API Security Authentication and Bot Protection Playbook
API Security Authentication and Bot Protection Playbook
API Security Authentication and Bot Protection Playbook
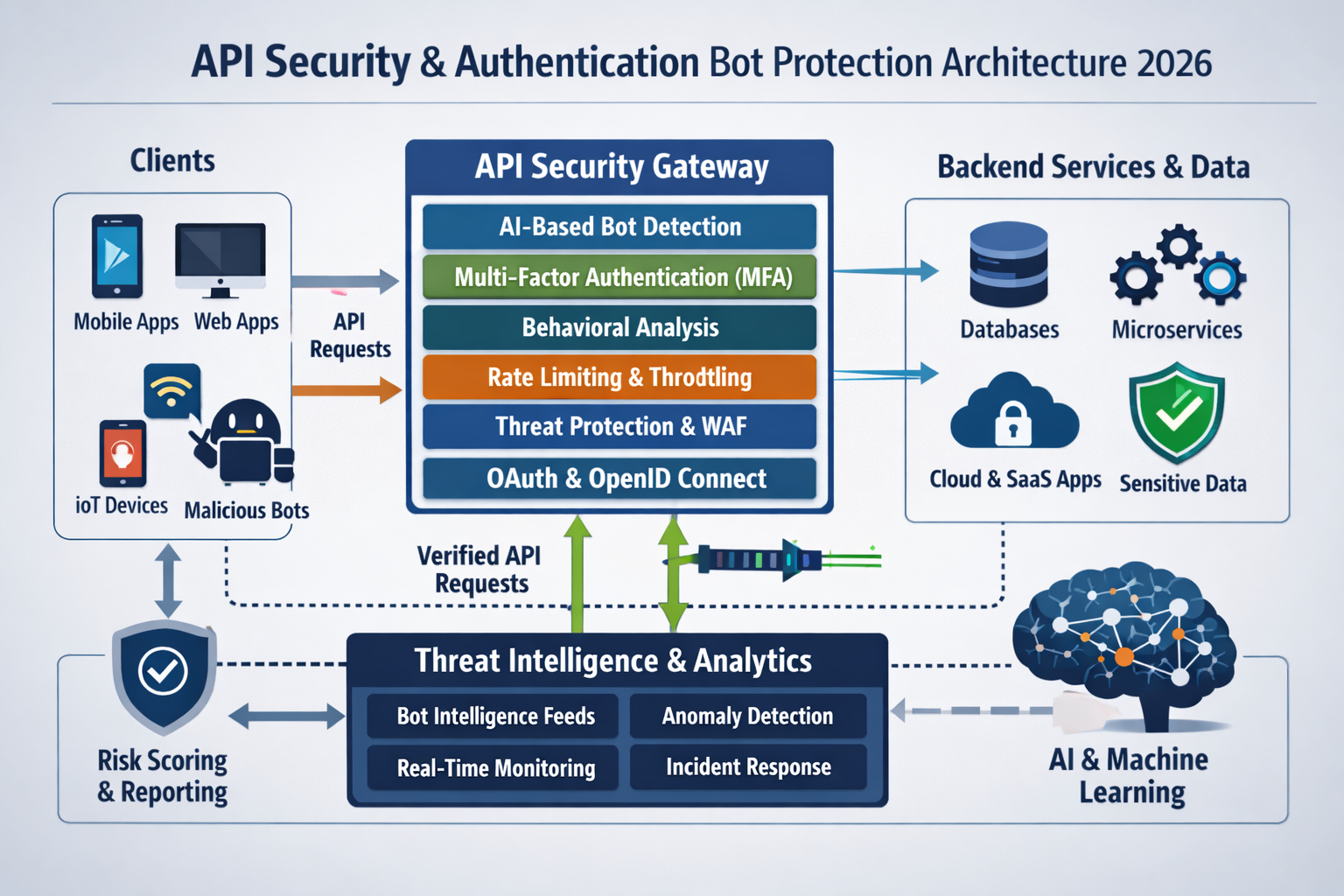
In 2026, API security authentication and bot protection work best as one unified strategy, because most abuse now comes from bots using valid credentials, stolen tokens and business-logic gaps rather than simple network exploits. Modern teams in the US, UK, Germany and the wider EU need a single control plane that ties OAuth2/OIDC, zero-trust authorization and machine-learning-based bot detection together across web, mobile and partner APIs.
Modern APIs don’t just power your mobile app or partner integrations they are your business. In 2026, API security authentication and bot protection can’t sit in different silos, because bots now abuse “legitimate” sessions, tokens and flows more than they attack raw network edges.
