Multi Cloud Strategy in Middle East for GCC CIOs
Multi Cloud Strategy in Middle East for GCC CIOs

Multi Cloud Strategy in Middle East (GCC CIO Guide)
A multi cloud strategy in Middle East means running workloads across two or more cloud providers (hyperscalers, local and sovereign clouds) to balance compliance, resilience, cost and access to AI services. It is different from hybrid cloud because hybrid focuses on mixing on-premise and cloud, while multi cloud focuses on using several clouds at once including sovereign, regional and global platforms often within the same regulated architecture.
Inroduction
For GCC CIOs, “which cloud?” has quietly become “how many clouds and where exactly?”. Saudi Arabia, UAE, Qatar, Kuwait, Bahrain and Oman are all pushing Vision 2030-style agendas that demand AI, data platforms and always-on digital services. At the same time, PDPL, NDMO, TDRA, CRA and QCB rules are tightening how and where data can live.
The Middle East public cloud market alone is estimated at around USD 38–40 billion in 2024, with forecasts suggesting nearly 20% annual growth towards 2033. In that world, a multi cloud strategy in Middle East is no longer just a technical pattern it’s an executive-level hedge against regulatory risk, concentration risk and AI disruption.
This guide walks GCC CIOs through models, compliance, architecture, cost and a practical cloud workload migration roadmap tailored to Saudi, UAE and Qatar enterprises.
Why Multi-Cloud Strategy Matters in the Middle East
From Single Cloud to Multi-Cloud in GCC Enterprises
GCC enterprises are moving from “one primary cloud” to deliberate multi-cloud because no single provider can simultaneously optimize data residency, AI innovation, sector-specific compliance and commercial terms in every country. In Saudi Arabia, for example, banks may need a local sovereign zone for PDPL/NDMO-regulated data while also consuming advanced analytics from global hyperscale cloud regions in Middle East and Europe.
The cloud adoption in GCC market is estimated at over USD 40 billion in 2023, with projections above USD 150 billion by 2032, which reflects how deeply cloud is embedded in national digital strategies. Governments in Riyadh, Dubai, Doha and Muscat are also investing heavily in data center capacity and AI campuses, with some estimates suggesting regional data center power could triple in five years.
For CIOs in Saudi, UAE, Qatar, Kuwait, Bahrain and Oman, this means:
Regulators expect data localization and sovereignty requirements to be respected by design.
Boards expect resilience comparable to Tier-1 US, UK or Germany markets.
Product teams expect rapid access to AI services matching what’s available in London, Frankfurt or California.
Compliance, AI and Resilience
Across Riyadh, Dubai/Abu Dhabi and Doha, the same three drivers keep showing up in board decks:
Compliance & Data Residency
Saudi’s PDPL, NDMO standards and Cloud First Policy require many public and sensitive workloads to stay inside KSA, particularly in government and financial services.
UAE’s TDRA-led FedNet and National Cloud Security Policy push federal services into accredited sovereign and national clouds.
Qatar’s CRA Cloud Policy Framework and the new QCB Cloud Computing Regulation set strict rules for banking and telecom workloads in Qatar Cloud and local providers.
AI and Data Platforms
AI adoption in GCC organisations has jumped sharply – surveys show over 80% of respondents using AI in at least one function by 2025. This demands scalable GPU capacity, which often sits in specialised AI or hyperscale regions, not always the same location as sovereign/regional clouds.
Resilience & Sovereignty
With geopolitical risk and critical infrastructure considerations, governments are treating sovereign cloud as strategic infrastructure, similar to energy or transport. Multi cloud becomes the natural way to avoid putting all critical workloads into one jurisdiction, one provider or one supply chain.
Multi-Cloud vs Hybrid Cloud for Middle East Companies
A multi cloud strategy for Middle East companies means intentionally distributing workloads across two or more cloud providers for example a UAE sovereign cloud, a Saudi sovereign provider and one or more global hyperscalers to balance compliance, AI capabilities, cost and resilience. It is different from hybrid cloud, which focuses on combining on-premise or private cloud environments with a single public or sovereign cloud.
In practice
Hybrid cloud strategy in GCC is often “on-premise + one cloud” (e.g., a Riyadh data center plus KSA sovereign cloud for core banking).
