GCC Fintech API Security Guide for Banks & Wallets
GCC Fintech API Security Guide for Banks & Wallets
GCC Fintech API Security Guide for Banks & Wallets
Fintech API security in GCC means protecting banking, wallet and open banking APIs in Saudi Arabia, United Arab Emirates and Qatar so they meet local regulations (SAMA, CBUAE, QCB, PDPL) while resisting bots, fraud and abuse. In practice, GCC fintech teams need a layered stack API gateway, WAF, FAPI-compliant authorization server, bot management and fraud/risk engines designed for local data residency, Arabic-first UX and strong customer authentication for open banking.
Introduction
Imagine a digital bank in Riyadh or Dubai: SAMA or CBUAE approvals in place, WAF and IAM deployed, yet carding bots hammer card APIs all night and credential stuffing hits login and consent APIs every weekend. Fraud spikes, SOC alerts explode, and yet most of the traffic still looks “normal” to legacy controls.
That’s the reality driving fintech API security in GCC. Regulations like SAMA Open Banking, CBUAE Open Finance and QCB Technology Risk are moving fast, while many teams are still leaning only on traditional WAF rules and simple rate limiting that don’t really see API and bot abuse.
This guide defines what fintech API security in GCC actually means, maps the core requirements for Saudi, UAE and Qatar, and walks through how to build a combined API security + bot defense stack from gateway and WAF to device fingerprinting, behavioral analytics and fraud engines plus a practical roadmap and selection checklist for GCC banks, wallets and fintechs.
What Is Fintech API Security in GCC?
From “API security” to “fintech API security in GCC”
When we say APIs here, we mean the real workhorses of GCC finance: mobile banking APIs, digital wallet and BNPL APIs, card and payment initiation APIs, and open banking aggregators that connect TPPs into bank cores.
Fintech API security in GCC goes beyond generic OWASP protections. It covers.
Strong, standards-based authorization (OAuth2 + a FAPI-compliant authorization server) for open banking and open finance.
Protection of critical journeys like onboarding, consent, payment initiation and card management from bots and scripted abuse.
Alignment with local laws such as Saudi PDPL and NDMO data standards, which emphasise data residency and tight control of cross-border transfers.
GCC-specific constraints make this different from “anywhere in the world” API security: Arabic-first UX, Sharia-compliant products, in-country hosting in Jeddah or local sovereign clouds, and identity schemes such as UAE Pass UAE Pass that need to be woven into authentication and consent flows.
GCC fintech landscape: Saudi, UAE, Qatar priorities
Across the region, digital banks, wallets, BNPL players and remittance apps are growing quickly in Saudi, the UAE and Qatar. Open banking and open finance programs mean regulators, partners and super-app ecosystems are all integrating through APIs not batch files.
For example
Saudi: SAMA Open Banking and initiatives like Open Banking Saudi Arabia make APIs the default way to expose consented data and payments.
UAE: CBUAE Open Finance and an API Trust Framework rely on secure APIs mediated through a central API hub.
Qatar: Qatar Central Bank (QCB) Technology Risks and PSP cyber regulations push banks and payment providers to build secure API-centric platforms.
Why generic “global” API security advice is not enough for GCC
Most global API security blogs don’t talk about data residency under Saudi PDPL, TDRA cloud controls or QCB technology risk instructions. They rarely mention Arabic-first UX, geo-fenced hosting, or national digital ID schemes like UAE Pass.
For GCC fintechs, you need patterns like:
Geo-fenced deployment in AWS Bahrain, Azure UAE Central or GCP Doha. (Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP))
Support for local sandboxes in SAMA and ADGM/DIFC.
API designs that respect Sharia-compliant products and local KYC rules.
Regulatory Drivers for Fintech API Security in GCC
Key API security requirements under SAMA Open Banking in KSA
Direct answer: Under SAMA Open Banking, fintechs and banks must expose open banking APIs with strong OAuth2 / FAPI security, secure customer consent journeys, encryption in transit and at rest, and detailed logging/monitoring mapped to SAMA’s open banking framework.
Practically, Saudi Central Bank (SAMA) expects.