This guide walks security architects and platform teams through how to design unified API security authentication and bot protection for US and EU environments, from OAuth2/OIDC patterns to WAAP and dedicated bot platforms.
Today, APIs already account for roughly 70% of all web traffic, and that share keeps rising.At the same time, bad bots make up around one-third or more of total internet traffic, with AI-driven bots growing fastest. In that world, strong API authentication without good bot defense (or vice versa) is a half-finished job.
Why API Security, Authentication and Bot Protection Must Converge in 2026
Security and platform teams now need one unified control plane where API authentication, authorization and bot mitigation work together, because bots increasingly abuse valid credentials and business-logic flows rather than simple network edges. If your login is bulletproof but your account-recovery or coupon APIs are exposed, automated abuse will still win.
How API traffic evolved.
API traffic has shifted from browser-centric page loads to API-first, multi-channel patterns: SPAs, mobile apps, partner integrations and machine-to-machine automation. In 2023, one major study found about 71% of all web traffic was API calls, and another shows APIs comprise well over half of all internet traffic.
For a fintech in New York or a B2B SaaS scale-up in San Francisco, that means:
Billions of API calls across web, mobile and partner channels
JWT/OAuth tokens crossing multiple networks and regions
Attackers focusing on logic flows like “quote → bind policy” or “add card → pay”
At the same time, sophisticated headless browsers, emulator farms and AI-driven tools make abusive traffic look more “human” than ever.
Where siloed auth and separate bot tools leave exploitable gaps
When identity and bot defense run as separate stacks, three gaps appear:
Credential-based bots look legitimate
Bots that pass username/password + MFA sail through pure-auth controls, then hammer password reset, rewards or gift card APIs.
Fraud vs security data lives in different tools
Identity logs, API gateway logs and bot telemetry sit in different silos, making it hard to correlate anomalies in real time.
Inconsistent enforcement across channels
Web login may be protected by a WAAP, while mobile and partner APIs bypass most bot controls. Attackers simply pivot to the weakest channel.
This is why API security posture management, as described by platforms like Wiz, now explicitly includes API discovery, auth risks and runtime attack detection as one continuous problem.
Business impact for US, UK, Germany and wider EU enterprises
For enterprises in the United States, United Kingdom, Germany and the broader EU, converging API security authentication and bot protection is no longer just a “nice to have”:
Direct financial loss
The global average cost of a data breach reached around USD 4.88M in 2024, with financial services even higher. Credential-stuffing and account takeover (ATO) drive a large share of that.
Regulatory exposure
GDPR/DSGVO, UK-GDPR, PSD2/Open Banking, HIPAA and PCI DSS all expect strong authentication, fine-grained access control and adequate monitoring of abuse.
Operational disruption
Bots can saturate pricing, booking or FHIR healthcare APIs, degrading performance for real users and risking SLAs.
Boards increasingly want consolidated dashboards: “How many credential stuffing attempts did we block this quarter?” and “What’s our API security posture across clouds?” Siloed tools make those questions painful to answer.
Core Concepts API Security, Authentication, Authorization and Bot Protection
API security combines robust authentication and authorization with protections against abuse patterns like credential stuffing, scraping and fraud. Bot protection adds behavioral and ML-based analysis so you can distinguish real users from automated traffic even when credentials look “valid.” Before you choose vendors, you need a shared language.
API security vs traditional web application security
API security focuses on machine-to-machine traffic, identity tokens and business logic, while web app security is often page- and session-centric. Traditional WAF rules match signatures on HTTP requests to HTML pages. API security cares about
JSON or GraphQL payloads
Resource identifiers (IDs) and object-level access
OAuth2 scopes and client identities
Sequencing of calls (e.g., cart → checkout → refund)
This is why the OWASP API Security Top 10 2023 highlights risks like broken object-level authorization (BOLA), broken authentication and unrestricted resource consumption as top concerns.