Multi cloud is “two or more clouds” (e.g., stc Cloud + AWS + Ooredoo + OneCloud in UAE), even if on-premise is also present.
Many GCC enterprises end up with hybrid multi cloud: legacy core on-prem, sovereign cloud for regulated data, and global hyperscalers for AI and analytics.
Multi-Cloud Strategy Models for Saudi, UAE and Qatar Enterprises
Common Multi-Cloud Patterns in MENA
The most common multi-cloud patterns Mak It Solutions sees in GCC are:
Best-of-Breed SaaS Mix
CRM on one hyperscaler, HR/payroll on another, analytics on a third.
Popular when integrating US/UK/DE SaaS with local data residency controls and edge-caching in GCC.
Dual-Hyperscaler with Local Sovereign Anchor
Example:
KSA enterprise uses a sovereign cloud such as stc Cloud or Solutions by stc for PDPL-regulated data, plus Azure and AWS for analytics and global B2C workloads.
Regulated vs Unregulated Workload Split
Regulated workloads (banking, healthcare, government identity) stay in sovereign or local national clouds.
Less regulated workloads (marketing sites, B2C apps, internal tools) use global hyperscale regions in the Middle East and Europe.
AI/ML “Sidecar” Cloud
Especially in UAE and Qatar, enterprises are adding a dedicated AI cloud (for GPUs and model training) alongside their primary application cloud.
Multi-Cloud Strategy in Saudi Arabia for Enterprises
In Saudi Arabia, multi-cloud strategy is being shaped by Vision 2030, PDPL and a cloud-first public sector. CIOs in Riyadh, Jeddah and Neom typically:
Anchor sensitive workloads in KSA-hosted providers (stc Cloud, Solutions by stc, and other local sovereign platforms).
Use workloads zoning: PDPL/NDMO-classified “restricted” data never leave KSA; “internal” data may go to MEA/Europe regions; anonymised data can be processed globally.
Map architecture to SAMA’s outsourcing/cloud rules for banks and insurers, particularly around incident reporting, audit rights and data access by third parties.
Many Saudi CIOs benchmark their target state against EU GDPR and BaFin expectations, while tailoring for PDPL and NDMO similar rigor, different jurisdiction.
Multi-Cloud Strategy in UAE and Qatar Under National Cloud Policies
In the UAE and Qatar, national cloud policies and telecom regulators play a central role:
UAE (TDRA, National Cloud Security Policy)
FedNet provides a VMware-verified sovereign cloud backbone for federal entities.
TDRA and the Cybersecurity Council publish the National Cloud Security Policy, defining principles for secure cloud use.
e& enterprise’s OneCloud, powered by Oracle Alloy, and du’s National Hypercloud offer UAE-sovereign hyperscale platforms for regulated sectors such as healthcare (NHS-equivalent), banking and critical infrastructure.
Qatar (CRA, QCB, MCIT)
The CRA Cloud Policy Framework and Qatar Cloud initiative set overall rules for telecom and digital infrastructure.
The QCB Cloud Computing Regulation governs how banks and fintechs can use cloud, with explicit expectations for governance, risk and data protection.
Local providers such as Ooredoo Multi-Cloud Local Connect and MEEZA sovereign cloud provide in-country, regulated hosting options for critical workloads.
A multi cloud strategy here often means: one or two UAE/Qatar sovereign clouds for Tier-1 data, plus global hyperscalers for cross-border AI and analytics.
Compliance, Data Residency and Sovereign Cloud in GCC
Saudi PDPL, NDMO and SAMA Requirements in a Multi-Cloud Design
Saudi organisations design a compliant multi cloud architecture by classifying data under PDPL/NDMO, keeping restricted personal and government data inside KSA, and using SAMA-compliant contracts, logging and audit controls for any outsourced cloud services. In practice, that means sovereign KSA regions for regulated data, encrypted cross-border links for allowed transfers, and clear segregation between banking, government and commercial workloads.
Key design steps
Data classification first apply NDMO data management and personal data protection standards, which define how public, internal, confidential and restricted data must be handled. Anchor PDPL-regulated data in KSA sovereign or government clouds, following DGA’s cloud adoption guidelines for government agencies.
Align financial workloads with SAMA outsourcing rules, including rights to audit, incident notification SLAs and clear exit strategies for cloud providers.