OAuth2 with Financial-grade API (FAPI) profiles, mTLS and modern token patterns.
Strong customer authentication for open banking (SCA via app-to-app, CIBA-style or redirect flows)
Explicit consent and granular scopes (e.g. accounts, transactions, payments).
Comprehensive audit trails: who accessed what, via which TPP, on which device.
All of this should be baked into your API design, not bolted on as sidecar scripts.
CBUAE Open Finance & TDRA expectations for API security in UAE
For the UAE, the CBUAE Open Finance Regulation and Open Finance Standards require secure, standardised APIs exposed through a central API hub, with strong identification, authentication, consent and notification across participants.
At infrastructure level, the Telecommunications and Digital Government Regulatory Authority (TDRA) information assurance and cloud frameworks push entities to adopt strong security controls for cloud-hosted APIs in Abu Dhabi and Dubai.
So UAE fintech API security must combine:
CBUAE Open Finance FAPI 2.0 security profiles.
TDRA IA controls and cloud security expectations around logging, encryption and monitoring.
QCB Technology Risk and cyber rules for Qatar fintech APIs
QCB’s Technology Risks Regulation and cyber rules require banks and PSPs to operate secure technology platforms, including robust identity and access management, monitoring and regular reviews of online banking channels explicitly including APIs.
For Qatar’s open banking ambitions and Qatar Digital Government initiatives in Doha, this means:
Secure API design with strong authentication and encryption.
Rigorous change management: API changes reviewed for technology and cyber risk impact.
Evidence that API controls protect Islamic banking and cross-border payment journeys running across Doha and other GCC hubs.
Abuse & Bot Threats Against GCC Banking and Fintech APIs
Real attacks on GCC fintech APIs: ATO, carding, fake accounts
In production, GCC teams see.
Account takeover (ATO) via credential stuffing against login and strong customer authentication endpoints.
Carding on payment, tokenization and checkout APIs especially where debit and prepaid cards are popular for BNPL and wallets.
Fake KYC and bonus abuse on onboarding and promo APIs for Islamic products, loyalty schemes and remittance corridors between Riyadh, Dubai and Doha. (Mak it Solutions)
Bots mix low-and-slow traffic with residential IPs and mobile user agents, so they glide past simple rate limits.
Why WAF and API gateways alone don’t stop bots
Traditional WAF and API gateways mainly see IPs, paths and coarse request patterns. For fintech abuse that’s not enough.
Modern attackers rotate IPs, emulate mobile SDKs and replay valid tokens. To stop them, you need:
Device fingerprinting and behavioral analytics for fintech fraud (session age, velocity, device history).
Identity-aware rate limiting and throttling to prevent API abuse (per user, device, card, BIN or TPP – not just per IP)
Correlation with fraud and risk engines to make real-time decisions.
How GCC digital banks can protect open banking APIs from bots & abuse
Direct answer: GCC digital banks should protect open banking APIs with layered defenses: SCA and FAPI-grade security, bot management tuned for banking traffic, and tight integration with fraud engines that use device and behavioral signals to block abuse in real time.
In practice, that looks like.
Enforcing strong customer authentication for open banking with device binding and app-to-app journeys.
Bot management that understands financial flows (login → consent → payment initiation) and flags anomalies.
Feeding API telemetry into fraud platforms and SOC tooling so carding spikes, unusual consent grants and risky devices are investigated quickly.