Authentication, authorization and identity for APIs
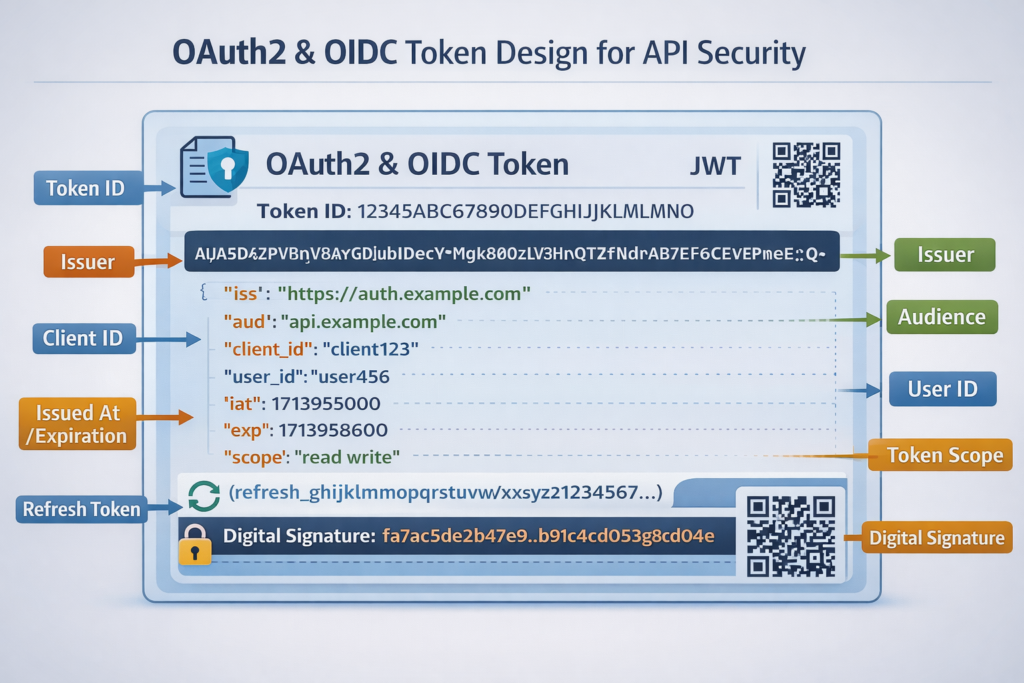
For APIs, authentication and authorization usually build on OAuth2 and OpenID Connect (OIDC)
Authentication
Proving who or what is calling (users, services, devices). Often via OIDC login that issues ID tokens and access tokens.
Authorization
Controlling what they can do: scopes, roles, attributes and policies enforced at the API gateway, WAAP or service layer.
Tokens
JWT vs opaque tokens, access vs refresh tokens, short lifetimes, rotation and revocation.
Identity providers and API gateways increasingly integrate with dedicated API security posture management tools so you can see misconfigured scopes, long-lived tokens or exposed admin interfaces across clouds.
What is API bot protection and which attacks it stops in 2026
API bot protection is a layer of controls signals, models and policies designed to detect and block automated abuse of APIs in real time. In 2026, effective API bot protection typically stops.
Credential stuffing & ATO
Bots replay leaked username/password pairs at scale.
Account takeover & session hijack
Abuse of password reset, OTP and token refresh flows.
Scraping
Competitive price scraping, fare scraping, content theft and LLM training crawlers.
Card testing & payment fraud
Small-value or $0 authorization attempts across payment APIs.
Fake sign-ups & promo abuse
Synthetic identities farming coupons, trials or gift cards.
Inventory hoarding
Bots holding carts, gaming ticketing and inventory APIs.
Vendors like Cloudflare, Imperva, DataDome and F5 now offer ML-based bot detection tuned for APIs, mobile and web together, not just browser pages.
Designing Strong API Authentication for a Bot-Hostile Internet
OAuth2/OIDC and token design for modern API authentication
Start with standards: OAuth2 for authorization, OIDC for login, and a clear token strategy.
Access vs refresh tokens
Short-lived access tokens and longer-lived refresh tokens with rotation and revocation.
JWT vs opaque tokens
JWTs improve performance (self-contained claims) but must be signed, short-lived and carefully scoped; opaque tokens push validation to your auth server or introspection endpoint.
Audience and resource servers
Ensure tokens are audience-bound, so a token for “payments-api” can’t be replayed against “admin-api.”
Key rotation
Use JWKS endpoints and automated rotation to prevent key compromise from becoming a long-lived incident.
Tools like Curity and cidaas specialize in OAuth2/OIDC for APIs, including PSD2/Open Banking-grade profiles.
Hardening login and machine-to-machine auth against credential stuffing
To resist credential stuffing and ATO, design authentication assuming bots will reach valid credentials.
Risk-based authentication
Factor in device, IP/ASN reputation, geolocation and behavior before deciding on MFA.
Step-up MFA
Require extra verification for high-risk actions (new device, large transfer, password change)
Device binding
Bind tokens to device fingerprints or secure elements for mobile apps.
mTLS for service-to-service
For machine-to-machine APIs, use mutual TLS plus client credentials and rotate certificates frequently.
IP/ASN reputation as a signal, not the gate
Use IP intelligence as just one input into behavioral models, not the sole control.
