EDR for Small Business in the GCC (Practical Setup Guide)
EDR for Small Business in the GCC (Practical Setup Guide)

EDR for Small Business in the GCC (Practical Setup Guide)
Endpoint Detection and Response (EDR) for small businesses in the GCC is a modern endpoint security approach that continuously monitors laptops, desktops, and servers for suspicious behaviour and automatically contains attacks like ransomware. For Saudi, UAE, and Qatar SMEs, EDR for small business in the GCC helps protect remote and office workers, supports alignment with NCA, SAMA, TDRA and NCSA expectations, and keeps endpoint security manageable for small IT teams.
Why EDR Matters for Small Businesses in the GCC Today
EDR for small business in the GCC is no longer “nice to have”; SMEs in Saudi Arabia, the United Arab Emirates, and Qatar are now prime targets for ransomware and credential theft, especially in fintech, logistics, e-commerce, and health. In the UAE alone, almost three-quarters of organisations were hit by ransomware attacks between 2021 and 2023, with many of those victims being SMEs, not just large enterprises.
“We’re Too Small to Be Hacked” The Risk for GCC SMEs
Many founders in Riyadh, Dubai, or Doha still assume attackers only care about banks and telcos. In reality, automated phishing, credential stuffing, and remote-desktop attacks hit any exposed endpoint, especially where basic antivirus and weak passwords are still in place. Qatar’s SME cyber-security manual, developed by Qatar Development Bank and the National Cyber Security Agency, explicitly warns that small businesses are heavily targeted and need baseline technical controls on endpoints.
How Remote Work and Cloud Tools Changed Endpoint Risk in Saudi, UAE, and Qatar
Today your “office” includes laptops at home in Jeddah, a MacBook in a Dubai co-working space, and a Windows server in an AWS Bahrain or Azure UAE Central region. With staff logging into SaaS tools, banking portals, UAE Pass, and internal apps from everywhere, the endpoint has become the easiest way around your firewalls. EDR adds real-time endpoint threat detection and response so you can spot suspicious remote access, lateral movement, and data exfiltration before it becomes a breach.
What You’ll Learn in This EDR Setup Guide
This guide walks small IT teams through how to plan an EDR rollout, deploy agents step-by-step to laptops and servers, tune noisy alerts, align with NCA, SAMA, TDRA, NDMO, QCB and NCSA expectations, and decide when to bring in a SOC-as-a-service partner. The focus stays realistic for about 20–100 endpoints spread between Saudi Arabia, the United Arab Emirates, and Qatar.
What is EDR and How Is It Different from Traditional Endpoint Security for Small Businesses in the GCC?
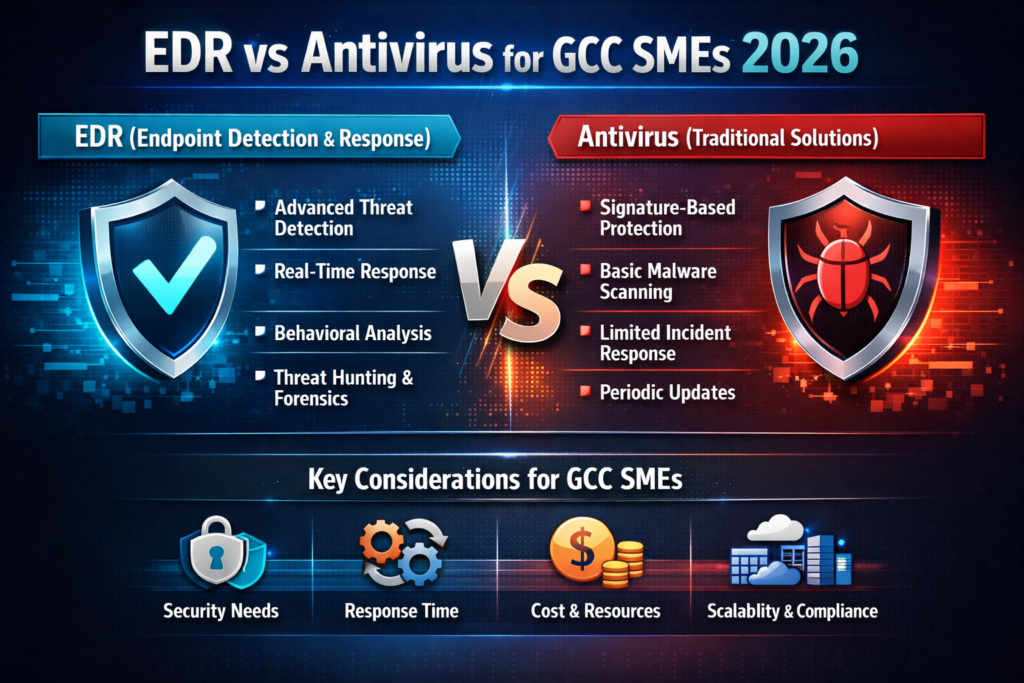
For GCC SMEs, EDR is a “next-gen antivirus and EDR” platform that continuously monitors endpoints, detects abnormal behaviour, and helps you investigate and contain attacks, not just block known malware. Traditional antivirus mainly looks for known signatures, while EDR gives you real-time endpoint monitoring for SMEs, attack timelines, and response actions (like isolating a laptop) that your small team can run with a few clicks.