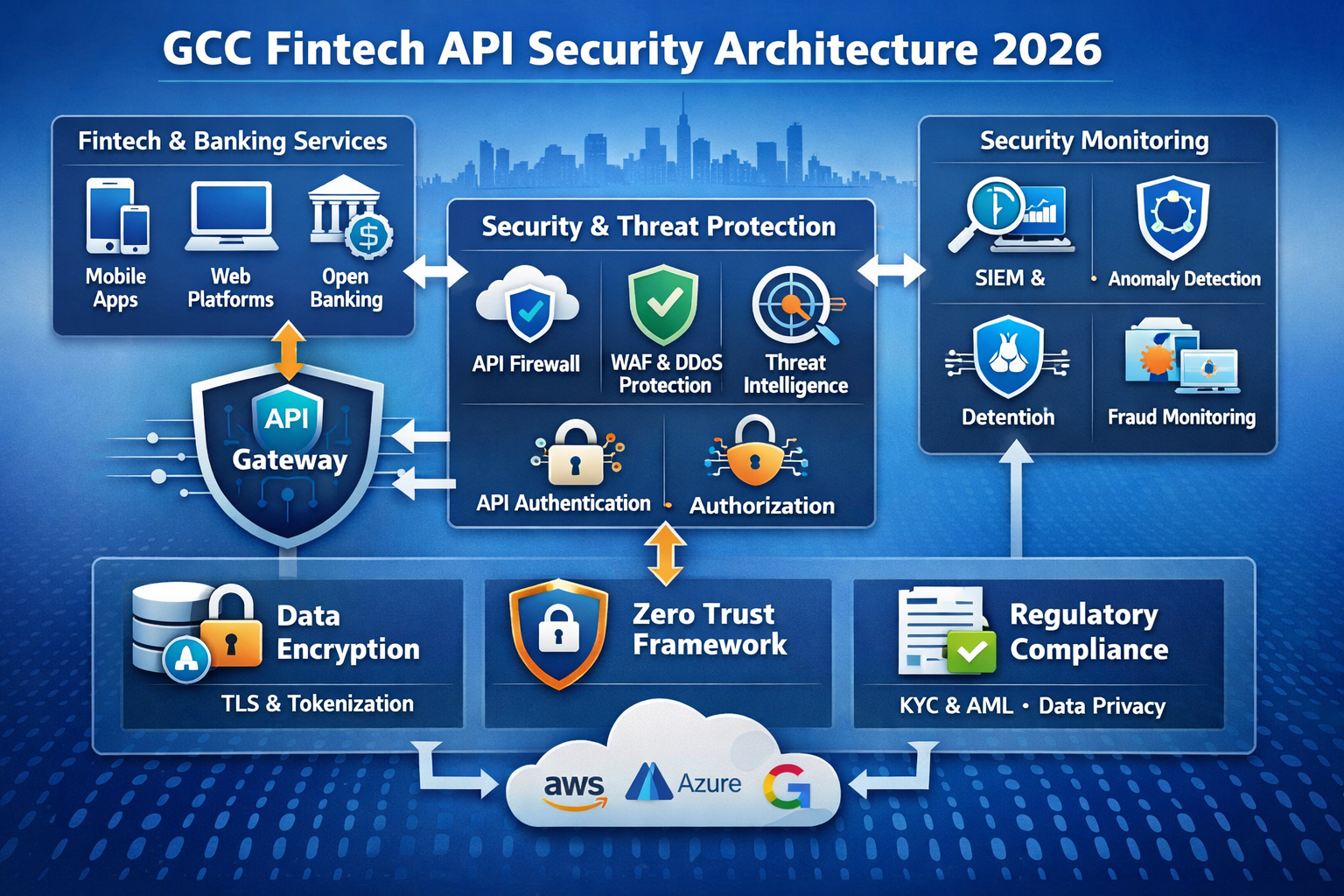
Designing a GCC-Ready API Security & Bot Defense Stack
Core components: API gateway, WAF, bot management, IAM, fraud engine
A GCC-ready fintech stack typically combines:
API gateway to publish, secure and observe APIs, enforce quotas and validate schemas.
WAF to stop generic web threats and OWASP API Security Top 10 issues.
Bot management for device fingerprinting, behavioral scoring and real-time challenges.
IAM / CIAM to deliver OAuth2/OIDC, FAPI-compliant authorization server capabilities, and SCA flows.
Fraud engine to join payments, KYC and device data for risk-based decisions.
Best way to combine WAF, API gateway & bot management
Direct answer: The best way for GCC fintechs to combine WAF, API gateways and bot management is to place the WAF at the edge, use the gateway as the API “brain,” and deploy bot management close to user and business logic, with shared telemetry into fraud and SOC platforms.
Typical pattern.
Edge: WAF + CDN terminate TLS, block obvious bad traffic and enforce baseline signatures.