This is also where “how to combine OAuth2 and bot detection for public APIs” becomes concrete: feed auth events and token metadata into your bot platform so it knows which sessions and flows to treat as high risk.
Zero-trust principles for public, partner and internal APIs
Zero trust means “never trust, always verify and for APIs that translates into.
Micro-segmentation
Group APIs by sensitivity and business domain, not just network.
Least-privilege scopes
Keep scopes narrowly aligned to specific APIs and actions.
Per-API client IDs
Give each mobile app, partner integration or backend job its own client ID and policy.
Continuous session risk evaluation
Adjust friction (challenges, MFA, throttling) as risk changes over the life of a session.
In practice, this creates a foundation where bot protection policies can align neatly with identity: you can challenge an API client because its behavior deviates from normal for its scope, not just because its IP “looks bad.”
API Bot Protection and Mitigation Strategies that Actually Work
Effective API bot protection layers basic controls like rate limiting and IP reputation with device fingerprinting, behavioral anomaly detection and challenge/response flows that are tuned for APIs rather than only web pages. Point solutions that only look at IPs or user agents will miss modern AI-enabled bots.
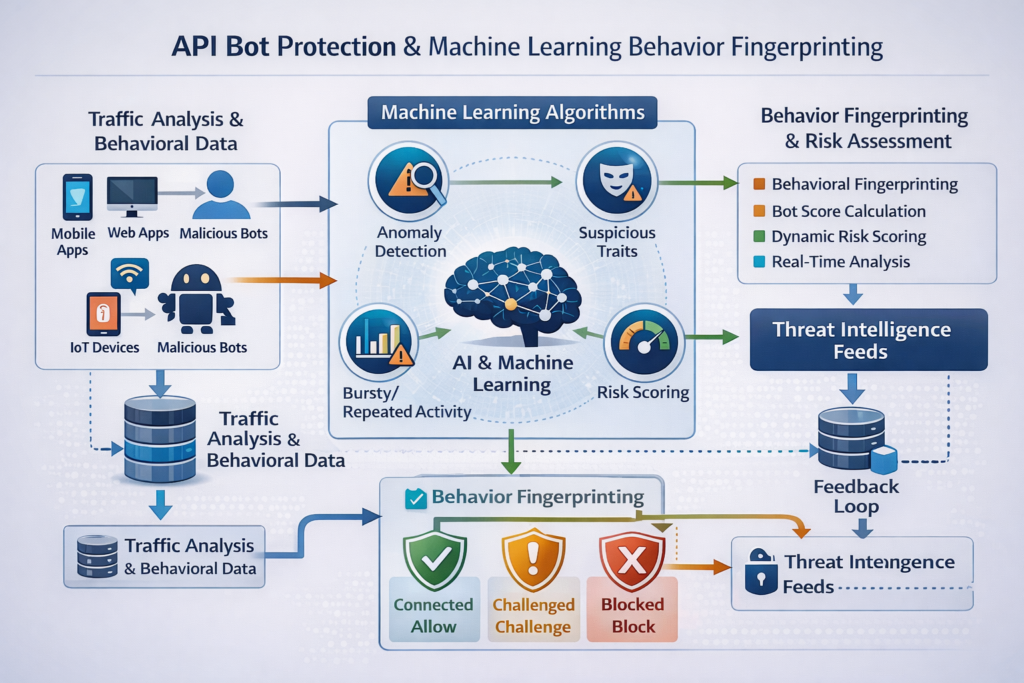
From rate limiting to behavioral ML.
Think of bot defense as concentric rings.
Baseline controls
Rate limiting, sliding-window throttling, per-API quotas and schema validation.
Reputation & lists
Dynamic allow/deny lists, ASN/hosting-provider intelligence, known-good partners.
Device & behavior fingerprinting
TLS fingerprints, client hints, mobile device signals and sequence-of-calls analysis.
Machine-learning anomaly scoring
Models trained on “normal” vs “abusive” API usage for credential stuffing, scraping and card testing.
Platforms like Radware, Akamai and Indusface use ML and behavior analytics to mitigate large-scale bot attacks without crushing real users.
Protecting login, scraping-sensitive and payment APIs
Focus your strongest defenses on high-risk endpoints.
Login & auth APIs
Tie risk-based auth, step-up MFA and bot scoring together; start with shadow-mode policies, then move to blocking.
Scraping-sensitive APIs
Pricing, inventory, quote and content APIs; combine behavior fingerprinting with IP reputation for API traffic so you’re not blocking CDNs or mobile carriers blindly.
