GCC Cybersecurity 2026: Zero Trust & Ransomware
GCC Cybersecurity 2026: Zero Trust & Ransomware
GCC Cybersecurity 2026: Zero Trust & Ransomware
In 2026, GCC cybersecurity for banks, government and critical infrastructure means shifting to Zero Trust, identity-centric security and tested ransomware playbooks aligned with local regulators. For leaders in Saudi Arabia, United Arab Emirates and State of Qatar, winning strategies combine cloud-ready IAM, regional data residency and 24/7 monitoring from partners who understand Arabic, English and GCC compliance.
Put simply: treat identity as the perimeter, assume breach and rehearse your first 24 hours after a ransomware alert all mapped to NCA, TDRA, QCB and sectoral rules.
Introduction
It’s 2:17 a.m. in Riyadh. Your SOC calls: a file server in the OT network is encrypting data and beaconing to an IP outside the Kingdom. At the same time, your board from Dubai to Doha is asking a simple question: “Are we truly resilient?”
In practical terms, GCC cybersecurity in 2026 means three things: treat identity as the new perimeter, adopt a pragmatic Zero Trust model and be ready for ransomware with a clear first-24-hours playbook. For CISOs and executives across Riyadh, Dubai, Abu Dhabi and Doha, success now depends on aligning security with local regulators, cloud regions and bilingual (Arabic–English) user experience – not just buying more tools.
Biggest Cybersecurity Threats Facing GCC Organizations in 2026
The biggest GCC cybersecurity threats in 2026 are targeted ransomware on OT and critical infrastructure, AI-powered social engineering in Arabic and English, and identity abuse in fast-growing cloud environments. These risks hit sectors like oil & gas, government, telecoms, fintech and logistics across Jeddah, Dubai and Doha, where downtime and data leaks quickly become national-level issues.
Ransomware, Double-Extortion and OT Disruption in the Gulf
Ransomware groups now study Gulf networks, map legacy OT/ICS and go after high-availability environments – refineries, utilities, airports and smart ports in cities like Dubai and Doha. Double-extortion (encrypt + leak) is especially damaging in tightly connected GCC markets, where leaked contracts or citizen data can damage trust with regulators and investors.
For critical infrastructure in Bahrain and Oman, attacks often pivot from IT into OT via flat networks and shared admin accounts. That makes network segmentation, PAM, hardening of remote access and tested backups essential if you want to avoid days of outage.
AI-Powered Attacks, Phishing and Deepfake Risks in Arabic & English
Generative AI has made spear-phishing cheaper and more convincing. Attackers send impeccably written Arabic and English emails, clone executive voices for “urgent transfer” calls and use deepfake videos to pressure finance teams. Staff who switch all day between Arabic WhatsApp, English email and bilingual portals can’t rely on “bad grammar” as a red flag anymore.
Security awareness in Kuwait and across the GCC now means realistic simulations, voice-phishing drills and clear escalation channels in both languages not just an annual training video.
Cloud Expansion, Shadow IT and Identity Sprawl in GCC Enterprises
As banks and ministries move to AWS Middle East (Bahrain), Azure UAE Central and Google Cloud Doha regions, identities explode: VPN accounts, SaaS logins, contractor access, local admin accounts and OT credentials. Without strong IAM, a single compromised account can give attackers lateral movement from a cloud dashboard to an on-prem core system.
In 2026, identity and access not the data centre firewall are the primary attack surfaces for Gulf organizations. Shadow IT and unapproved SaaS further widen that identity sprawl unless brought under central governance.