Gateway tier: validates tokens, applies scopes, routes to microservices and enforces quotas.
Bot layer: inspects device fingerprints and behavior, enriches requests with risk scores, and applies identity-aware throttling.
This is where you plug in device fingerprinting, behavioral analytics and risk scoring to protect key journeys without breaking good users.
GCC constraints: data residency, cloud regions, and cross-border APIs
Architecture choices must respect.
Saudi PDPL & National Data Management Office (NDMO) standards, which restrict cross-border transfers and push in-kingdom hosting.
UAE expectations around TDRA IA and CBUAE rules, often favouring UAE-hosted cloud or sovereign setups.
QCB instructions and sector rules that may require hosting in or near Qatar.
Many fintechs mix Amazon Web Services (AWS) Bahrain, Microsoft Azure UAE Central and Google Cloud Platform (GCP) Doha regions, sometimes alongside sovereign clouds, to keep latency low and data close. (Mak it Solutions)
Implementing & Operationalizing API Security for GCC Fintechs
API security testing and DevSecOps for fintech microservices in GCC
Shift-left means building API security into CI/CD for teams in Kuwait, Bahrain and Oman, not just big banks in Riyadh or Dubai.
Key steps.
Use SAST/DAST and API-specific scanners against OpenAPI/Swagger definitions, mapped to OWASP API Security Top 10.
Add security checks to pipelines for mobile and web backends.
Re-use learnings from your zero trust or GCC cybersecurity roadmap. (Mak it Solutions)
Link this with partners that already think API-first—our own guides on web development trends in the Middle East for KSA & UAE and GCC cybersecurity 2026 show how architecture and security converge in the region.
Continuous monitoring, SOC integration, and incident response
Day-2 operations depend on.
Centralised API logs and metrics in your SIEM.
Dashboards for auth failures, consent errors, carding patterns and sudden traffic from new regions.
Clear runbooks shared between product, fraud and SOC teams.
Resources like the MDR vs SOC vs XDR buyer’s guide for Saudi, UAE & Qatar can help you decide whether to run this in-house or with an MSSP.
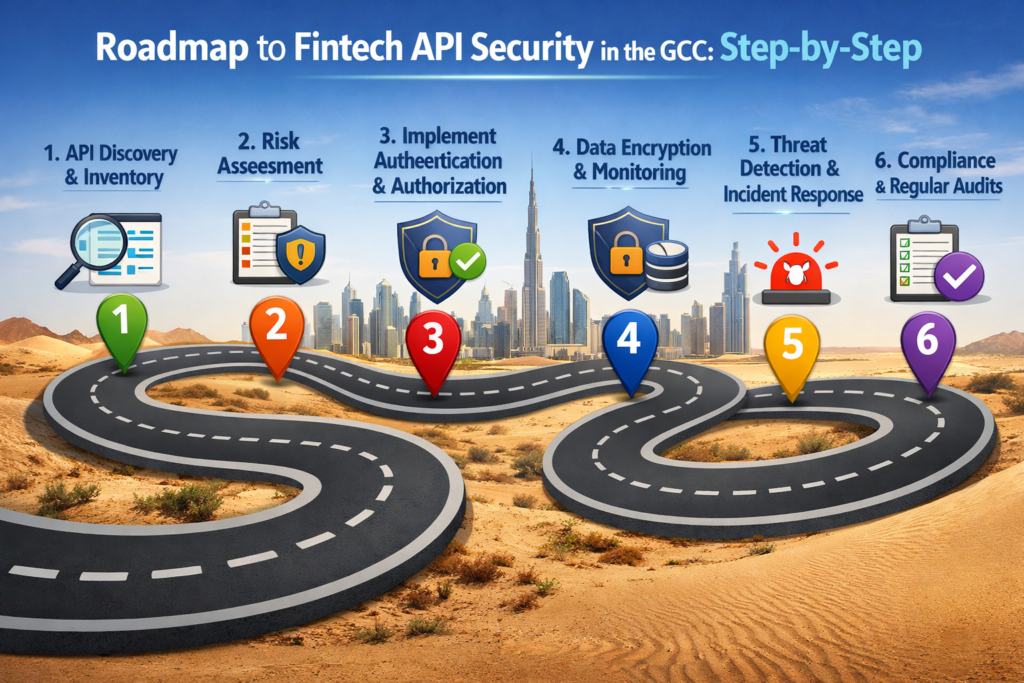
Step-by-step roadmap for Saudi, UAE and Qatar fintech teams
Discover and inventory all fintech APIs. Use gateways, code scans and traffic discovery to list every banking, wallet and partner API.
