MDR vs SOC vs XDR: Saudi, UAE & Qatar Buyer’s Guide
MDR vs SOC vs XDR: Saudi, UAE & Qatar Buyer’s Guide
MDR vs SOC vs XDR: Saudi, UAE & Qatar Buyer’s Guide
For GCC security leaders, MDR, SOC and XDR are three different ways to run 24/7 cyber defence. MDR and SOCaaS give you outsourced analysts, playbooks and incident response, while XDR is the technology platform your own team (or your MDR/SOCaaS provider) operates.
In Saudi Arabia, the United Arab Emirates and Qatar in 2026, most banks, fintechs and government entities will get faster, more compliant protection with MDR or hybrid SOCaaS + XDR models rather than trying to build a full in-house SOC from scratch.
For CISOs and CIOs in Saudi Arabia, the UAE and Qatar, MDR vs SOC vs XDR has become a board-level 2026 decision, not just a technical architecture debate. Ransomware gangs, supply-chain attacks and nation-state campaigns are testing every gap in cyber security operations outsourcing in GCC markets, especially in regulated sectors like banking, fintech and government.
At the same time, regulators such as the Saudi Central Bank (SAMA), NDMO/NCA, the Telecommunications and Digital Government Regulatory Authority (TDRA) and Qatar Central Bank (QCB) have tightened expectations around monitoring, logging and incident response maturity. Their cybersecurity and technology-risk frameworks require structured controls, evidence and 24/7 visibility across critical systems and payment services.
By the end of this guide, you’ll know when to buy MDR, when to build or extend a SOC, and when to invest in XDR for your Saudi, UAE or Qatar environment including how each choice impacts data residency, Arabic support and your SAMA/TDRA/QCB compliance roadmap.
What MDR, SOC and XDR Really Mean for GCC Security Leaders
Quick definitions with a GCC lens
At board level, you can think of the models like this.
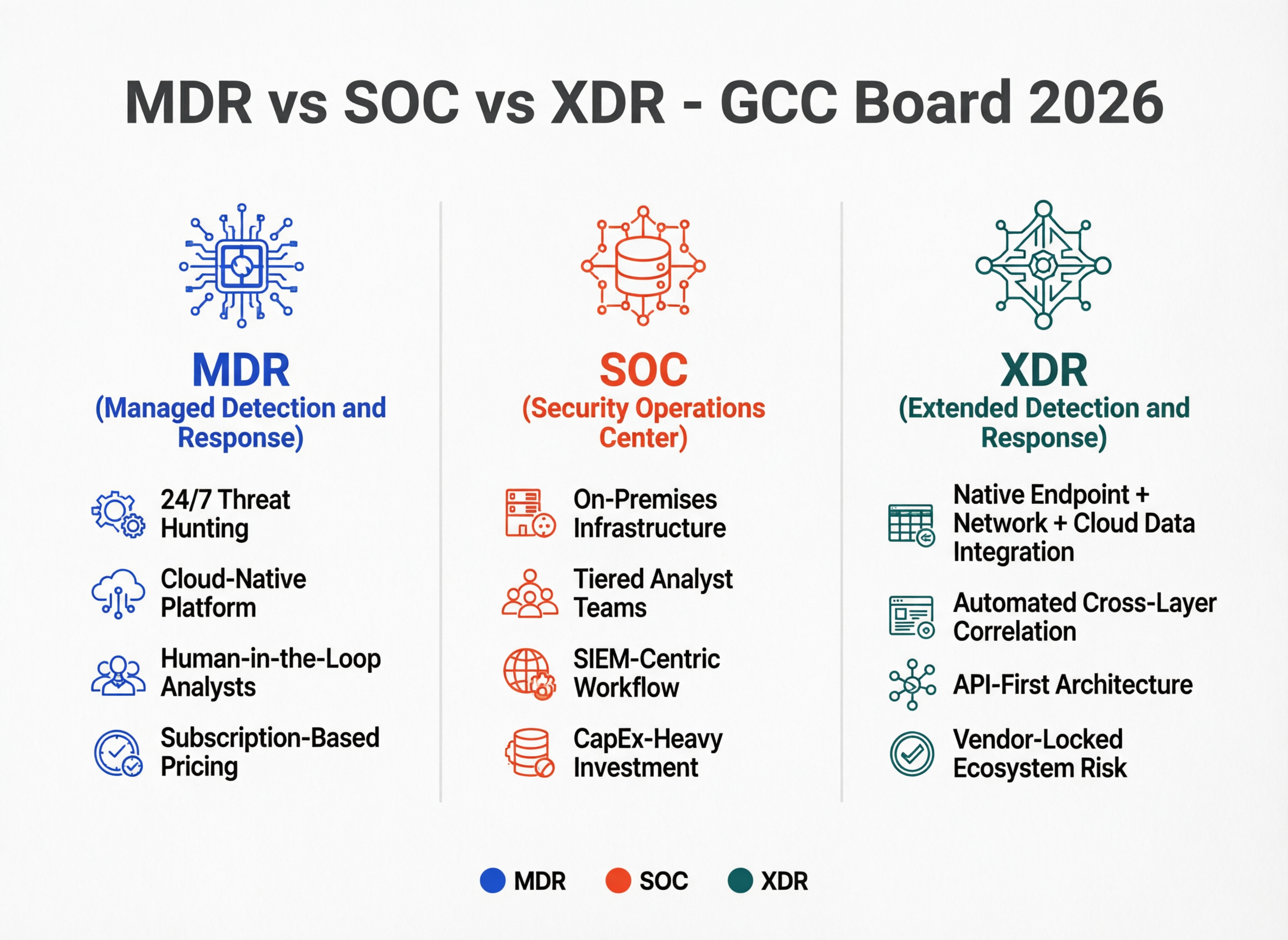
SOC (Security Operations Center)
The team, processes and tooling that monitor threats, triage alerts and coordinate incident response, whether in-house or outsourced.
SOCaaS (SOC as a Service)
A managed security services provider in the GCC or globally delivering SOC outcomes as a service (people + process + tools), usually on a subscription basis.