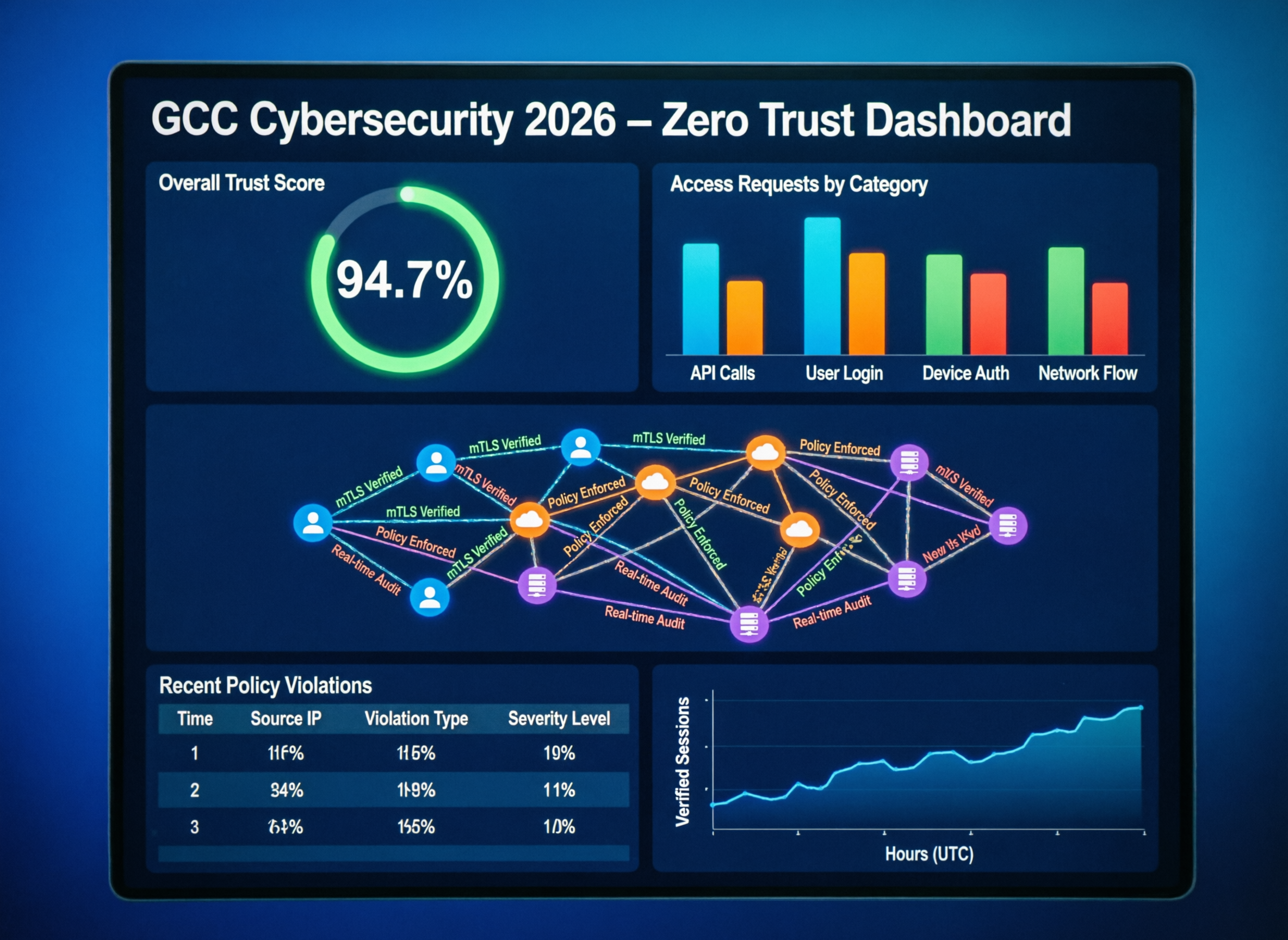
Why Gulf Enterprises Are Moving from Perimeter Security to Zero Trust
Gulf enterprises are moving from perimeter security to Zero Trust because users, apps and data are now everywhere – branches, cloud, mobile and third-party platforms and “inside = trusted” no longer works. In practice, Zero Trust for GCC cybersecurity means continuously verifying users, devices and sessions against policy, rather than assuming any network segment is safe.
Zero Trust Basics for GCC Leaders From “Trust but Verify” to “Never Trust, Always Verify”
For boards in Riyadh or Abu Dhabi, Zero Trust is less about a single product and more about a mindset: every access request is verified based on identity, device posture, location and risk. That’s crucial in hybrid work environments and when external vendors maintain OT systems or SaaS platforms.
Instead of relying on a big firewall around the data centre, access to smart-city control rooms, finance systems and citizen portals is granted per user, per app, per session. This limits blast radius if credentials are stolen or a device is compromised.
Zero Trust Use Cases in KSA, UAE and Qatar Sectors
In Saudi Arabia, Zero Trust helps protect e-government platforms aligned with National Cybersecurity Authority (NCA) and National Data Management Office (NDMO) standards. In the United Arab Emirates, telecom operators and smart-city projects in Dubai and Abu Dhabi use Zero Trust to secure APIs, IoT and citizen mobile apps.