Use end-to-end encryption, KSA-based key management, and strict admin access controls to reduce cross-border data exposure while still enabling analytics and AI offloading.
This is very similar to how EU banks align with GDPR and EBA guidelines, or how US healthcare entities fit HIPAA workloads into multi cloud architectures.
UAE TDRA, National Cloud Security Policy and Sovereign Cloud
UAE enterprises typically start from TDRA guidance and the National Cloud Security Policy, then design multi cloud around FedNet, OneCloud and global hyperscalers:
FedNet acts as a secure backbone for federal entities, connecting more than 35 entities and thousands of virtual servers with VMware-verified sovereign cloud capabilities
The National Cloud Security Policy defines baseline controls for identity, encryption, monitoring, and third-party risk for any government cloud service.OneCloud (e& enterprise + Oracle Alloy) and National Hypercloud (du + Oracle Alloy) give regulated industries a UAE-sovereign hyperscale environment for AI and data-intensive workloads.
Architecturally, this often becomes a layered model
Tier 0/Tier 1 government identity (e.g., UAE Pass), health and justice workloads anchored in FedNet and sovereign clouds.
Commercial workloads split between UAE sovereign clouds and global regions (e.g., Azure UAE North + EU West) depending on data residency and latency.
Data stored and replicated using cloud governance and security framework principles that feel very similar to GDPR/UK-GDPR and PCI DSS.
Qatar Cloud Policy Framework, QCB Cloud Regulation and Qatar Cloud
In Qatar, CRA and QCB set the tone
The CRA Cloud Policy Framework aligns Qatar with international security, data protection and transparency standards while encouraging foreign and local investment in cloud.
QCB’s Cloud Computing Regulation, effective April 2024, defines how licensed banks and payment providers should manage cloud risk, governance and security controls.
Providers like Ooredoo (Multi-Cloud Local Connect) and MEEZA deliver sovereign cloud and GPU-enabled AI platforms fully hosted in Qatar.
For CIOs in Doha, a practical approach is:
Use Ooredoo/MEEZA as primary sovereign zones for QCB-regulated banking and critical national systems.
Connect to hyperscalers via local multi-cloud connectivity while enforcing strict data egress rules
Mirror the sort of data residency discipline you would apply for NHS data in the UK or BaFin-regulated data in Germany.
Architecture and Governance Blueprint for Multi-Cloud in MENA
Reference Architecture for GCC Banks and Government
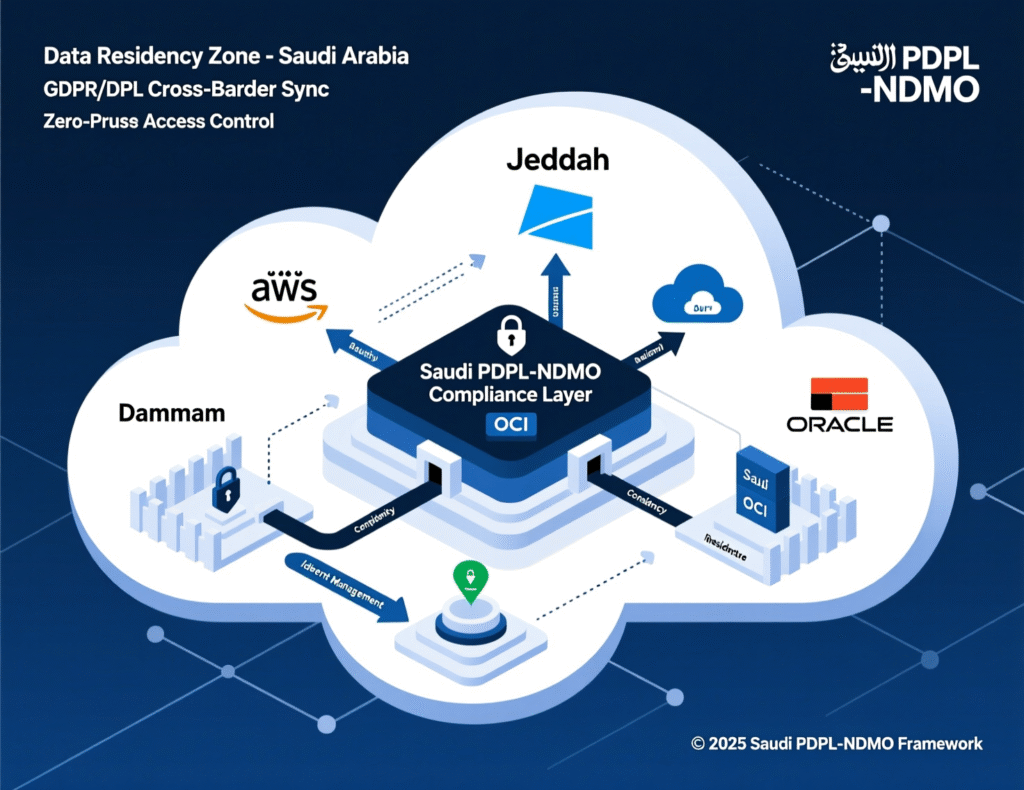
A multi cloud approach improves resilience and data residency for GCC banks and government by separating critical data into sovereign zones, spreading workloads across multiple providers and regions, and designing automated failover paths that never violate localization rules. In practice, that means at least one in-country sovereign cloud, one regional hyperscale, and clear policies for what data can leave the country in encrypted form.