MDR (Managed Detection and Response)
A specialised service where an external provider delivers high-quality detection, a 24/7 threat-monitoring service in Middle East time zones, and hands-on guided response, often using its own EDR/XDR stack.
XDR (Extended Detection and Response)
A platform that unifies telemetry from endpoints, network, cloud and identity into a single analytics and response plane; your SOC (in-house or MDR/SOCaaS) still has to operate it.
Global definitions don’t fully capture GCC realities like Arabic-first support, strict data residency (especially under NDMO and PDPL), and the need to align with sector regulations in Riyadh, Dubai, Abu Dhabi and Doha.
MDR vs SOC vs XDR: core differences in responsibility split
A simple way to think about SOC vs SIEM vs XDR vs MDR is: who owns what?
Technology stack
In-house SOC: you buy and run SIEM/XDR, EDR, NDR, SOAR.
MDR/SOCaaS: the provider may bring its own stack or co-manage yours.
XDR alone: you buy the platform; your team still has to watch the screens.
Detection content & tuning
In-house SOC: you own detection engineering and threat hunting.
MDR/SOCaaS: the provider designs and maintains most rules and playbooks.
Monitoring & incident response
In-house SOC: your team runs 24/7 shifts.
MDR/SOCaaS: the provider delivers continuous monitoring, incident response and threat-hunting services, often with SLAs for triage and containment.
Compliance reporting
In-house SOC: you build regulator-ready dashboards and reports.
MDR/SOCaaS: the provider supplies mapped reports (e.g., SAMA, TDRA, QCB controls) plus evidence packs; you still own final sign-off.
In short: XDR is a platform you operate; MDR/SOCaaS are outcomes you buy.
What is the difference between MDR, SOC and XDR for Saudi and UAE companies?
For Saudi and UAE companies, the key difference is who runs day-to-day security operations. MDR and SOCaaS give you outsourced experts who monitor, investigate and respond 24/7, while XDR is the toolset that your own SOC (internal or external) uses to see and stop threats across endpoints, networks, cloud and identities.
