Identity Is the New Perimeter for Cloud IAM Security
Identity Is the New Perimeter for Cloud IAM Security
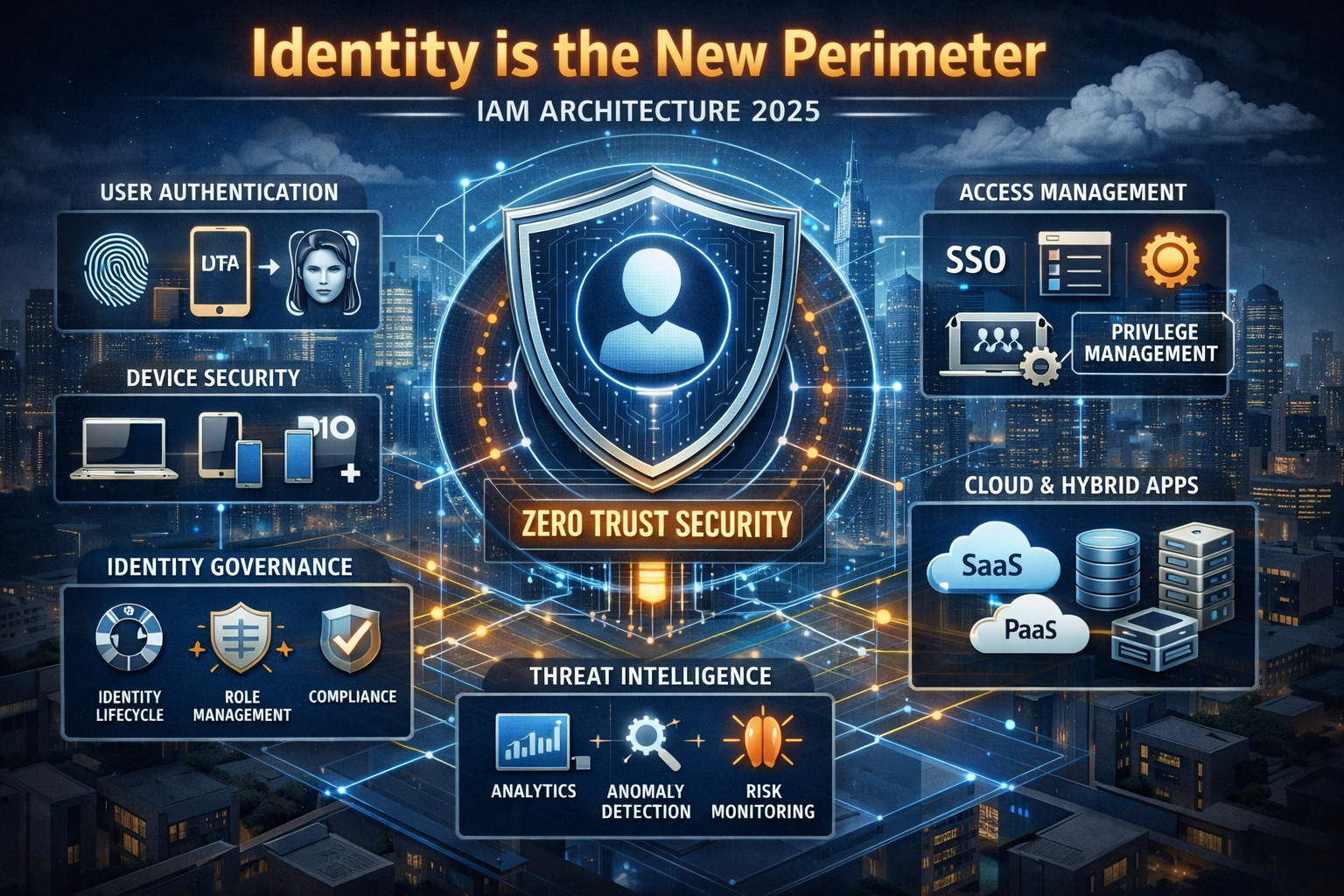
Identity Is the New Perimeter for Cloud IAM Security
In 2025, “identity is the new perimeter” means that users, devices and workloads not the network are now the primary control point for access, detection and policy enforcement in IAM. For US, UK and EU organisations, an identity-first, Zero Trust IAM strategy uses strong MFA, least privilege, continuous monitoring and cloud IAM controls to protect hybrid, SaaS and multi-cloud environments.