In the State of Qatar, Zero Trust micro-segmentation around stadium and smart-venue networks reduces blast radius if a single asset is compromised. Similar patterns apply to LNG facilities, aviation and logistics hubs where availability and safety are non-negotiable.
Building a Zero Trust Adoption Roadmap for GCC Enterprises
A practical roadmap typically starts with assessment and a focused pilot – for example, securing remote access to critical apps or enforcing MFA and device checks for admin users. Then organizations expand to segment OT networks, protect APIs and enforce least-privilege across cloud workloads.
Regional partners like Mak It Solutions can help embed secure-by-design principles into custom portals and mobile apps, while GCC-based MSSPs provide 24/7 monitoring and incident response tuned to local regulations and Arabic interfaces.
Building an IAM Roadmap for the Gulf that Supports Cloud, Remote Work and Compliance
CISOs in the Gulf can build an IAM roadmap by treating identity as the control plane: unifying logins, enforcing strong authentication and mapping access rights to regulator expectations. Done well, IAM makes cloud, remote work and compliance easier – not harder.
Identity-Centric Security for Hybrid Cloud and Remote Workforces
In 2026, IAM in the GCC means SSO across on-prem and cloud apps, MFA for all users (including contractors), conditional access based on device and location, and privileged access management for admins and OT operators. Identity telemetry then feeds AI-driven threat detection to spot abnormal logins or privilege escalations.
For many organizations, this is integrated with modern applications developed or modernised via web development services and mobile app development that are built for secure authentication from day one.
Mapping IAM Controls to GCC Regulations and Sectoral Rules
Banks and fintechs in KSA must align IAM with Saudi Central Bank (SAMA) and NCA requirements, including strong authentication, access logging and segregation of duties. In Qatar, Qatar Central Bank (QCB) has issued technology and cybersecurity regulations that emphasize secure access, monitoring and data handling across banking channels.
For all regulated entities, IAM must align with data classification and access governance standards set by NDMO and similar bodies, turning regulatory text into concrete role models, approval workflows and access review cycles.
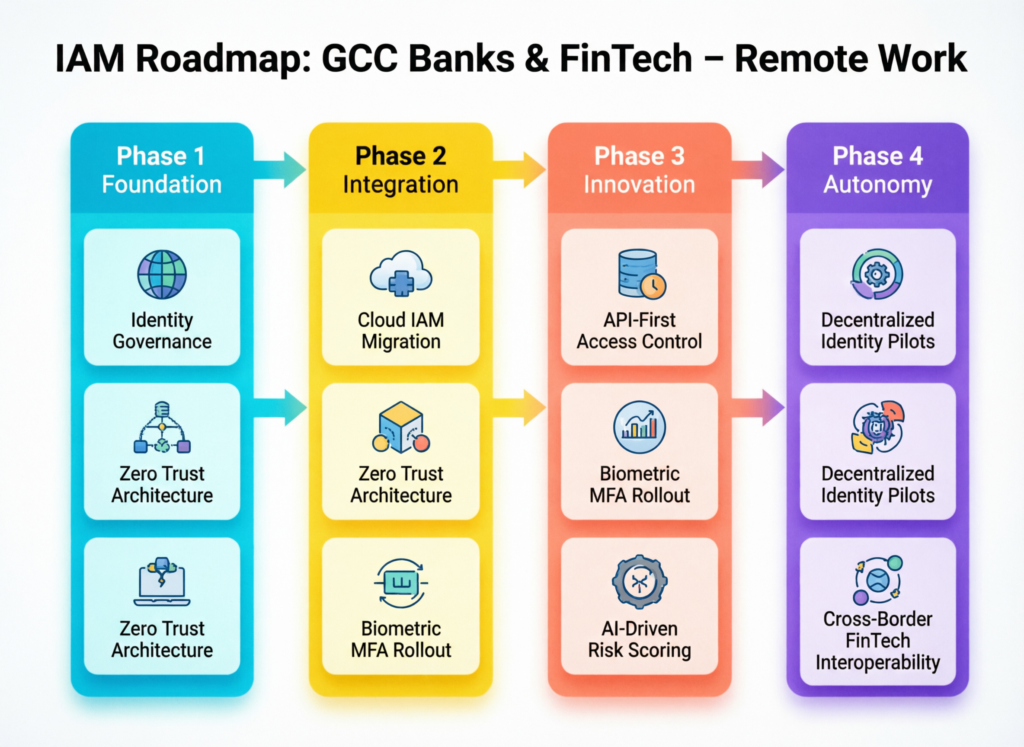
Arabic-Friendly IAM and User Experience for GCC Staff and Customers
Adoption fails if users struggle with English-only portals or OTP flows. IAM portals and self-service password resets should be fully localized, with Arabic-first UX and bilingual support scripts. National identity systems like UAE Pass, Open Banking KSA APIs and Qatar’s evolving digital ID services set expectations for smooth, secure sign-in.