If you only remember one thing: MDR/SOCaaS = “hire a team to protect you”, XDR = “buy a powerful console your team must operate”. For KSA and UAE environments with Microsoft-heavy stacks (Defender XDR, Sentinel), lots of on-prem legacy and multi-cloud workloads, the most successful 2026 architectures combine XDR with MDR or SOCaaS rather than relying on XDR alone.
How MDR, SOC and XDR Fit Saudi, UAE and Qatar Environments in 2026
Saudi reality: SAMA, NDMO and lack of senior SOC talent
In Saudi Arabia, SAMA’s Cybersecurity Framework, NDMO requirements and NCA controls have pushed banks, insurers and fintechs to formalise monitoring, logging and incident response.
Yet many organisations in Riyadh and Jeddah still struggle to hire and retain Tier-2/3 analysts, threat hunters and incident commanders.
This gap is driving strong demand for MDR and SOCaaS. Regional banks and government entities increasingly outsource 24/7 operations while keeping governance, risk and compliance in-house. For Saudi-friendly MDR services with Arabic support, it’s common to demand in-country log storage, clear SAMA mapping and support for hybrid on-prem and AWS Bahrain workloads.
UAE landscape.
United Arab Emirates organisations especially in Dubai, Abu Dhabi, DIFC and ADGM are typically more cloud-first and multi-cloud. Microsoft Defender XDR and Sentinel are widely adopted, alongside Azure UAE Central, AWS UAE and sometimes GCP.
Here, the trend is SOCaaS plus XDR. A managed provider operates Sentinel/Defender or other XDR platforms, delivering outcomes like 24/7 monitoring and automated response, while internal teams focus on governance and integration with business systems such as UAE Pass and national digital services.
For many UAE buyers, the winning model is “no full in-house SOC; strong SOCaaS anchored on XDR.”
Qatar focus.
In Qatar, especially Doha, national telcos and global partners run large SOCs serving government, BFSI and critical infrastructure. These SOCs are increasingly AI-driven, using machine learning to correlate events across OT/ICS, cloud and banking platforms.
For many Qatari entities, MDR and XDR are extensions to a national or telco SOC. XDR provides local visibility in their own tenant (e.g., GCP Doha, Azure regions), while MDR providers focus on niche areas like OT threat hunting or specialised incident response.
This hybrid, layered approach aligns well with QCB technology-risk expectations and Qatar’s smart-nation initiatives.
Mapping MDR, SOC and XDR to SAMA, TDRA and QCB Rules
How do MDR, SOC and XDR options map to SAMA, TDRA and QCB cybersecurity requirements?
At a high level.
SAMA / NDMO (Saudi)
Expect robust governance of logs, access, incident response and regular maturity assessments. An MDR or SOCaaS model aligned to SAMA’s Cybersecurity Framework can provide continuous monitoring, incident playbooks and evidence for audits, while XDR strengthens technical controls for detection and response.
TDRA and sector regulators (UAE)
Emphasise resilience of digital services, telecoms and government platforms. SOCaaS or MDR with strong SLAs, data-loss controls and integration to cloud services helps document compliance and support UAE digital-government objectives. (tdra.gov.ae)
QCB & Qatar PDPL (Qatar)
Focus on protecting banking and payment systems, personal data and technology risks. MDR/SOCaaS help provide continuous logging and monitoring aligned with QCB regulations, while XDR technologies enforce controls like anomaly detection, access monitoring and incident traceability.
This section is guidance, not legal advice; final control choices must be validated with your legal, risk and compliance teams.
Data residency: where logs, telemetry and incidents actually live
For SAMA-, TDRA- or QCB-regulated entities, data residency is often the deal-breaker. You need clarity on.
Where SIEM/XDR and EDR/NDR telemetry is stored (e.g., in-country vs EU/US).
Whether MDR/SOCaaS analysts access data directly or via privacy-preserving views.
How incident tickets, evidence and timelines are stored for regulator reviews.
Good practice in 2026 is to use regional cloud regions (AWS Bahrain, Azure UAE Central, GCP Doha) or sovereign data centres for log storage, with clear data-processing agreements and cross-border transfer clauses. Many GCC buyers now include explicit “no raw log export outside KSA/UAE/Qatar without approval” language in MDR/SOC contracts.