Payment & card APIs
Use velocity checks per card, per IP, per device, plus 3-D Secure and issuer-side SCA where applicable.
These patterns apply across REST, GraphQL, mobile backends and partner APIs. For example, a travel platform in London might put stricter anomaly detection on fare-quote APIs and checkout routes than on low-risk public content.
Detection, response and reducing false positives in bot mitigation
Bot defenses fail when they either miss attacks or constantly block real users. To keep a good balance:
Shadow mode first
Deploy policies in “monitor-only” mode to understand impact and tune thresholds.
Fraud & SRE collaboration
Involve fraud, product and SRE teams in reviewing detections and business impact.
Multi-outcome policies
Use graduated responses: log-only → challenge → throttle → block.
UX-aware challenges
Prefer friction-light challenges for high-value actions and avoid blanket CAPTCHAs.
Vendors like DataDome emphasize low-latency, high-accuracy detection across web, mobile and APIs specifically to reduce false positives at scale.
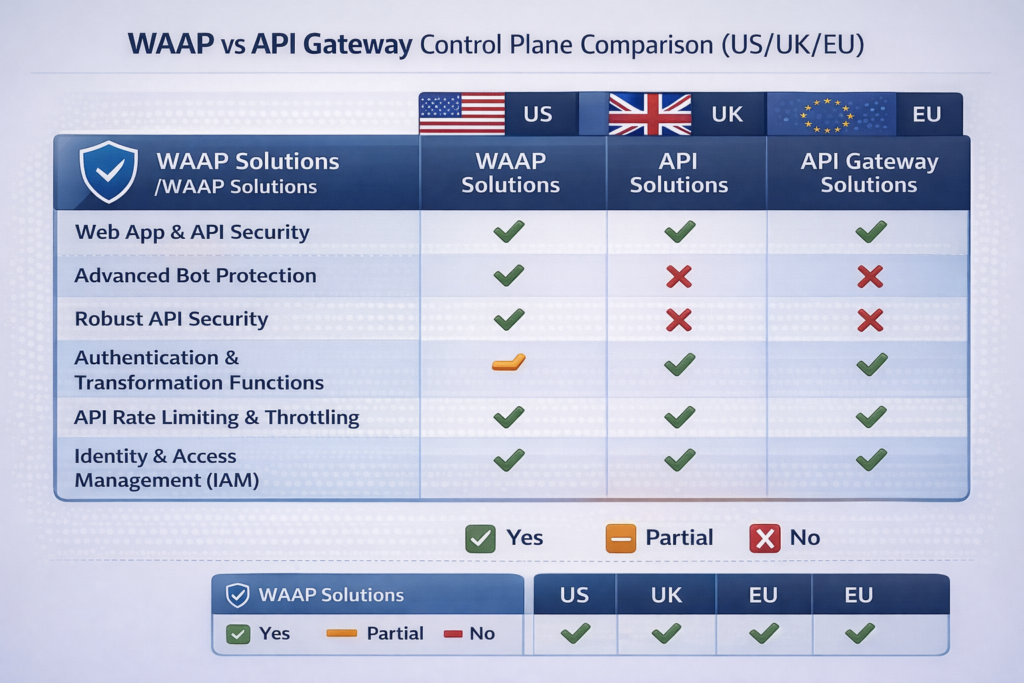
WAAP, WAF and API Gateways Choosing the Right Control Plane
Most organizations combine an API gateway for routing and policy with a WAAP or WAF + bot management layer; the right mix depends on how much you need managed detection, ML-based bot defense and global edge presence. Your goal is a single logical control plane, even if it spans multiple products.
API gateway security vs WAAP vs legacy WAF
High level
API gateway
Great for routing, authentication/authorization enforcement, schema validation and per-service policy. Often deployed near your microservices.
WAAP (Web App & API Protection)
Combines WAF, API security and bot management, often as a cloud-managed edge service (e.g., Cloudflare, F5, Imperva, Akamai).
Legacy WAF
Signature-focused, often lacking deep API understanding or advanced bot detection.
For API-heavy architectures, a typical pattern is: API gateway for auth and routing, WAAP for threat protection and bot mitigation, and a dedicated bot platform if attacks or complexity outgrow built-in features.
When to add dedicated bot management on top of WAAP
Signals that your WAAP/WAF rules are no longer enough.
Regular high-volume credential stuffing despite rate limits
Attacks using headless browsers and mobile emulators that bypass simple checks
Fraud teams reporting ATO or promo abuse that doesn’t show up clearly in security dashboards
Need for machine-learning-based bot detection for APIs across multiple regions and clouds
That’s when dedicated bot solutions like DataDome or Indusface, integrated with WAAP and gateways, make sense. They provide richer behavior models, agent and LLM-aware controls and better reporting for fraud and risk teams.