Organizations can extend these patterns into their own e-commerce, banking and government platforms, often supported by partners delivering SEO-ready, multilingual experiences.
Ransomware Defense and the First 24 Hours After an Incident in the GCC
In the GCC, the first 24 hours after a suspected ransomware attack should follow a clear playbook: detect, contain, isolate, communicate, notify regulators and start recovery all while protecting evidence. Companies that rehearse this process suffer less downtime, pay fewer ransoms and regain regulator confidence faster.

Pre-Incident Hygiene Backups, MDR and Tabletop Exercises
Before any incident, organizations need immutable, offline backups; network segmentation between IT and OT; and tested recovery for critical services. Managed detection and response (MDR) or SOC services hosted in GCC data centres help meet data residency and log retention requirements, especially where regulators expect logs to remain in-country.
Regular tabletop exercises in Riyadh, Dubai and Doha align executives, legal, communications and technical teams on who does what when an alert hits at 2 a.m. That rehearsal is often the difference between a contained event and a multi-day crisis.
24-Hour Ransomware Response Playbook for GCC Organizations
A practical first-day playbook could look like this.
Confirm the incident
Validate alerts, capture screenshots and preserve logs so you know it is truly ransomware and you have evidence.
Contain and isolate
Disconnect affected servers and endpoints; block malicious IPs and domains; disable compromised accounts.
Protect crown jewels
Prioritize banking systems, citizen portals and OT assets supporting public services; increase monitoring and tighten access.
Engage leadership
Brief C-level, legal and communications, including country leads in KSA, UAE and Qatar, on status and key decisions.
Notify regulators and CERTs
Follow sector guidance for timing and channels in each jurisdiction; coordinate with MSSPs and legal.
Begin recovery
Restore from clean backups, validating data integrity and confirming a malware-free state before going back into production.
Review and improve
Within days, run a post-incident review and update controls, playbooks and training based on lessons learned.
Working with Local CERTs, Regulators and Law Enforcement
When incidents affect telecoms, banks or government platforms, organizations should coordinate with local CERTs and cyber agencies such as Qatar’s National Cyber Security Agency (NCSA) and Saudi’s NCA. Sector regulators SAMA, QCB and the Telecommunications and Digital Government Regulatory Authority (TDRA) may require timely notification and evidence of containment.
Clear engagement plans, including Arabic-language points of contact, speed up approvals for public statements and cross-border cooperation if attacks touch multiple GCC markets.
Data Residency, Local Cloud Security and GCC Sovereignty Requirements
Data residency and local cloud security are critical in the GCC because regulators increasingly see data as a strategic national asset especially for finance, health and government services. Using local cloud regions and aligning controls with national frameworks reduces legal risk and builds public trust.
Overview of Cloud Cybersecurity Controls and Data Residency Expectations in KSA
In KSA, updated Cloud Cybersecurity Controls (CCC 2: 2024) from NCA and NDMO’s data governance standards emphasize where sensitive data may be stored, processed and backed up – and under which jurisdictions. (National Cybersecurity Authority) Organizations running workloads on AWS Middle East (Bahrain) or emerging local KSA regions must map each dataset to these requirements and consider when encryption, tokenization or in-country DR sites are mandatory.
UAE and Qatar Cloud Security, Free-Zone Rules and Cross-Border Data
In the UAE, TDRA’s information assurance and cloud frameworks shape how critical infrastructure entities adopt IaaS, PaaS and SaaS, while the federal Data Office drives broader data protection laws. Free zones like Abu Dhabi Global Market (ADGM) and Dubai International Financial Centre (DIFC) add their own data protection regimes for financial firms.
In Qatar, QCB and NCSA guidance influences where banks host core systems and how cross-border data flows are controlled. Regional CISOs increasingly work with legal and data-protection officers to maintain a living map of data flows in and out of the country.