Arabic UX, reporting and regulator-ready evidence
For boards and regulators across the GCC (including Kuwait, Bahrain and Oman), Arabic matters. Dashboards, alerts and executive reports that are bilingual (Arabic/English) make it far easier to brief audit committees, respond to regulator RFIs and align with national strategies like Saudi Vision 2030.
When evaluating MDR, SOCaaS or XDR providers, insist on:
Arabic-capable dashboards for senior leadership.
Regulator-mapped reports (e.g., SAMA domains, TDRA controls, QCB technology-risk areas).
Exportable evidence packs describing incidents, root cause and lessons learned in clear language.
When to Choose MDR vs SOC vs XDR in the GCC.
Why are many GCC organisations replacing traditional SOC builds with MDR services?
Many GCC banks, government agencies and enterprises are replacing the idea of a 20-person in-house SOC with MDR that can be live in 60–90 days. Instead of spending 18–24 months recruiting, training and retaining senior analysts in Riyadh or Dubai, MDR gives immediate 24/7 coverage, ready-made playbooks and proven threat-hunting capabilities. (SentinelOne)
In practice, this means faster time-to-detection, less alert fatigue and clearer accountability. MDR is especially attractive when cyber security operations outsourcing in GCC markets is cheaper and more reliable than trying to keep a full night-shift team on your own payroll.
When XDR alone is not enough and when it’s exactly right
Buying an XDR platform without MDR or SOCaaS often fails because.
No one tunes the rules or enriches alerts.
There is no 24/7 human monitoring.
Incident response responsibility is unclear.
However, for mature SOC teams (for example, a national oil & gas SOC in Abu Dhabi or a government SOC in Riyadh), XDR is exactly right. It unifies telemetry, speeds correlation and supports automation across SIEM, EDR and cloud.
In such cases, XDR amplifies an already strong SOC instead of replacing MDR.
How can a Saudi or UAE company combine MDR and XDR with an existing in-house SOC?
Hybrid patterns that work well in the GCC include.
In-house SOC + external MDR for Tier-2/3
Your internal team handles Tier-1 triage and governance, while MDR experts perform deep investigations, proactive threat hunting and incident response on complex cases.
Central XDR + MDR-operated playbooks
You standardise on XDR in KSA/UAE cloud regions; the MDR provider runs detection rules and response workflows, and your team focuses on business context and regulator relationships.
This is particularly powerful for fintech, government, retail, logistics and oil & gas organisations that need both intimate local knowledge and access to global threat-intelligence and playbooks.
Cost, Talent and Time-to-Value Across MDR, SOC and XDR
Cost drivers in the GCC.
Typical cost drivers in Saudi, UAE and Qatar include.
Platform licences SIEM/XDR, EDR/NDR, SOAR and threat-intelligence feeds.
Headcount L1–L3 analysts, engineers, a SOC manager and an incident commander.
Operations overhead 24/7 shifts, office space, training and certifications.
For many mid-size banks, fintechs and government entities, MDR/SOCaaS is an OPEX-friendly option. You pay a predictable subscription instead of building a large permanent team. That frees capital to invest in secure digital platforms, from web applications to mobile channels and data platforms.
SOC vs SOCaaS vs MDR in the GCC.
A simple decision lens for 2026
Choose in-house SOC when you have strong existing talent, high sensitivity and strategic reasons to keep everything internal.
Choose SOCaaS when you want broad coverage (log monitoring, vulnerability, basic response) with predictable cost and clear SLAs.
Choose MDR + XDR when you need advanced detection and response quickly but don’t have senior analysts or threat-hunting capacity.
Red flags for building a SOC in-house include no plan to retain senior analysts, no 24/7 budget or unclear ownership of incident response. In these cases, MDR or SOCaaS is usually safer.
Typical 2026 timelines.
Realistic ranges for GCC entities in 2026.
RFP/RFQ & procurement around 3–9 months for government and critical infrastructure; roughly 2–6 months for the private sector.
Technology deployment about 1–3 months for cloud-based XDR; 3–6 months when heavy on-prem integration is required.
Onboarding to “first critical incident detected and responded” often within 30–90 days of MDR/SOCaaS go-live when log sources are integrated properly.
As with any security investment, these are indicative ranges, not guarantees. Actual timelines will depend on your internal processes and vendor selection.