Simple Definition: Endpoint Detection and Response for SMEs
In simple terms, EDR is software you install on laptops, desktops, and servers that watches processes, network connections, and user actions, and raises high-quality alerts when something looks like an attack. For a 40-person company in Riyadh, that means seeing when an employee’s device suddenly runs PowerShell scripts, talks to suspicious IPs, or encrypts files like ransomware.
EDR vs Antivirus vs Legacy Endpoint Security for GCC Small Businesses
Legacy antivirus focuses on scanning files; old endpoint suites often bolt on basic firewall and device control. EDR adds behaviour-based analytics, threat hunting, and response playbooks. For a small business in Dubai or Abu Dhabi, that can be the difference between:
Generic “virus blocked” notifications you never read, and
A clear investigation view that shows which user clicked a phishing link, which endpoints were touched, and lets you quarantine them in seconds.
When Does a Small Team in Riyadh, Dubai, or Doha Actually Need EDR?
Clear triggers include.
Remote or hybrid work
Handling payment or open-banking data
Storing health or sensitive customer data
Being regulated by SAMA, QCB, or UAE free-zone regulators
Once you’re beyond roughly 20 endpoints, or working towards frameworks like SAMA’s Cyber Security Framework or NCA Essential Cybersecurity Controls, EDR is the practical way to prove you can detect and respond to attacks, not only install antivirus.
How Small IT Teams in the GCC Should Plan an EDR Rollout
How Many Laptops, Desktops, and Servers Need EDR?
Start with a simple spreadsheet covering:
User
Device type
OS
Location (Riyadh, Jeddah, Dubai, Abu Dhabi, Doha)
Business role
Include on-prem Windows servers and any cloud VMs in AWS Bahrain, Azure UAE Central, or GCP Doha, because ransomware protection for laptops and servers should sit under one view.
Map Users and Critical Workloads Across Saudi, UAE, and Qatar Offices
Prioritise finance, operations, and engineering devices, plus endpoints accessing banking portals, Open Banking Framework APIs, or government systems. In a Riyadh fintech, for example, developer laptops that touch SAMA-regulated systems should be in the first EDR wave.
In-House EDR Management or Managed EDR Service?
If your IT “team” is one admin juggling helpdesk and projects, running a full 24/7 SOC is unrealistic. Many GCC startups now combine an in-house EDR platform with a managed EDR or SOC-as-a-service for after-hours alert triage and incident response, especially in fintech and health where downtime is expensive.
How Can a Small IT Team Set Up EDR Step-by-Step on Laptops and Servers in the GCC?
Choose an EDR, Create Admin Accounts, and Define Basic Policies
Shortlist vendors that support data residency in GCC or nearby regions, Arabic-friendly interfaces, and integrations with your M365/Google Workspace. Create admin roles with least privilege, define baseline policies (for example: block known ransomware, flag privilege escalation, restrict risky scripts), and plan pilot groups per country.