Designing Cloud-Native Security Controls for Regional Data Centers
Designing secure architectures means using cloud-native controls IAM, encryption, logging, DLP and WAF and aligning them with GCC regulations. Choosing AWS Bahrain, Azure UAE Central or Google Cloud’s Doha region helps balance latency, customer trust and regulatory expectations. (Amazon Web Services, Inc.)
In practice, many organizations pair in-region SOC services with secure application development and data engineering from partners who already deliver business intelligence solutions and modern web platforms for regulated industries.
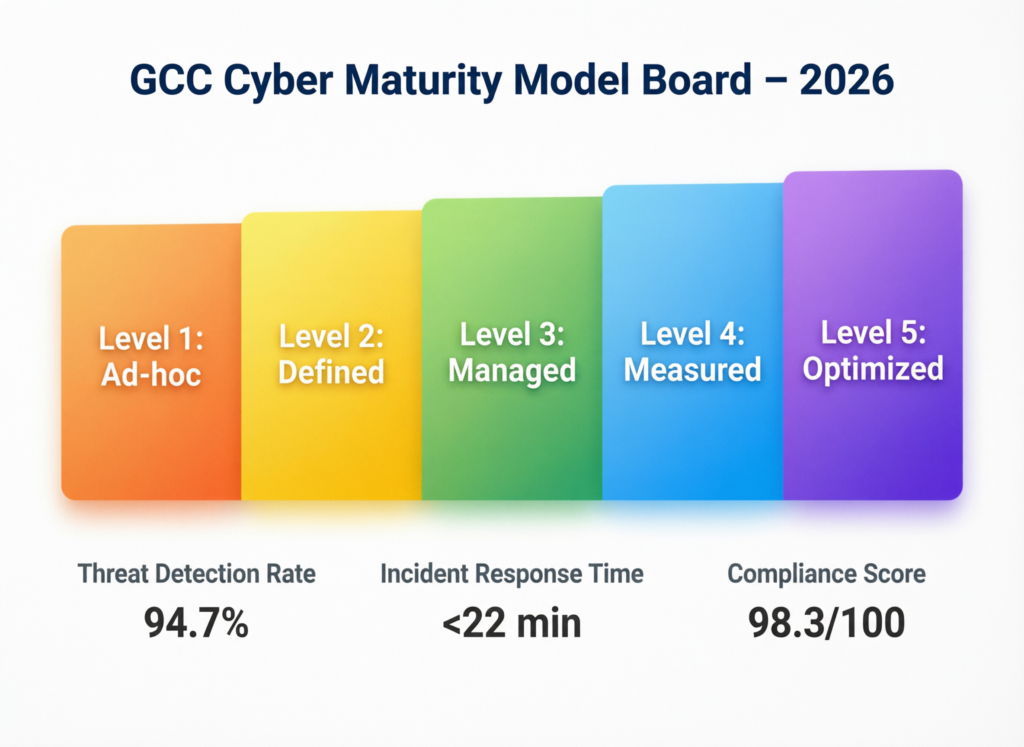
Measuring the Maturity of Zero Trust, IAM and Ransomware Defense in GCC Organizations
To measure maturity in 2026, Gulf organizations combine a simple capability model (from ad-hoc to optimized) with concrete KPIs: coverage, speed and alignment with local regulation. This gives boards in KSA, UAE, Qatar, Bahrain, Kuwait and Oman a shared language for cyber resilience.
Maturity Models Tailored to GCC Sectors and Regulations
A 4-level model Reactive, Defined, Aligned, Optimized works well. “Aligned” means Zero Trust, IAM and ransomware processes are mapped to frameworks from NCA, TDRA and QCB; “Optimized” adds continuous improvement, automation and board-level oversight.
Benchmarks from peer banks in Riyadh, e-commerce providers in Dubai and logistics hubs in Doha help CISOs explain where they stand and what “good” looks like in their sector.
KPIs and Board-Level Metrics for Cyber Resilience
Executives respond best to numbers tied to business risk. Useful KPIs include: percentage of users with MFA; percentage of privileged accounts under PAM; mean time to detect/respond to incidents; percentage of critical systems with tested ransomware recovery (RPO/RTO within business tolerance); and phishing simulation failure rates in Arabic and English.
Dashboards from SIEM/SOAR tools can surface these KPIs in board packs alongside financial and operational metrics, so cyber resilience sits next to revenue and uptime – not in a separate, technical appendix.
