with GDPR, DORA, HIPAA and PCI DSS. Start with a focused discovery workshop and leave with a practical software modernization roadmap your board — and your engineers can support.( Click Here’s )
FAQs
Q : How often should large enterprises run a technical debt audit on legacy systems?
A : Most large enterprises should run a focused technical debt audit on critical legacy systems at least once a year, with lighter quarterly reviews for high-risk applications. In fast-moving sectors like banking or healthcare, or where DORA and HIPAA apply, many CIOs move to a rolling assessment model, revisiting each critical system every 12–18 months. The key is to tie the audit cadence to change volume, regulatory obligations and incident trends rather than treating it as a one-off project.
Q : What KPIs show that legacy system modernization is actually reducing technical debt and risk?
A : Useful KPIs include reduced change lead time, fewer high-severity incidents on legacy platforms, lower change failure rates and improved time-to-restore after outages. You can also track audit and regulatory findings per system, cloud cost per transaction, and the percentage of critical flows running on modern, well-instrumented platforms. Over 12–24 months, effective modernization should show fewer incidents and exceptions and more frequent, reliable deployments.
Q : How can smaller organisations or SMEs tackle legacy technical debt with limited budgets?
A : SMEs rarely have the budget for massive “rip and replace” projects, so they should focus on small, high-impact changes. Start by identifying 1–2 systems that create the most pain (manual workarounds, frequent outages, compliance headaches) and target those with pragmatic refactors or replatforming. Use managed cloud services to reduce operational overhead, and consider no-code/low-code for less critical workflows while keeping core logic in well-structured code (Mak it Solutions [19]). The aim is to gradually reduce risk while keeping the business running and cash-flow stable.
Q : What’s the best way to align product roadmaps with legacy technical debt reduction initiatives?
A : Bring product and engineering leadership together around a shared prioritisation matrix that includes risk and tech debt factors alongside revenue and customer outcomes. For each major product initiative, ask: “What legacy constraints will block or delay this?” and allocate explicit budget and capacity to remove them. Techniques like “debt epics,” dedicated remediation sprints and reserving 5–15% of ongoing capacity for refactors help ensure that tech debt work is visible, funded and delivered alongside new features rather than competing with them.
Q : How does technical debt in legacy systems affect developer experience and talent retention?
A : Developers stuck maintaining fragile legacy systems with poor tooling, slow deployments and constant firefighting often burn out and leave. Technical debt makes onboarding harder, slows experimentation and limits the use of modern practices like CI/CD, trunk-based development and cloud-native services. Over time, this shrinks your internal talent pool and increases reliance on expensive contractors or niche vendors. Investing in modernization improves developer experience, makes roles more attractive in competitive markets like London, Berlin and San Francisco, and helps you retain the people who understand your business best.