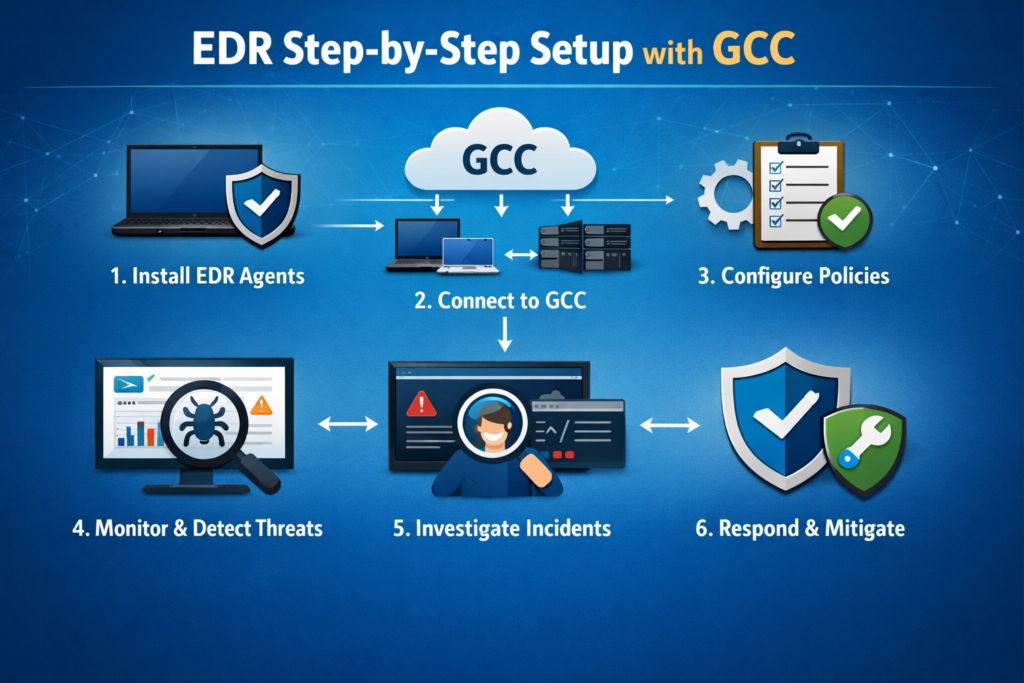
Install EDR Agents on Pilot Devices in Riyadh, Dubai, and Doha
Roll out agents to 5–10 devices per location: one finance laptop, one developer machine, an operations PC, and at least one server. Validate that alerts arrive, that remote isolation works over local ISPs, and that there’s no major performance impact in day-to-day work.
Push EDR to All Endpoints and Verify Coverage for Remote Teams
Once pilots are stable, deploy via your MDM/AD tools or simple install packages for remote staff. Check coverage dashboards to ensure every active device in Saudi Arabia, the UAE, and Qatar is reporting. Run a controlled test (for example, a benign EICAR file or simulated phishing) to confirm alerts and your response process actually work.
What EDR Settings Should Saudi and UAE SMEs Change First to Reduce False Alerts?
Ransomware, Privilege Misuse, and Suspicious Remote Access Rules
Focus your “high” severity rules on behaviours that really matter: mass file encryption, credential dumping, new local admins, and unusual RDP/SSH from the internet. This aligns neatly with NCA’s Essential Cybersecurity Controls and SAMA’s risk-based approach for financial entities.
Turn Off or Tune “Chatty” Low-Risk Alerts for Small Security Teams
Disable or downgrade noisy alerts like every single USB insert, benign script execution, or repetitive software updates. For a busy IT lead in Dubai, it’s better to receive 10 high-quality alerts per week than 500 “informational” ones that will simply be ignored.
Simple EDR Playbooks for Small IT Teams Without a Full SOC
Document two or three lightweight playbooks such as:
Suspicious login
Possible ransomware
Malicious file
Each should list: isolate device, reset accounts, collect EDR timeline, decide whether to wipe/rebuild, and when to inform management or your managed EDR partner.
How Does EDR Help Small Businesses Meet Local Cybersecurity and Data-Residency Rules in the GCC?