When to Engage Regional MSSPs, SOCs and Strategic Partners
For many CISOs, the tipping point comes when they need 24/7 coverage, OT security expertise or structured regulatory reporting. At that stage, GCC-based MSSPs and SOCs combined with engineering partners like Mak It Solutions for secure, scalable applications and UI/UX and web design – can accelerate maturity.
This blended model lets in-house teams focus on governance and strategy while partners handle heavy operations, DevSecOps and continuous improvement.
If you’re responsible for GCC cybersecurity in a bank, fintech, government entity or fast-growing tech company, 2026 is the year to turn strategy into execution: Zero Trust, IAM and ransomware readiness tailored to your regulators and cloud footprint. The good news? You don’t have to design everything from scratch.
The team at Mak It Solutions already builds secure, cloud-ready platforms, mobile apps and data solutions for regulated industries and can work alongside your CISO, MSSP or SOC to embed security into every customer journey. Reach out via our contact page to discuss a GCC-specific roadmap, or explore our full service portfolio to see how we support leaders across the region.
FAQs
Q : How do the costs of implementing Zero Trust differ between Saudi Arabia, UAE and Qatar?
A : Costs vary more by complexity and sector than by country, but there are GCC patterns. In Saudi Arabia, larger banks and government entities often invest heavily to align with NCA, NDMO and SAMA standards, including in-country SOCs and data-localization controls. The UAE typically sees higher spend on cloud-native security and smart-city use cases, especially in Dubai and Abu Dhabi. In Qatar, budgets often focus on banking, energy and critical national infrastructure aligned with QCB and NCSA frameworks. Spreading projects over phases and re-using existing tools can help control overall cost.
Q : Is Zero Trust or IAM explicitly required for banks under SAMA or QCB cybersecurity rules?
A : Neither SAMA nor QCB usually name “Zero Trust” as a product you must buy, but their regulations effectively require the building blocks of Zero Trust and strong IAM. SAMA cyber and technology risk guidance expects robust authentication, access control, monitoring and segregation of duties for Saudi banks and fintechs, which align naturally with Zero Trust and identity-centric security. QCB’s technology and data handling regulations in Qatar require banks to secure access to systems, protect payment channels and monitor cyber risk. In practice, banks that adopt modern IAM and Zero Trust architectures find it easier to demonstrate compliance in audits and regulator reviews.
Q : Can GCC organizations store customer data outside the region if they use global cloud providers?
A : Whether you can store customer data outside the GCC depends on sector, data type and regulator expectations. Some workloads can use global regions if data is encrypted and protected by strong contractual and technical controls; others, especially in finance and government, may need to stay within KSA, UAE or Qatar. Updated NCA CCC 2 controls, NDMO standards in Saudi, TDRA guidance in the UAE and QCB rules in Qatar all influence data-location decisions.
Many organizations use a hybrid approach: sensitive data in regional or in-country regions (AWS Bahrain, Azure UAE Central, GCP Doha), with less sensitive workloads in other locations. Early legal and compliance involvement is essential.
Q : Are local GCC MSSPs and SOCs better than global providers for ransomware protection and response?
A : Global providers bring scale and tooling, but local GCC MSSPs and SOCs often win on context: Arabic-speaking analysts, familiarity with sectors like oil & gas and government, and established processes for dealing with NCA, TDRA, QCB and other regulators. During a ransomware incident, understanding local reporting timelines, acceptable communication styles and cross-border data movement rules can significantly reduce risk.
Many organizations adopt a hybrid model: a regional SOC for front-line monitoring and response, plus specialized global threat-intelligence services. The right choice depends on your regulatory exposure, OT footprint and appetite for managing multiple vendors.
Q : Do GCC regulations expect cybersecurity awareness training to be delivered in Arabic as well as English?
A : Regulations rarely dictate the exact training language, but they consistently require effective awareness programs and in the GCC that almost always means Arabic as well as English. Employees in government, banking, logistics and healthcare across Riyadh, Dubai, Doha and beyond often operate primarily in Arabic, so English-only content is unlikely to meet the spirit of frameworks from NCA, TDRA, QCB or NCSA.
Many regulators also emphasize the role of culture and human behaviour in cyber resilience under national visions like Saudi Vision 2030. Delivering bilingual training, phishing simulations and playbooks shows regulators that your program is designed for real users, not just for audit checklists