A typical reference architecture for a GCC bank, regulator or smart-city platform looks like this:
Sovereign Zones
Primary core banking, ID, payments or citizen-data systems in a sovereign cloud or government DC (stc Alloy, FedNet, OneCloud, Ooredoo/MEEZA, or equivalent).
Data stored with in-country redundancy (multi-AZ within sovereign region).
Regional / Global Hyperscalers
Analytics, AI/ML, customer-facing mobile apps, and partner integrations in Azure, AWS, GCP or Oracle across Middle East and EU regions.
Strict routing rules to avoid regulated personal data leaving KSA/UAE/Qatar unless PDPL/CRA/TDRA conditions are met.
Workload Zoning & Network Segmentation
Clear zones for public, internal, confidential and restricted workloads, mirroring NDMO or CRA classifications.
Centralized logging and SIEM with cross-cloud correlation, often anchored in sovereign zones.
Cross-Cloud Resilience
Multi-region failover within the same jurisdiction (e.g., between two KSA DCs, or between UAE north and central regions).
Optional cross-jurisdiction DR (e.g., GCC-to-EU) for non-personal data, similar to how US hospitals use EU backups for anonymised research under HIPAA-friendly architectures.
Cloud Governance, Security and Data Classification Frameworks
Without governance, multi cloud becomes “shadow IT at scale.” GCC CIOs are increasingly implementing:
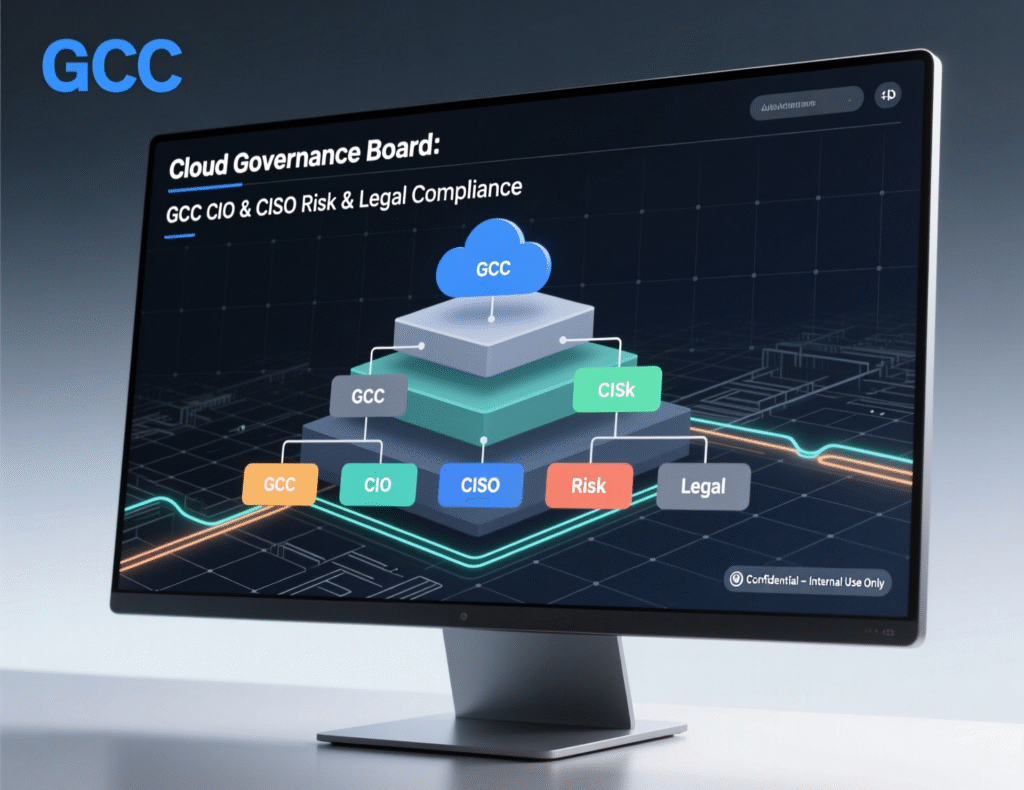
Cloud governance boards including CIO, CISO, COO, Risk, Legal and Business Unit heads in KSA/UAE/Qatar.