Saudi Arabia: Aligning EDR with NCA, SAMA, and NDMO Expectations
NCA’s Essential Cybersecurity Controls and newer private-sector controls require organisations to detect, respond to, and report cyber incidents; EDR is a practical way to evidence those capabilities on endpoints. For SAMA-regulated banks, fintechs, and open-banking participants, EDR supports the Cyber Security Framework by providing monitoring, incident handling, and audit trails on all devices touching regulated systems.When you store logs in GCC cloud regions and apply National Data Management Office (NDMO) classification and retention policies, EDR becomes a strong part of your compliance story.
UAE: TDRA, ADGM, and DIFC Endpoint Security Expectations for SMEs
The UAE National Cybersecurity Strategy and Information Assurance Regulation emphasise minimum security controls across public and private entities, including logging and incident response on critical systems. For free-zone companies in ADGM or DIFC handling financial and personal data, EDR on office and remote endpoints reinforces their own data-protection regimes and helps prove “appropriate technical measures” in audits.
Qatar: QCB, NCSA, and Sovereign-Cloud Considerations for EDR Logs
In Qatar, the National Cyber Security Agency leads the national cyber strategy, and QCB-regulated financial institutions are under pressure to harden endpoints and monitoring.SMEs can follow the QDB/NCSA Cyber Security Manual for SMEs and keep EDR telemetry in GCC or local regions such as GCP Doha or AWS Bahrain, applying encryption and strict access controls to respect Qatar’s data-protection expectations.

How to Choose the Right EDR or Managed EDR Service for Small Businesses in Saudi, UAE, and Qatar
Key Features Small GCC Teams Should Look For in an EDR Platform
Look for.
Strong ransomware protection for laptops and servers
Behavioural analytics and easy investigation timelines
Built-in playbooks for common incidents
Integration with email and collaboration tools
For GCC SMEs, Arabic-capable dashboards and local MSSP partners are a big plus.
Cloud EDR vs On-Prem EDR vs Local GCC Data Centers
Cloud-hosted EDR is usually easiest for small teams, but you should confirm where telemetry is stored and whether GCC data centres (AWS Bahrain, Azure UAE Central, GCP Doha) are supported. Highly regulated Saudi or Qatar workloads may prefer vendors that can commit to regional or sovereign-cloud storage plus strong encryption.
Cost Expectations for EDR for 20–100 Endpoints in KSA, UAE, and Qatar
Most vendors price per endpoint per month. For a 50-employee company in Riyadh or Jeddah on a limited budget, start with core EDR plus a light managed-service tier rather than a full enterprise SOC. Compare that to your risk: a single ransomware incident can easily exceed the annual cost of a low-cost EDR service in Qatar or the UAE once downtime and recovery are included.
Running EDR Day-to-Day with a Small IT Team in the GCC
Daily and Weekly EDR Checks a Small Team Can Actually Commit To
A realistic routine.
Daily: review new high-severity alerts and confirm any isolated endpoints.
Weekly: check coverage (no “offline” agents), review policy changes, and export a short report for management, especially in regulated sectors like fintech and logistics.
When to Escalate to a Managed EDR or SOC-as-a-Service Partner
If you see recurring targeted attacks, cannot respond 24/7, or must comply with frameworks like SAMA CSF, NCA ECC, or QCB/NCSA expectations, consider a managed EDR partner. They can watch alerts overnight and coordinate with your team during working hours.
Building a Simple Incident-Response Plan Around Your EDR
Create a one-page incident-response (IR) plan covering: who leads incident handling, who talks to regulators or banks, which systems are “crown jewels,” and what thresholds require external legal, PR, or regulator notification. Test it with a tabletop exercise once or twice a year so the team knows what to do before a real incident hits.
From First EDR Pilot to a Secure GCC Small Business
What a Small GCC Business Gains from Proper EDR Setup
With a simple EDR rollout, a Dubai e-commerce brand, a Riyadh fintech startup, or a Doha logistics SME can finally see what’s happening on endpoints, stop live attacks, and produce evidence for auditors and investors. EDR becomes the bridge between policies on paper and real-world detection and response.