The corporate perimeter you grew up with has disappeared. SaaS sprawl, remote and hybrid work, APIs, contractors, third-party admins and machine identities mean your critical assets are now everywhere across as-a-service (XaaS) platforms, mobile apps and data lakes from Amazon Web Services (AWS) to niche SaaS used by small teams. Traditional IP ranges, VPN tunnels and on-prem firewalls simply don’t map cleanly to business risk anymore.
That’s why identity is the new perimeter. Instead of trusting everything “inside” the network, modern IAM assumes every request is untrusted until the identity, device, context and risk signals check out. For CISOs, security architects and IAM owners in mid-to-enterprise organisations across the United States, United Kingdom and Germany, this is a practical playbook: what “identity is the new perimeter” really means, how it connects to Zero Trust and Cloud IAM, and how to move from slideware to a working identity-centric security architecture.
At Mak It Solutions we see this shift up close when we build secure web, mobile and analytics platforms for clients in New York, London, Berlin and across the EU every successful project treats IAM as the control plane, not an afterthought.
What Does “Identity Is the New Perimeter” Mean for IAM?
A simple definition for security and IAM leaders
“Identity is the new perimeter” means user, device and workload identities not networks now form the primary control point for access, detection and policy enforcement in modern IAM. In an identity-centric model, every access decision is tied back to an authenticated identity with least-privilege permissions, verified continuously with context such as device health, location and behaviour.
Put differently: identity is the enforcement plane for Zero Trust, while the network becomes just a transport layer. This is what identity is the new perimeter means for US enterprises, UK public bodies and EU-regulated organisations: if an attacker owns your identities, they own your business, regardless of your firewalls.
How identity became the only reliable perimeter
Several forces have pushed IAM into the spotlight
SaaS adoption and cloud migration
With public cloud and SaaS dominating new workloads, your most critical assets often sit outside traditional network boundaries.
Hybrid and remote work
Users routinely connect from coffee shops in New York City, homes near London or co-working spaces in Berlin, using a mix of managed and BYOD devices.
APIs, bots and machine identities
Service accounts, CI/CD runners, API keys and AI agents massively outnumber humans in many environments.
Third-party access
Partners, vendors and MSPs need scoped, auditable access into your environments.
At the same time, attackers have professionalised identity-based attacks. Verizon’s 2024–2025 DBIR data shows stolen credentials and basic web app attacks involving credentials remain one of the top initial access vectors, involved in around a quarter of analysed breaches. A 2026 incident response study found identity weaknesses present in roughly 90% of investigated breaches.
When credentials, OAuth tokens or cloud roles are compromised, the old assumption that “inside equals trusted” completely breaks.
How “identity is the new perimeter” connects to Zero Trust IAM
Zero Trust, as defined by NIST SP 800-207, moves defences from static, network-based perimeters to focus on users, assets and resources. In practice, identity-first IAM is how you implement the three core Zero Trust principles:
Verify explicitly
Strong authentication, MFA, device posture, risk signals and identity threat detection and response (ITDR) validate every request.
Use least-privilege access
Access is tightly scoped using roles, policies and just-in-time elevation.
Assume breach
Identities, sessions and tokens are continuously monitored for anomalies and quickly revoked or re-authenticated when something looks wrong.
Vendors like Microsoft (Entra / Azure AD), Okta and cloud providers such as AWS implement these patterns in their Zero Trust architectures, treating identity as the first pillar.

From Network Perimeter to Identity-First Security Architecture
Traditional perimeter security vs. identity-centric security
Traditional perimeter security assumes “inside = trusted, outside = untrusted”, while identity-centric security continuously verifies each identity and its context, regardless of location or network. Instead of building taller walls, you enforce policies as close as possible to the identity and the data.
Traditional perimeter controls
Firewalls and IP allowlists
VPN concentrators and split tunnelling
Network Access Control (NAC)
Flat internal networks with broad lateral movement
Identity-centric security controls
Central IAM, SSO and federation
Multi-factor authentication (MFA) enforcement on risky access paths
Role-based and attribute-based access control (RBAC/ABAC)
Zero Trust Network Access (ZTNA) and device posture checks
PAM vaults and brokered access for privileged roles
This shift doesn’t eliminate the need for firewalls or VPNs in the US, UK or EU it simply means they’re supporting layers, not the main perimeter.
Why legacy perimeters fail for hybrid, remote and cloud workforces
Legacy network-centric models break down in modern environments because.