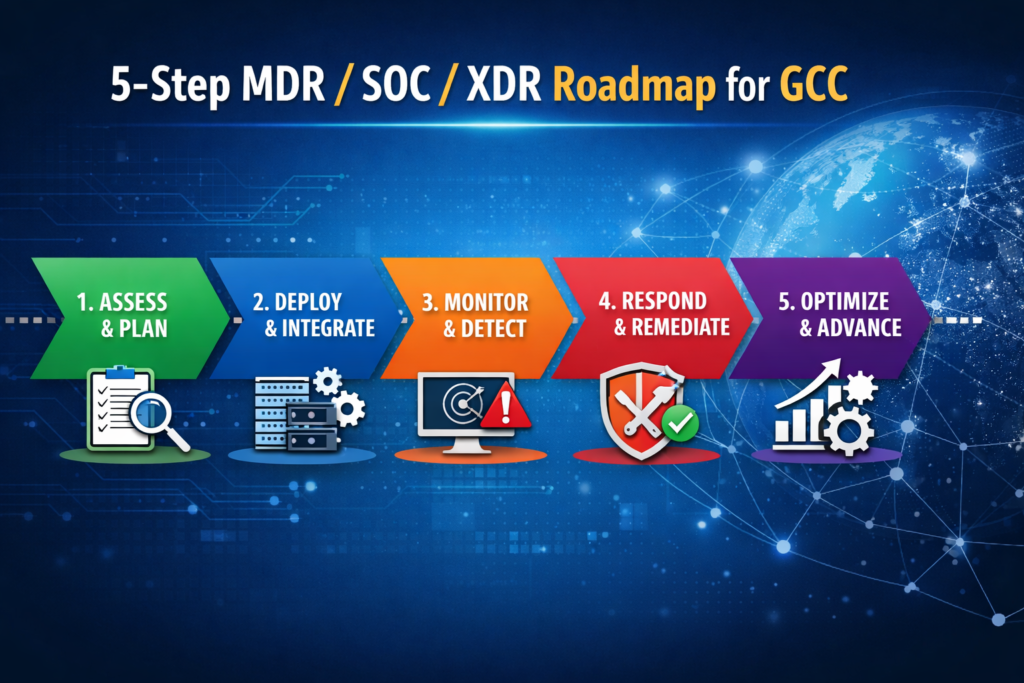
2026 Roadmap for GCC CISOs.
5-step approach to choosing MDR vs SOC vs XDR in 2026
Map regulator and data-residency requirements
Capture all relevant frameworks (SAMA/NDMO/NCA, TDRA, QCB, PDPL and any sector rules) and note in-country logging and data-processing obligations.
Audit current tooling
Identify what you already have (SIEM, EDR, NDR, cloud security, identity protection) and where visibility is weak across KSA, UAE and Qatar environments.
Assess team skills and coverage
Be honest about 24/7 gaps, detection-engineering capacity and incident-response readiness. Map which hours and skills you can realistically cover in-house.
Shortlist MDR/SOC/XDR mixes
Evaluate combinations that fill your technical and human gaps while meeting data-residency expectations (e.g., AWS Bahrain, Azure UAE Central, GCP Doha).
Run PoCs and GCC reference checks
Pilot shortlisted providers, validate SLAs and dashboards, and speak with reference customers in Riyadh, Dubai, Abu Dhabi and Doha before committing.
What should a Qatar or GCC CISO consider before choosing MDR vs SOC vs XDR in 2026?
Key checklist items.
Data residency and in-country logging options.
Arabic UX and reporting for executives and regulators.
Clear mapping to SAMA, TDRA, QCB and PDPL controls.
Integration with your existing SIEM/XDR, identity and cloud platforms.
SLAs for detection, response and containment ownership.
Clarity on who talks to regulators and customers during major incidents.
Example target-state architectures for Saudi, UAE and Qatar
KSA bank under SAMA
In-country SIEM/XDR hosted on AWS Bahrain or local data centres; MDR providing 24/7 monitoring and incident response; a small in-house SOC team owning governance, Open Banking KSA control mapping and executive reporting.