CDN-based API security and regional deployments (US, UK, Germany/EU)
For global APIs, geography matters
Data residency
German and broader EU clients often prefer inspection and logging in EU-only PoPs (e.g., Frankfurt, Amsterdam) to support GDPR/DSGVO expectations.
Latency
Terminating TLS and enforcing auth as close as possible to users in regions like Berlin, London or New York reduces round trips and improves UX.
Control placement
One practical model is: TLS termination and basic bot filtering at the CDN/WAAP edge, then fine-grained auth and authorization at the API gateway inside each region.
Regulators and auditors will ask where packets are terminated, where logs land and how cross-border transfer is controlled, particularly for EU data subjects.
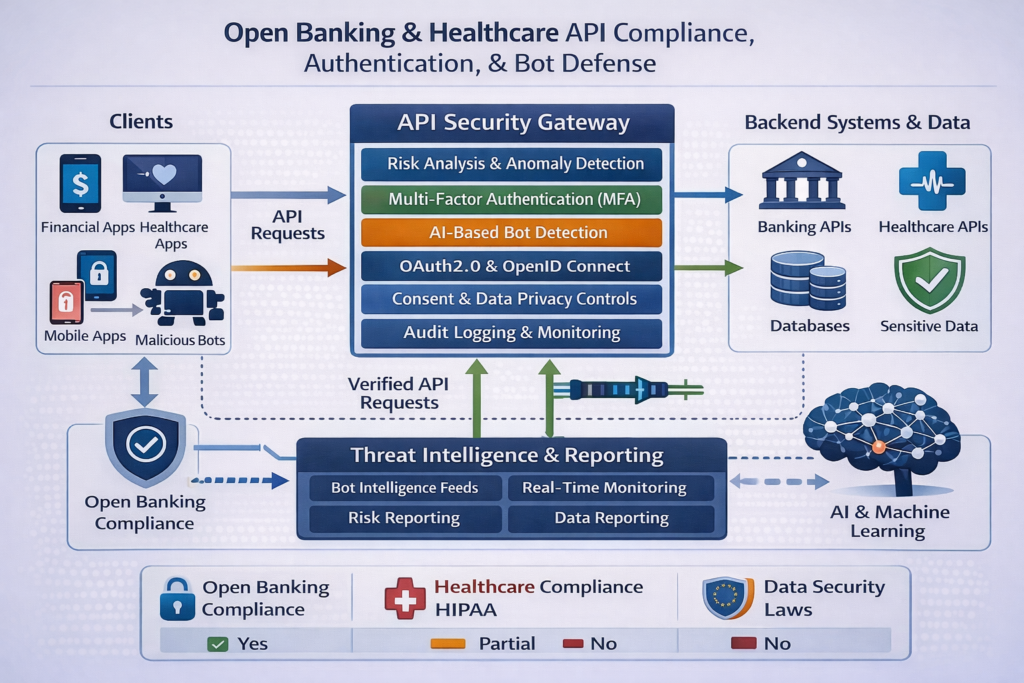
Regulated Industries Open Banking, Healthcare and EU/UK Compliance
Regulations like PSD2, GDPR/DSGVO, UK-GDPR, HIPAA and PCI DSS push organizations toward stronger API authentication, Strong Customer Authentication (SCA) and careful logging/telemetry for bot detection without over-collecting personal data.
This article is general information, not legal or compliance advice always review regulatory requirements with your legal and compliance teams.
How PSD2, Open Banking and BaFin guidance shape API controls
For banks and fintechs in the EU and UK, PSD2 and Open Banking require.
SCA
Two or more factors, often step-up MFA tied to risk and transaction value.
Fine-grained consents
Tokens scoped to specific accounts and permissions.
Strict throttling and monitoring
Account information and payment initiation APIs must have abuse-resistant rate limits.
German players often lean on platforms like BaFin guidance and vendors such as Airlock or cidaas for open banking API authentication and bot defence requirements in the UK and DACH markets.
Designing HIPAA- and PCI-ready API authentication and logging
In US healthcare and payments:
Minimum necessary data
Tokens and logs should contain only what’s necessary for auth, debugging and fraud detection; avoid dumping PHI or full card numbers into traces.
Encrypted tokens and channels
TLS everywhere, plus at-rest encryption for tokens and session stores.
Audit trails
Immutable logs of access decisions, failed and successful auth, policy changes and bot mitigation events.