Classify data and critical journeys. Mark payments, onboarding, consent and high-risk flows for priority protection.
Map regulatory requirements per country and regulator. Align each API with SAMA, CBUAE, QCB, PDPL and TDRA/NDMO expectations.
Design target architecture (gateway, WAF, bot, fraud). Choose components that support FAPI, SCA, bot detection and data residency options in KSA, UAE and Qatar.
Roll out testing, monitoring and incident runbooks. Automate API security testing, plug telemetry into SOC and rehearse incident scenarios like carding waves or compromised TPPs.
This roadmap lets Saudi, UAE and Qatar fintech teams continuously test and monitor API security without stalling delivery.
GCC Use Cases & Reference Architectures
Open banking in Saudi Arabia: secure consent, aggregation & payment initiation
A typical SAMA-aligned flow: PSU in Riyadh approves access in their bank app → TPP calls the bank’s consented APIs → the bank’s FAPI-secured authorization server issues tokens → APIs for account data or payment initiation execute under SCA.
Enforce mTLS and token binding at the gateway, add bot and fraud checks around login and consent, and keep detailed logs for audits.
UAE digital wallets, BNPL and super-apps: API abuse hotspots
In UAE wallets, BNPL apps and super-apps regulated via CBUAE, abuse clusters around:
Top-up and payout APIs
Voucher and promo redemption
Referral and cashback endpoints
Here, combine targeted rate limiting and throttling to prevent API abuse with behavioral analytics and device reputation, especially for users authenticating via UAE Pass or operating in free-zone environments like ADGM and DIFC. (Central Bank Rulebook)
Qatar Islamic banking and cross-border APIs: risk & design patterns
For Qatar’s Islamic banks and cross-border APIs, align designs with QCB cyber rules and data localization constraints.
Architect patterns where sensitive data for Islamic products and remittance corridors is processed in-region, with carefully controlled cross-border calls into partner banks or regional hubs in Riyadh, Dubai or Doha. (Qatar Central Bank)
Selecting API Security & Bot Defense Solutions for GCC
Evaluation checklist for GCC fintech API security platforms
When you evaluate vendors, look for:
Full coverage of OWASP API Security Top 10 and continuous discovery of “shadow” APIs.
Bot and abuse detection tuned for financial traffic (ATO, carding, fake KYC, promo abuse).
Data residency and deployment options in KSA, UAE and Qatar (regional cloud, sovereign, on-prem).
Tight integration with gateways, IDPs, fraud tools and your existing SOC/MDR stack.
Guides like Middle East cloud providers for KSA, UAE & Qatar CIOs can help you understand which cloud and deployment models best fit these needs.
Questions to ask vendors and partners in GCC
Ask concrete questions such as.
“How do you map controls to SAMA Open Banking, CBUAE Open Finance and QCB Technology Risks?”
“Can you show evidence packs regulators will accept in Riyadh, Dubai and Doha?”
“Where exactly is telemetry stored, and how do you respect Saudi PDPL and UAE/Qatar data rules?”
And don’t forget to ask about experience with ADGM, Dubai International Financial Centre (DIFC), and sandbox environments.
Phased rollout and success metrics for GCC banks and fintechs
Start with a pilot on a high-risk journey (e.g. wallet login + top-up), then expand. Track KPIs like:
Reduced fraudulent transactions and bot traffic
Faster time-to-detect and time-to-contain incidents
Higher API inventory coverage
Lower developer friction (fewer fragile custom rules)
Our content on GCC cyber security and zero trust and identity as the new perimeter provides additional context for setting realistic targets and making them stick.