Stolen VPN credentials give attackers “valid” access that bypasses many controls; from there, flat networks and shared admin accounts enable lateral movement.
Access from unmanaged or partially managed devices creates blind spots if you rely solely on network checks.
SaaS and cloud admins often sit entirely outside your internal network, making traditional segmentation meaningless.
Partner and contractor identities are hard to manage with static firewall rules.
For a remote workforce spread between Manchester, Austin and Munich, it’s nearly impossible to maintain clean IP-based boundaries that map to real business risk.
Benefits of an identity-centric security strategy
Done well, an identity-first strategy delivers.
Reduced breach risk
Focusing on MFA, least-privilege roles, PAM and continuous access review directly tackles the credential and privilege abuse patterns that dominate breaches.
Better user experience
SSO and passwordless flows reduce login friction; users see step-up MFA only when risk increases rather than on every single action. Okta reports that by 2023, MFA was used by around 64% of users and 90% of admins — adoption that’s only growing.
Easier regulatory alignment
Identity-centric controls map cleanly to IAM expectations in frameworks like SOC 2, ISO 27001, HIPAA, PCI DSS, GDPR/DSGVO and NIS2.
IAM and Identity Security Best Practices in an Identity-First World
Core IAM best practices every organisation should implement
The IAM best practices that most reduce identity-based attacks in cloud environments are strong MFA, least-privilege roles, just-in-time elevation and continuous access review. Applied consistently, they give you a robust identity perimeter even before advanced tooling.
Start with a baseline checklist:
Central SSO and federation across critical apps (HRIS, CRM, ERP, cloud consoles, developer tools).
Multi-factor authentication (MFA) enforcement for all admins, remote access and sensitive apps including passwordless where feasible.
Strong password and session policies where passwords remain: long, unique and supported by technical safeguards rather than user discipline alone.
Standardised joiner mover leaver (JML) processes integrated with HR so accounts are created, updated and removed automatically.
Regular access reviews for high-risk systems and roles, with clear ownership.
In UK contexts, this aligns with the ICO’s guidance on “appropriate technical and organisational measures” for secure processing; in the US, it supports HIPAA, SOX and PCI DSS control expectations around access.
Identity security best practices beyond basic IAM
Beyond baseline IAM, you’ll want additional identity-centric security layers.
Privileged access management (PAM) for root, domain admin, cloud admin and “break-glass” accounts. Tools from vendors like ManageEngine or enterprise PAM suites provide vaulting, session recording and just-in-time elevation.
Identity threat detection and response (ITDR) to spot anomalous logins, impossible travel, privilege escalations and risky OAuth grants; CrowdStrike and other EDR/XDR vendors are increasingly adding identity telemetry to their stacks.
Zero Trust Network Access (ZTNA) that binds access to identity and device posture, not just IP, often replacing or augmenting legacy VPNs.
Together, these tighten your identity perimeter and give your SOC richer signals than network logs alone.
Operationalising IAM best practices across teams and tools
Identity-first security fails when it’s “owned by nobody and used by everyone”. To make it stick:
Align security, IT and HR on a common identity lifecycle and data model.
Define a RACI for IAM ownership: who owns policies, platforms, integrations and approvals.
Standardise request and approval workflows for access, with SLAs and audit trails.
Set an access review cadence quarterly for high-risk apps, annually for lower-risk ones.
Many organisations in the US, UK and EU bring in external partners for IAM assessments or managed services. Firms like Orange Cyberdefense or Intragen focus on IAM, while training bodies such as EC-Council help upskill internal teams.
Cloud IAM Best Practices and Zero Trust Identity in Practice
Cloud IAM best practices across multi-cloud and SaaS
In AWS, Azure and GCP, your Cloud IAM configuration often is your security model. Good patterns include:
Use cloud-native IAM (roles, policies, conditional access) integrated with a central directory (e.g., Entra ID or Okta) rather than managing islands of identities in each cloud account.
Consolidate SaaS identities with SSO and federation to reduce password sprawl and shadow IT; Okta and similar providers’ reports show the number of SaaS apps per organisation continues to climb.
Design least-privilege roles for IaaS/PaaS: narrow, task-specific roles; resource-scoped policies; explicit separation of duties.
Maintain “break-glass” accounts with out-of-band MFA and strict procedures.
