
The digital world has evolved far beyond simple passwords and static logins. In today’s hyper-connected environment, security and usability must go hand in hand. Whether you’re accessing a banking app, logging into your workplace dashboard, or verifying identity for an online purchase, authentication methods have to be strong enough to keep attackers out yet smooth enough to avoid frustrating users.
In 2025, authentication is no longer just a technical necessity it’s a cornerstone of trust. Businesses that fail to adopt modern authentication techniques risk not only breaches and data theft but also user abandonment. On the other hand, platforms that deploy advanced, user-friendly authentication methods see better engagement, loyalty, and long-term credibility.
This guide explores the modern authentication techniques that are reshaping cybersecurity, why they matter, and how organizations can implement them effectively to strike the perfect balance between security and convenience.
Why Traditional Passwords Are Fading
For decades, passwords were the primary gatekeepers of digital systems. But as cybercrime advanced, so did methods to crack or steal passwords. Weak or reused credentials account for a large percentage of data breaches, and phishing tactics make even strong passwords vulnerable.
Problems with passwords include:
- User fatigue from remembering multiple complex credentials
- Password reuse across platforms creating risk chains
- Credential stuffing attacks exploiting stolen login databases
- Social engineering making humans the weakest link
Because of these vulnerabilities, the modern web is shifting toward passwordless authentication, multi-factor verification, and continuous identity checks.
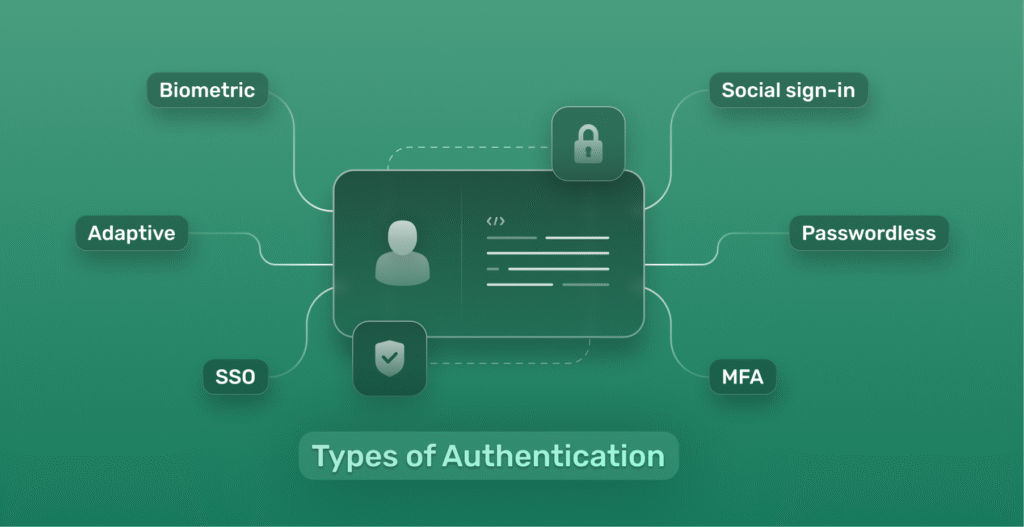
Core Modern Authentication Techniques
Multi-Factor Authentication (MFA)
MFA combines two or more factors something you know (password or PIN), something you have (device, token), and something you are (biometric).
- Example: Logging into a banking app with a password and then confirming with a fingerprint.
- Benefits: Stops most brute-force and credential-stuffing attacks.
- Challenge: Can frustrate users if poorly implemented.
Passwordless Authentication
Passwordless login eliminates the weakest security layer passwords replacing them with secure methods like.
- Magic links sent via email
- One-time passcodes (OTPs) delivered by SMS or authenticator apps
- Device-based cryptographic keys (WebAuthn, FIDO2)
Big tech companies are pushing passwordless adoption because it improves both security and user experience.
Biometric Authentication
Biometric factors are unique to individuals and difficult to forge. Common examples include:
- Fingerprint scanning (smartphones, laptops)
- Facial recognition (Face ID, Windows Hello)
- Voice recognition for call centers
- Behavioral biometrics (typing rhythm, swipe patterns)
Biometrics deliver speed and convenience, but they also raise privacy concerns and need strong encryption.
Adaptive and Risk-Based Authentication
Instead of applying the same login process for everyone, adaptive systems assess risk signals in real time:
- Device type
- Geolocation
- Time of access
- IP reputation
If a login attempt looks suspicious (e.g., accessing from a new country), the system requests extra verification.
Single Sign-On (SSO)
SSO allows users to log in once and access multiple apps securely without re-entering credentials. For example: logging into Google and seamlessly accessing Gmail, YouTube, and Drive.