UAE cloud-first startup
XDR as core platform (for example, Defender XDR) in Azure UAE Central; MDR as a service for advanced detection and response; no full SOC, but a lean internal security team focused on secure development and digital-ID integrations like UAE Pass.
Qatar critical infrastructure
A national or telco SOC for baseline monitoring; local XDR deployment in GCP Doha; specialist MDR focusing on OT/ICS threat hunting and incident response aligned with QCB and national cybersecurity frameworks.
For the wider GCC (including Kuwait, Bahrain and Oman), these patterns are flexible starting points rather than rigid blueprints.
If you’re a CISO or technology leader in Saudi, UAE or Qatar and need to decide MDR vs SOC vs XDR for 2026, you don’t have to map this journey alone. The team at Mak It Solutions already helps organisations design secure, cloud-ready platforms, from web and mobile applications to analytics portals.
Book a consultation to explore how your existing digital stack websites, portals, mobile apps and data platforms can be aligned with the right MDR/SOC/XDR strategy for your regulators, budget and talent realities.
FAQs
Q : Is MDR alone enough to satisfy SAMA and NDMO expectations for Saudi banks?
A : MDR can strongly support SAMA and NDMO expectations by providing 24/7 monitoring, incident response and structured reporting, but it is not enough on its own. SAMA’s Cybersecurity Framework expects banks to maintain governance, risk management, oversight and periodic assessments internally, even when operations are outsourced.
Saudi banks typically pair MDR with clear internal accountability, documented policies and periodic audits against SAMA/NCA controls. MDR is a powerful operational layer, but SAMA still views the bank’s board and executives as the ultimate owners of cyber risk.
Q : How should a Dubai or Abu Dhabi company choose between SOC as a Service and MDR in 2026?
A : Companies in Dubai and Abu Dhabi should start by mapping business criticality, cloud footprint and TDRA or free-zone expectations. SOCaaS is ideal when you want broad log monitoring, vulnerability coverage and standard incident handling across multi-cloud environments. MDR is better when you need advanced, attack-focused detection and deeper incident response on top of XDR or EDR platforms.
Many UAE organisations combine both, using SOCaaS for wide coverage and MDR for high-priority assets. TDRA’s focus on resilience and digital-government maturity makes documented SLAs and evidence-rich reporting essential in either model.
Q : Can Qatar organisations keep all security logs inside Doha when using MDR or XDR providers?
A : Yes, many MDR and XDR providers now support in-country log storage in Qatar, especially using GCP Doha, Azure regions or local data centres. The key is to specify data residency clearly in contracts and ensure that log indexes, incident evidence and case data remain hosted under QCB-aligned controls.
Providers may still access telemetry remotely for investigations, but raw data does not have to leave the country. Qatar’s Data Handling and Protection and technology-risk regulations encourage robust logging, monitoring and access control; they don’t forbid using external providers as long as appropriate safeguards and governance are in place.
Q : What is a realistic MDR/SOC budget for a mid-size GCC fintech or payments company?
A : Budgets vary, but a mid-size fintech or payments company in Riyadh, Dubai or Doha will often allocate a low- to mid-single-digit percentage of annual revenue to security, with MDR/SOC as a significant line item. In practice, MDR or SOCaaS contracts may be cheaper than running a 24/7 internal SOC once salaries, turnover and tooling are considered.
Start by modelling platform licences, provider fees and the internal FTEs you still need for governance and compliance. In Saudi Arabia, alignment with SAMA and Saudi Vision 2030’s digital-economy goals often justifies investing more in security outcomes, not just tools. This is not financial advice; always model scenarios for your specific business.
Q : How can GCC governments ensure Arabic reporting and executive dashboards from MDR and XDR vendors?
A : Governments in KSA, UAE and Qatar should include Arabic reporting and dashboard requirements directly in RFPs, evaluation criteria and contracts. This means specifying bilingual SOC runbooks, board-level reporting templates and regulator-ready evidence in Arabic and English.
During PoCs, insist on demonstrations of Arabic UX, support for right-to-left layouts and localisation of incident categories. Bodies such as TDRA and national digital-government initiatives already emphasise accessible Arabic digital content, which you can reference when negotiating with vendors.