For US enterprises, this often means mapping IAM controls to SOC 2 and ISO 27001 for cloud workloads; in Germany and the wider EU, it must also line up with GDPR data minimisation and access governance expectations. (EUR-Lex)
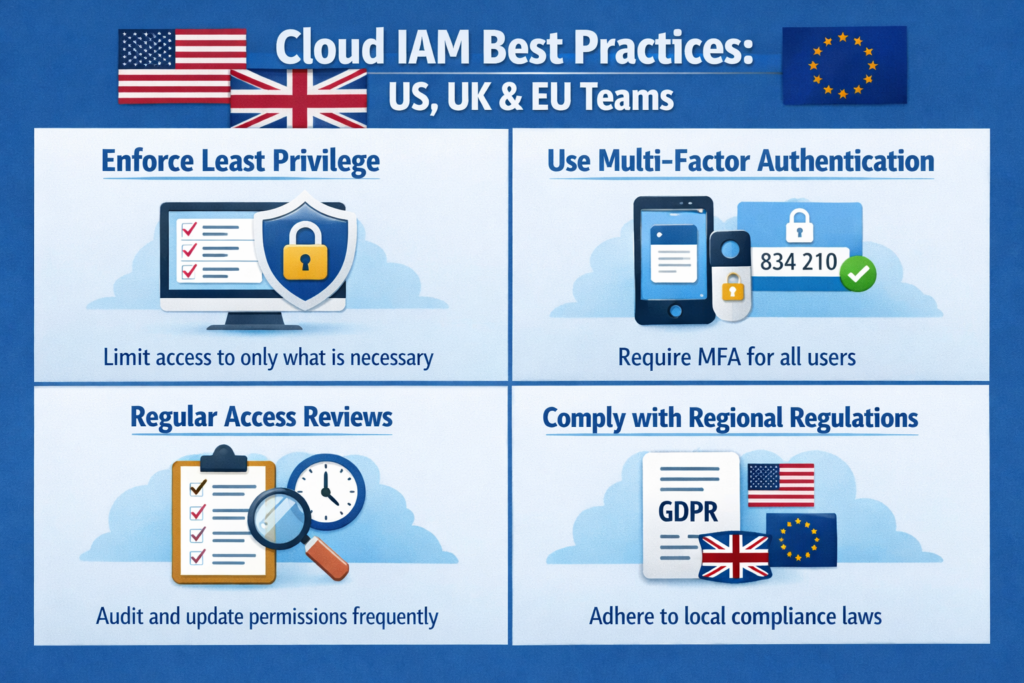
Zero Trust identity and access management patterns
Zero Trust identity in practice looks like.
Risk-based access policies that adapt MFA requirements and session limits based on device, geolocation, IP reputation and behaviour.
Continuous session evaluation revoke or re-authenticate when risk changes rather than waiting for session expiry.
Mapping users, devices and workloads into sensitivity tiers (e.g., public, internal, confidential, highly restricted) and aligning IAM policies accordingly, instead of relying only on VLANs and subnet tags.
Security score platforms like Security Scorecard increasingly factor identity exposure (e.g., leaked credentials, misconfigured SSO) into external cyber-risk ratings, making identity-first Zero Trust patterns visible at board level.
Securing remote and hybrid workforce identities
For remote and hybrid workforces in the US, UK and EU.
Integrate endpoint and device posture (EDR, MDM) with IAM and ZTNA to block or restrict access from non-compliant devices without killing productivity.
Enforce SSO and MFA everywhere remote users log in VPN, ZTNA, cloud consoles, HR, finance and collaboration tools.
Handle contractors, partners and third-party admins with time-bound, scoped access, preferably via dedicated identities or just-in-time access brokers.
In the UK public sector and health providers such as the NHS, these measures can be layered on top of existing clinical and line-of-business systems without disrupting critical services, by placing identity-aware proxies and ZTNA in front of legacy apps.