- Benefits: Reduces password fatigue and IT support costs.
- Challenge: If SSO is compromised, all linked accounts are at risk.
Hardware Security Keys
Physical devices such as YubiKeys or FIDO2-compliant USB/NFC keys provide the strongest form of authentication. Since they require possession, they’re almost impossible to phish.
- Use case: Enterprises, developers, and security-conscious individuals.
- Challenge: Can be lost or misplaced.
Continuous Authentication
Unlike traditional login, continuous authentication verifies identity throughout the session. It relies on monitoring:
- Keystroke dynamics
- Mouse movement patterns
- Device usage habits
This ensures attackers who bypass the first login barrier can still be detected and blocked mid-session.
The Impact of Modern Authentication
a) Strengthening Security Posture
Modern authentication drastically reduces risks from phishing, brute force, and credential leaks. For organizations handling sensitive financial, healthcare, or government data, these measures are non-negotiable.
b) Improving User Experience
Smooth authentication like face unlock or one-tap verification removes friction. When security feels invisible, users are more likely to stay engaged and trust the platform.
c) Regulatory Compliance
Governments and industry standards increasingly require strong authentication. Examples include:
- PSD2 regulation in Europe demanding Strong Customer Authentication (SCA)
- HIPAA compliance for healthcare systems
- PCI DSS for payment card industries
d) Cost Reduction for Businesses
Password resets are costly in time and IT resources. By shifting toward passwordless and SSO systems, businesses cut support costs and boost productivity.
Real-World Applications
- Banking & Fintech: Multi-factor + biometrics for fraud prevention.
- E-Commerce: Passwordless logins with OTPs to reduce cart abandonment.
- Healthcare: Biometric + adaptive authentication to secure patient records.
- Corporate Workplaces: SSO with hardware keys for secure remote work.
Challenges in Adoption
Despite the benefits, organizations face hurdles such as:
- Integration with legacy systems
- Balancing privacy concerns with biometric storage
- Educating users about new authentication flows
- Costs of deploying enterprise-scale MFA or hardware keys
A gradual rollout, paired with employee/user training, often ensures smoother adoption.
Future of Authentication in 2025 and Beyond
Decentralized Identity: Users control their own digital identities using blockchain-based credentials.
AI-Powered Authentication: Systems learn from user behavior and flag anomalies instantly.
Passwordless by Default: Major platforms are pushing for a world where passwords disappear entirely.
Biometric Fusion: Combining multiple biometric factors (face + fingerprint) for maximum security.
The trend is clear authentication will continue to prioritize zero-trust principles, minimizing assumptions and verifying identity at every level.

Final Thoughts
Modern authentication techniques are not just about securing accounts; they’re about building a foundation of trust in the digital world. As cyber threats become more sophisticated, outdated methods like static passwords are simply not enough. Businesses, developers, and organizations must adapt to these changes to ensure both safety and usability.
In 2025, adopting methods such as passwordless login, biometrics, adaptive verification, and continuous authentication is a necessity, not a luxury. Those who embrace modern authentication will strengthen their security, simplify user access, and gain a competitive advantage by demonstrating that user protection is at the heart of their digital strategy.
FAQs
Q : Why are passwords considered weak in modern security?
A : Passwords are prone to reuse, phishing, and brute-force attacks. Even strong ones can be stolen. That’s why organizations are shifting to passwordless, biometric, and multi-factor methods for stronger protection.
Q : What is the biggest advantage of passwordless authentication?
A : It removes the need to remember or reset credentials, reducing user frustration while strengthening security. Passwordless systems use cryptographic keys or one-time codes, making them resistant to most cyberattacks.
Q : Can biometrics be hacked or stolen?
A : While harder to duplicate, biometrics can still be spoofed if not properly secured. That’s why encryption and secure storage are crucial. Combining biometrics with MFA further reduces the risks of identity fraud.
Q : How does adaptive authentication improve security?
A : Adaptive systems analyze context such as device type, location, and login time. If behavior looks unusual, extra verification is triggered. This balances user convenience with real-time threat detection.
Q : Is Single Sign-On (SSO) safe for businesses?
A : Yes, when combined with MFA and strong encryption. SSO reduces password fatigue and IT workload. However, organizations must protect the central login system since it controls access to multiple accounts.
Q : Do hardware security keys really stop phishing?
A : Absolutely. Security keys use cryptographic verification, making phishing almost impossible. Even if attackers trick users into entering credentials, they can’t access accounts without the physical key.
Q : What’s the future of authentication in the next decade?
A : Expect a passwordless-first world, AI-powered anomaly detection, and blockchain-based digital identities. Security will become seamless, with authentication running in the background without disrupting user experience.