Separated telemetry streams
Keep fraud/bot telemetry logically separate from PHI to simplify HIPAA scoping.
Card brands and PCI DSS also expect robust rate limiting and anomaly detection on cardholder data environments perfect candidates for integrated auth + bot controls.
GDPR/DSGVO and UK-GDPR constraints on bot detection and telemetry
For EU and UK teams, the question is often: what telemetry can we collect for bot detection while staying compliant? Consider:
IP address handling
Treat IPs as personal data; consider hashing or truncation where possible.
Retention limits
Keep detailed request-level data for the shortest feasible period, then aggregate.
Consent and transparency
Explain security/fraud detection logging in privacy notices; use banners wisely.
Pseudonymized identifiers
Use pseudonymous IDs in behavior fingerprinting, rather than directly storing user identifiers or device IDs.
Many German buyers explicitly look for “DSGVO konforme API Security Authentifizierung und Bot Schutz” in vendor proposals privacy by design is a feature, not a constraint.
Regional Playbooks US, UK and Germany/EU API Auth + Bot Protection Patterns
United States: high-volume APIs, vertical regs and dedicated bot budgets
In the US, fintech, ecommerce and B2B SaaS APIs often prioritize.
Tight alignment with HIPAA, PCI DSS and GLBA where applicable
High-volume, multi-cloud deployments with regional PoPs in cities like New York and San Francisco
Dedicated bot budgets for ATO prevention, card testing and promo abuse
Buyers here often shortlist WAAP + bot platforms from Cloudflare, F5, Imperva and Akamai, and evaluate how well they integrate with identity, SIEM and fraud tools.
United Kingdom.
In the UK, open banking standards and NHS FHIR APIs shape expectations.
PSD2/Open Banking-compliant OAuth flows with SCA built in
High-availability consent and token introspection endpoints
Bot detection that protects login and account information APIs without breaking third-party provider flows
For healthcare, the NHS open APIs rely on strong client authentication, certificate pinning and strict rate limiting to preserve clinical capacity.
Germany/EU.
Germany and wider EU markets often show:
Preference for EU-based WAAP and logging stacks
Careful scrutiny of cross-border data transfer and “US person access” to logs
Strong emphasis on documented DPIAs, joint-controller agreements and auditability
Local or EU-focused vendors like DataDome and Airlock, combined with regional PoPs in Frankfurt and other EU hubs, can help meet these expectations.
Evaluation Checklist and Roadmap for Unified API Authentication and Bot Protection
Teams should evaluate solutions on coverage of OWASP API risks, depth of bot detection, integration with identity providers and API gateways, compliance fit and the ability to roll out controls in phases without breaking critical APIs.
Key questions to ask WAAP, API gateway and bot protection vendors
When you’re comparing WAAP, gateways and bot platforms, ask.
Coverage
Which OWASP API Security Top 10 and bot attack types do you detect natively?
ML transparency
How are models trained? Can we see features or at least explainability at a high level?
Latency impact
What’s the typical added latency at p95 for API traffic by region?
False-positive handling
Can we run policies in monitor mode, simulate changes and roll back quickly?
Data residency & privacy
Where do logs live? How is personal data handled for GDPR/DSGVO and UK-GDPR?
Security posture
SOC 2, ISO 27001, independent pen tests, API security posture management capabilities.
Use guidance from players like Wiz on API-SPM to frame these questions around continuous risk posture rather than one-off configuration.
Phased rollout plan for US, UK and EU teams
A pragmatic rollout you can present as a how-to.
Discover & prioritize APIs
Inventory public, partner and internal APIs; map high-risk endpoints (login, payments, quotes, sensitive data)
Enable observability
Turn on detailed logging in gateways, WAAP and bot tools; centralize into SIEM/observability platforms.
Deploy in monitor (shadow) mode
Integrate WAAP and bot protection, but start with logging-only policies on key flows.
Tune with fraud/security feedback
Review findings weekly with fraud, SRE and product teams; adjust rules, thresholds and challenges.
Tighten & expand coverage
Move critical APIs to blocking mode, then expand across regions and partners, keeping a clear rollback plan.
This approach works equally well for a healthtech startup in Austin or a regulated bank in Berlin.
KPIs, dashboards and executive reporting for API security
To keep executives engaged, define a simple KPI set, for example.
Time-to-detect API abuse From attack start to detection.
Blocked credential-stuffing attempts Aggregated per month, by region and channel.
Fraud loss avoided Estimate based on blocked attacks vs historical baseline.
Latency & availability SLOs Impact of security controls on p95 latency and uptime.