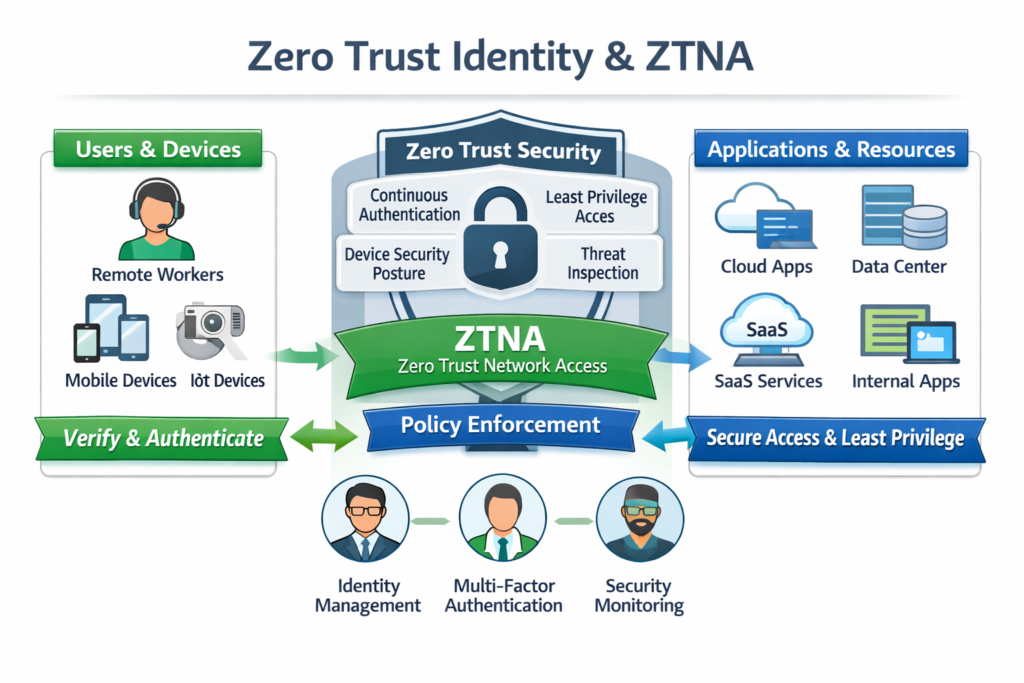
Regional and Compliance-Driven Identity Security (US, UK, Germany, EU)
IAM for US-regulated industries (Healthcare, Finance, SaaS)
US-regulated sectors have well-defined expectations.
HIPAA demands strong authentication, access controls and audit logs for ePHI; modern IAM supports this with MFA, RBAC and immutable logging.
PCI DSS requires unique IDs, least privilege and secure authentication for anyone with cardholder data access.
SOC 2 / ISO 27001 place heavy emphasis on access governance and change control, which IAM platforms support via central policies and reviews.
Think of a New York City healthcare provider: tying EHR access to central IAM with enforced MFA, JML automation and PAM for database admins simultaneously supports HIPAA, SOC 2 and resilience expectations.
IAM best practices for UK enterprises and public sector
For UK enterprises and public bodies:
UK-GDPR and ICO guidance call for “appropriate technical and organisational measures” identity-centric IAM, ZTNA and PAM are exactly that.
FCA-regulated firms and Open Banking ecosystems must prove strong customer authentication, granular entitlements and detailed audit trails; IAM best practices for UK financial services and Open Banking emphasise centralised customer identity, consent management and robust admin controls.
UK public sector organisations, including local councils and health trusts, can modernise IAM by layering SSO, MFA and ZTNA over existing systems instead of big-bang replacements.
Regulators like the FCA and the ICO increasingly expect identity-centric security in assessments and guidance, especially as identity-related breaches trend upward.
IAM in Germany and the wider EU.
For Germany and the EU.
IAM Best Practices für DSGVO und NIS2 in der EU include strong authentication, minimal privileges, detailed logging and regular access reviews, all designed for auditability.
Under DORA, BaFin-regulated banks and financial institutions must show operational resilience, including identity-related incident response and recovery.
Data residency and Schrems II require careful handling of identity data, often using EU data centres and regionalised logs.
For a BaFin-supervised bank in Frankfurt, this means IAM architectures that keep EU identity data in-region, use EU sovereign cloud options and maintain detailed evidence for access decisions and identity changes that will stand up to regulatory scrutiny.