Concluding Remarks
GCC regulators are making open banking and open finance a reality—and that means fintech API security in GCC is no longer “nice to have.” It sits at the heart of compliance and customer trust, right alongside bot and abuse defense.
If you start with visibility, map your APIs to SAMA, CBUAE, QCB and PDPL expectations, and then design a clear architecture combining gateway, WAF, bot and fraud capabilities, you can industrialise testing and monitoring without slowing product delivery.
This guide shares general security perspectives and is not legal, regulatory or financial advice. Always review requirements with your own compliance, legal and risk teams.
If you’re a CISO, security lead or product owner in a GCC bank, wallet or fintech, now is the time to benchmark your current API stack against a Saudi/UAE/Qatar-ready roadmap. Mak It Solutions already works with GCC teams on cloud, security and data-driven architectures, and our blogs on web development trends in the Middle East and Middle East cloud strategy show how we think.
If you’d like a region-focused assessment or workshop from API inventory to bot defense and data residency options reach out to Mak It Solutions to design a tailored fintech API security strategy for Saudi, UAE and Qatar.( Click Here’s )
FAQs
Q : Is open banking API security in Saudi Arabia different from the UAE and Qatar?
A : Yes, there’s a shared foundation (OAuth2, FAPI, SCA, logging), but each jurisdiction adds its own requirements. Saudi Arabia leans on SAMA Open Banking standards and PDPL data residency rules; the UAE layers CBUAE Open Finance, TDRA IA regulations and free-zone regimes like ADGM/DIFC; Qatar focuses on QCB Technology Risks and PSP cyber regulations. For a GCC fintech, the safest approach is to adopt a common security core, then add country-specific add-ons for data residency, sandboxing and evidence packs.
Q : Do GCC fintechs need separate API security controls for regulatory sandboxes vs production environments?
A : Usually yes, but the separation is more about scope and data than about weaker controls. Sandboxes (SAMA, CBUAE, TDRA or local hubs) typically use synthetic or masked data and allow faster iteration, but regulators still expect sound authentication, logging and segmentation so sandbox access doesn’t leak into production. In production, additional layers like fraud engines, 24/7 monitoring and stricter change management kick in. Saudi Vision 2030 and UAE/Qatar digital strategies all encourage sandbox innovation but assume that when you go live, your security posture is fully enterprise-grade.
Q : How can a UAE-based fintech prove to regulators that its bot mitigation on banking APIs is effective?
A : Evidence is key. UAE fintechs should document their bot defense design (signals collected, decision logic, fail-safes), show test results from simulated attacks, and provide historical metrics—blocked carding attempts, reduced ATO, improved fraud loss ratios. Align these with TDRA IA controls and CBUAE Open Finance Standards, and include them in security audits or design reviews. Linking bot telemetry with SOC and fraud systems—and being able to show end-to-end traces for incidents makes it much easier to convince regulators and auditors that API bot defense is not just a checkbox.
Q : What are common mistakes GCC banks make when relying only on WAF for API security?
A : Common mistakes include assuming IP-based blocking is enough, not authenticating machine-to-machine APIs properly, and leaving shadow or legacy APIs unprotected behind VPNs. Another frequent gap is treating open banking security as a “gateway/WAF rule” issue instead of a full FAPI/OAuth design problem. Banks that align only to generic WAF guidance, without referencing local regulations (SAMA, TDRA IA, QCB tech risk, PDPL) and the OWASP API Security Top 10, often discover too late that bots and sophisticated fraud bypass these shallow controls. (Mak it Solutions)
Q : Can GCC fintech startups use global cloud regions for API security tools and still meet local data residency rules?
A : Sometimes, but only with careful design. Many GCC startups run core banking and customer data in-region (AWS Bahrain, Azure UAE, GCP Doha or sovereign clouds) while using global SaaS for less sensitive telemetry or analytics. Under PDPL and QCB rules, sending production personal data or full transaction details to offshore tools can be problematic, whereas aggregated or anonymised metrics may be acceptable. The safest path is to pick API security and bot solutions that can be deployed in-region and then add tightly controlled, regulator-approved cross-border flows where needed. (Mak it Solutions)