Audit/compliance metrics Coverage of OWASP API risks, SCA adoption, log retention and DPIA completion.
Dashboards should be shareable at CISO, engineering and fraud levels with drill-down into specific APIs and regions.
Key Takeaways
APIs now dominate internet traffic, and bots account for a growing share of abuse so API security authentication and bot protection must be designed together, not bolted on separately.
Strong OAuth2/OIDC, zero-trust scopes and token design are the foundation; machine-learning-based bot detection and behavior fingerprinting sit on top.
WAAP + API gateways give you a practical control plane; dedicated bot management comes into play once you face high-volume or highly evasive attacks.
Regulated sectors (open banking, healthcare, payments) in the US, UK and EU must balance SCA, HIPAA/PCI DSS logging and GDPR/DSGVO-friendly telemetry.
Regional patterns differ: US teams often lead on scale and budget, UK on open banking patterns, and Germany/EU on privacy and data residency discipline.
A phased rollout discover, monitor, tune, then block lets you adopt unified API auth and bot defense without breaking critical customer journeys.
If you’re planning an API-heavy roadmap and want a second pair of eyes on your API security authentication and bot protection strategy, the team at Mak It Solutions can help you design a unified control plane across gateways, WAAP and bot platforms. We work with fintech, ecommerce, healthcare and B2B SaaS teams across the USA, UK, Germany and wider Europe on secure, scalable API architectures.
Share your current stack, regulatory requirements and key APIs, and request a scoped architecture review or security workshop. Together, we can map a practical 90-day plan to harden auth, reduce bot abuse and keep your business-critical APIs fast and secure.( Click Here’s )
FAQs
Q : Is OAuth2 alone enough to protect public APIs from sophisticated bots?
A : No OAuth2 alone is not enough to protect public APIs from sophisticated bots. OAuth2 and OIDC give you a solid framework for authentication and authorization, but bots can still steal, replay or brute-force tokens and credentials. To protect public APIs, you should combine OAuth2 with bot detection that monitors behavior, device fingerprints and anomaly patterns across login, account and payment flows. Rate limiting, mTLS, IP/ASN intelligence and continuous token risk evaluation should all work together as part of a unified control plane.
Q : Do I still need CAPTCHAs if I deploy dedicated API bot protection?
A : In many cases, dedicated API bot protection significantly reduces your reliance on CAPTCHAs, but doesn’t remove them entirely. Modern bot platforms can challenge suspicious traffic with behind-the-scenes signals and lightweight friction, so only a small percentage of users see visible challenges. For high-risk actions, a well-placed CAPTCHA or step-up MFA can still be useful, especially when combined with behavior-based scoring. The goal is to reserve CAPTCHAs for truly risky edge cases, not to blanket every login or checkout with puzzles.
Q : How can small teams add bot mitigation on top of an existing API gateway without a full re-architecture?
A : Small teams can usually integrate bot mitigation incrementally at the edge or gateway layer. Start by enabling WAAP or bot features from your existing cloud provider or CDN, pointing it at your current gateway without changing backend services. Run policies in monitor mode first, review false positives, then move selected APIs like login or payments to blocking mode. Over time, you can forward bot telemetry to your SIEM, add risk-based auth signals into your identity provider and only later consider dedicated bot platforms if attack volume or complexity justifies it.
Q : What telemetry should we collect to detect API abuse while staying GDPR/DSGVO compliant?
A : To stay GDPR/DSGVO compliant while detecting API abuse, focus on proportional, pseudonymized telemetry. Collect request metadata like endpoint, method, timestamp, response codes, IP (possibly truncated or hashed), user agent, device fingerprints and token-related attributes (scopes, client IDs) rather than full personal data. Limit retention windows for raw logs, aggregate where possible and clearly describe security/fraud detection logging in your privacy notices. For EU and UK users, you may also need to document this processing in your DPIAs and ensure that any cross-border log transfers rely on valid transfer mechanisms.
Q : How do we benchmark different WAAP and bot management vendors for latency, accuracy and data residency?
A : To benchmark WAAP and bot vendors, design a short proof-of-concept that mimics your real traffic and regulatory constraints. Measure added p95 and p99 latency in regions where you operate, using synthetic and real-user monitoring on critical APIs. Compare detection accuracy by replaying known attack samples or using red-team exercises, and track false positives in monitor mode. For data residency, review where traffic is terminated, where logs are stored, which sub-processors are involved and how each vendor supports GDPR/DSGVO, UK-GDPR and sector-specific rules like HIPAA or PCI DSS. Document these findings in a simple scorecard for stakeholders.