Roadmap, Metrics and Next Steps for Identity-First Security
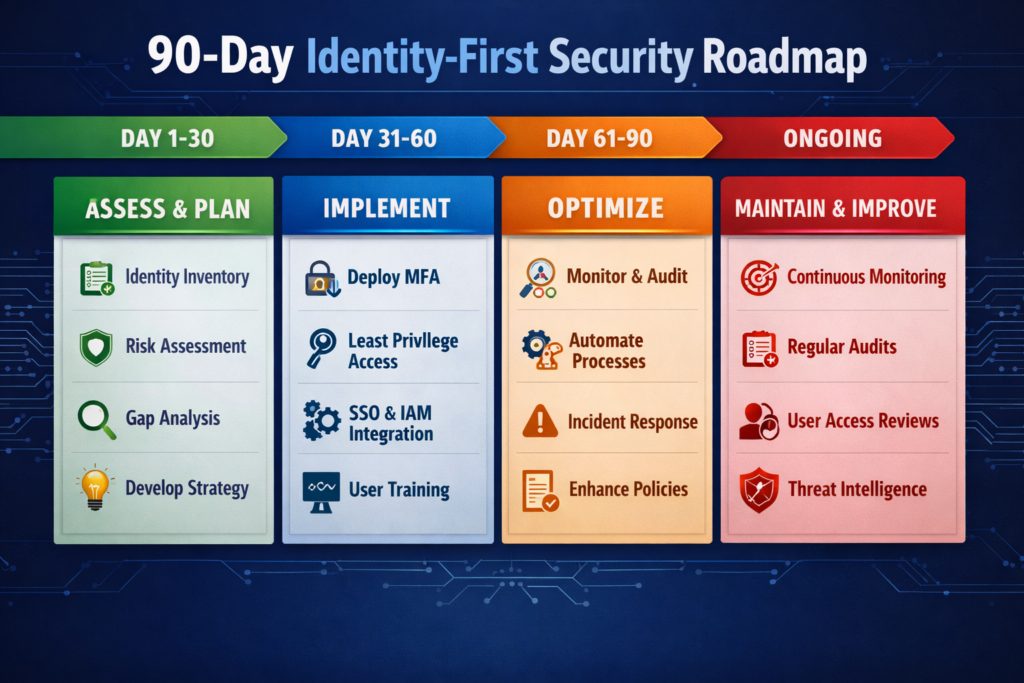
A 90-day roadmap to an identity-first security strategy
A pragmatic 90-day plan to move towards identity-first security.
Discover identities and access (Days 1–30)
Inventory human identities (employees, contractors, partners) and machine identities (service accounts, APIs, AI agents).
Map critical applications (SaaS, cloud, on-prem) and which identities can reach them.
Identify “toxic combinations” of access (e.g., admin + finance approvals)
Prioritise quick wins (Days 31–60)
Enforce MFA for all admins and high-risk apps.
Roll out SSO for top-critical apps in HR, finance and developer tooling.
Fix obvious JML gaps especially dormant or orphaned accounts.
Design your target architecture (Days 61–90)
Define an identity-centric security architecture aligned to Zero Trust and NIST SP 800-207.
Plan Cloud IAM hardening, ITDR integration and PAM rollout.
Draft an IAM operating model (RACI, processes, tools) for the next 12–24 months.
This phased approach lines up with Zero Trust and cloud identity guidance from vendors and standards bodies.
How to measure identity-centric IAM effectiveness over time
Security teams should measure identity-centric IAM using coverage (who is under control), quality (least privilege, clean roles) and outcome metrics (fewer identity breaches, faster response).
Example KPIs.
Coverage: % of users under SSO; % of users and admins with enforced MFA; % of apps integrated.
Quality: number of dormant accounts closed per month; ratio of privileged to standard accounts; PAM adoption for admin tasks.
Outcomes: reduction in identity-related incidents year-on-year; mean time to detect/respond (MTTD/MTTR) for identity threats; audit findings related to IAM.
You can also benchmark yourself using external ratings from platforms like Security Scorecard and results from internal or third-party red-team exercises.
When to invest in IAM platforms, managed services and assessments
Consider investing in new IAM platforms, managed services or assessments when:
You’re scaling into multi-cloud or multiple regions (US + UK + EU) and manual IAM processes can’t keep up.
Regulatory audits (e.g., SOC 2, ISO 27001, DORA, NIS2) highlight recurrent identity issues.
You’re going through M&A, fast headcount growth or large-scale SaaS/cloud adoption.
Evaluation criteria should include:
Integration with Entra, AWS, Okta and your current stack.
Support for Zero Trust patterns (risk-based policies, ZTNA, ITDR)
Regional data residency and compliance features for GDPR, UK-GDPR and sectoral rules.