When to Bring in a GCC-Based Managed EDR Partner
Bring in a regional partner when alerts outgrow your capacity, when entering regulated markets (for example, Open Banking in Saudi Arabia), or when expanding into multiple offices across the GCC. A local SOC-as-a-service provider understands SAMA, NCA, TDRA, and NCSA language and expectations, which makes audits and incident handling smoother.
EDR Basics, Compliance Deep Dives, and Vendor Comparisons
To go deeper on GCC-ready digital platforms, you can explore Mak It Solutions’ insights on web development trends in the Middle East for KSA & UAE and other compliance-driven tech topics. Their teams can also help connect EDR planning with secure web development services, mobile app development, and modern stacks like Webflow or Wix.

If you’re responsible for IT or security in a Saudi, UAE, or Qatar SME and EDR for small business in the GCC still feels “too enterprise,” this is your moment to change that. Mak It Solutions can help you scope endpoints, shortlist GCC-appropriate EDR platforms, and align setup with local regulations and your real-world budget.
Explore our core services and related digital transformation guidance for regulated markets, or contact us to design a practical EDR and endpoint-security roadmap for your small team.
FAQs
Q : Is EDR mandatory for Saudi SMEs under NCA or SAMA rules?
A : EDR itself is not named as a mandatory product, but its functions continuous monitoring, incident detection, and response map directly to NCA Essential Cybersecurity Controls and newer private-sector controls, which now treat cybersecurity as a baseline requirement for many Saudi businesses, not only critical infrastructure. For financial institutions and fintechs regulated by the Saudi Central Bank (SAMA), the Cyber Security Framework requires robust controls around endpoints, logging, and incident handling; EDR is often the most efficient way for Saudi SMEs to meet those expectations in practice.
Q : Can UAE free-zone companies in ADGM or DIFC keep EDR data inside the UAE?
A : Yes, many EDR vendors can store telemetry and logs in regional cloud regions, including Middle East data centres used by UAE businesses, which helps ADGM and DIFC companies demonstrate appropriate data-protection safeguards. UAE’s National Cybersecurity Strategy and Information Assurance Regulation emphasise strong protection of information assets but do not forbid using cloud services, as long as encryption, access control, and risk management are in place. When choosing an EDR solution, UAE free-zone firms should explicitly ask about data-centre locations, encryption options, and how the vendor supports compliance with their free-zone data-protection rules.
Q : What is the best EDR option for a 50-employee company in Riyadh or Jeddah on a limited budget?
A : For a 50-employee Saudi SME, the “best” EDR option is one that balances strong prevention with simple operations and transparent pricing not necessarily the most feature-rich enterprise tool. In practice, this often means a cloud-delivered EDR with per-endpoint pricing, a basic MDR (managed detection and response) add-on, and integrations into your existing Microsoft or Google stack. Align it with NCA and SAMA expectations by ensuring you can generate incident records, keep logs in GCC or approved regions, and demonstrate basic threat-hunting capability during assessments.
Q : How can a Qatar-based SME ensure EDR logs stay in a local or GCC data center?
A : Qatar-based SMEs should shortlist vendors that offer regional hosting in GCC cloud regions such as GCP Doha or nearby AWS Bahrain and clearly state data-location options in their contracts. This aligns with Qatar’s push for strong cybersecurity under the NCSA and the practical guidance in the QDB/NCSA Cyber Security Manual for SMEs, which urges SMEs to secure cloud usage and protect sensitive data. If a truly local region is not available, combine regional hosting with strong encryption, access control, and documented risk assessments referencing Qatar’s National Cybersecurity Strategy.
Q : Do GCC-based managed EDR services provide Arabic support for dashboards and alerts?
A : Many GCC-based MSSPs and SOC-as-a-service providers now offer Arabic-speaking analysts, bilingual runbooks, and, in some cases, dashboards localised for Arabic-first teams, reflecting the region’s growing cybersecurity and MSSP markets. When evaluating providers, SMEs in Saudi Arabia, the UAE, and Qatar should ask specifically about Arabic alert summaries, training material, and regulator-ready reports that reference NCA, SAMA, TDRA, QCB, or NCSA requirements and national programmes like Saudi Vision 2030 or Qatar National Vision 2030.