If you’re not sure where to start, an IAM maturity assessment or pilot with a trusted IAM consultancy can de-risk the journey. Identity-first security articles for example an “Identity-First Security: From Zero Trust to Resilience” guide pair well with this identity is the new perimeter IAM playbook when planning modern architectures. (Mak it Solutions – Identity-First Security)
Key Takeaways
Identity not the network is now the most reliable perimeter for modern, cloud-heavy, hybrid workforces.
An identity-centric security architecture combines SSO, MFA, PAM, ITDR and ZTNA to continuously verify users, devices and workloads.
Cloud IAM misconfigurations and over-privileged roles are a major source of risk; least privilege and just-in-time elevation are non-negotiable.
US, UK and EU regulations (HIPAA, PCI DSS, GDPR/DSGVO, NIS2, DORA) increasingly expect strong IAM with auditability and clear ownership.
A 90-day roadmap focused on discovery, quick wins and target architecture design can kick-start an identity-first, Zero Trust programme.
Metrics around coverage, quality and outcomes help prove that “identity is the new perimeter” is delivering real risk reduction and compliance value.
If you’re looking at your current VPN-centric setup and thinking “this won’t survive our next audit or incident”, you’re not alone. The good news: most of the building blocks for identity-first security are already in your stack they just need to be wired together properly so that “identity is the new perimeter” becomes reality rather than a slogan.
The team at Mak It Solutions works with security and IT leaders across the US, UK, Germany and the wider EU to build secure web, mobile and analytics platforms that respect modern IAM and Zero Trust patterns from day one. If you’d like a pragmatic 90-day roadmap for your own environment, reach out to our experts for a scoped IAM and identity-first architecture assessment.( Click Here’s )
FAQs
Q : How does identity-first security change the role of traditional firewalls and VPNs?
A : Identity-first security doesn’t remove the need for firewalls and VPNs, but it changes their job. Instead of being the primary perimeter, they become supporting controls that protect infrastructure and reduce noise while IAM, SSO, MFA and ZTNA become the main enforcement points. In practice, this means you still segment networks and use VPNs where needed, but access decisions are driven by user, device and workload identities, with continuous verification and least privilege. Over time, many organisations gradually replace broad VPN access with granular, identity-aware ZTNA.
Q : What are practical first steps if our organisation still has weak IAM processes?
A : Start with visibility and a few high-impact changes. Inventory your identities and critical apps, then enforce MFA for administrators and remote access as quickly as possible. Next, centralise authentication for a handful of business-critical apps behind SSO and clean up joiner mover–leaver processes so dormant accounts are removed promptly. Finally, define ownership (who runs IAM day-to-day) and set up regular access reviews for high-risk systems. You can add PAM, ITDR and ZTNA once this foundation is working smoothly.
Q : How can small and mid-size businesses adopt Zero Trust IAM without enterprise budgets?
A : SMBs don’t need big-ticket platforms to benefit from Zero Trust IAM. Most cloud and SaaS platforms already include built-in MFA, basic conditional access and role-based permissions that can be enabled with configuration rather than heavy engineering. Start by enforcing MFA everywhere, using SSO for your top 10–20 apps, and tightening admin roles so only a small group has powerful privileges. Then, use simple policies (e.g., block risky geos, restrict logins from unknown devices) and regularly review access. Managed security providers can help extend these basics into a more complete Zero Trust design without the cost of a full internal team.
Q : What should security teams look for when comparing IAM and SSO platforms?
A : When comparing IAM and SSO platforms, look beyond checkbox features. Evaluate how well they integrate with your existing directories, cloud providers and key SaaS apps, and whether they support Zero Trust patterns like risk-based policies, device posture and passwordless authentication. Check regional data residency options for US, UK and EU workloads, plus certifications like SOC 2 and ISO 27001. Also assess admin experience (policy as code, automation), ecosystem (PAM, ITDR, ZTNA integrations) and total cost of ownership over 3–5 years. A short proof-of-concept with a critical app set often reveals more than a long RFP.
Q : How do identity threat detection and response (ITDR) tools fit into an existing SIEM/SOC stack?
A : ITDR tools complement not replace your SIEM and SOC. They add specialised analytics and detections for identity events such as risky sign-ins, abnormal privilege escalations, suspicious OAuth grants and token theft attempts. In a mature setup, ITDR feeds high-quality alerts and context into your SIEM, which then orchestrates response playbooks (for example, forcing re-authentication, revoking sessions or locking accounts). SOC analysts gain richer, identity-aware telemetry and can correlate identity signals with endpoint, network and application logs for faster triage and containment.