A unified cloud governance and security framework that:
Adopts controls familiar from NIST, ISO 27001, CIS Benchmarks and maps them to PDPL, TDRA, CRA, QCB and sector-specific rules (e.g., SAMA, healthcare).
Defines data classification rules aligned with NDMO, National Cloud Security Policy and CRA frameworks.
Codifies change management, incident response and access reviews across all clouds.
Role of the CISO
Chairs or co-chairs the risk committee for multi cloud.
Owns policies for identity, privileged access, encryption and logging across all providers.
Ensures equivalence between sovereign-cloud controls and global-cloud controls.
For CIOs who’ve worked with GDPR, UK ICO guidance or US HHS/HIPAA, this feels very familiar – just with PDPL/TDRA/CRA acronyms instead of GDPR/ICO/HHS.
Arabic-First UX and Bilingual Operations in Multi-Cloud Environments
Technology choices only work if operations match GCC reality:
Arabic-first plus English portals, runbooks, dashboards, training and service catalogs should be bilingual for operations teams spread across Riyadh, Dubai and Doha.
Support desks 24/7 bilingual support is crucial for banks, logistics, telecoms and healthcare providers.
Runbooks & SLAs document failover, DR drills and regulatory reporting workflows in Arabic and English so auditors, regulators and global vendors can all follow the same playbook.
This is an area where GCC often leads compared to US/UK organisations, who sometimes underestimate the friction introduced by monolingual operations.
Cost, Risk and Vendor Management in a GCC Multi-Cloud Strategy
Avoiding Vendor Lock-In While Keeping Compliance
Avoiding vendor lock-in while staying compliant is about smart constraints, not total abstraction:
Use open standards (Kubernetes, Terraform, OpenTelemetry) for core platforms so workloads can move between hyperscalers and sovereign clouds.
Negotiate exit clauses, data export formats and assistance in every major cloud contract, mirroring what PCI DSS or BaFin would expect.

For regulated workloads, keep data models, encryption keys and IAM logic under your control, even if compute runs on external clouds.
For many GCC CIOs, the goal is not “cloud agnostic” everything; it’s “cloud portable enough” to avoid strategic dependency on a single provider or jurisdiction.
Cost Optimization and TCO for Saudi, UAE and Qatar Workloads
With multi cloud, TCO conversations need to compare local vs global regions, egress pricing, managed services and FinOps discipline:
Local sovereign regions might cost more per unit of compute but reduce compliance overhead and audit costs in Saudi, UAE and Qatar.
Hyperscalers offer aggressive discounts via reserved instances and savings plans, but egress from EU/US back to GCC can be high.
Independent reports suggest that around one-third of organisations globally now spend over USD 12 million per year on public cloud, with AI being a major driver.
Bringing in a FinOps practice – or partnering with a firm already running FinOps for other clients – is critical once monthly cloud bills cross six figures. For practical guidance on aligning architecture and billing, see Mak It Solutions’ article on Cloud Cost Optimization. makitsol.com
SLAs, DR and Multi-Region Failover for GCC Enterprises
Banks, government entities, logistics and healthcare providers in GCC increasingly expect:
RPO near zero for core payments, trading, ID and health systems.
RTO from minutes to low hours, depending on tier.
In a multi-cloud design, that translates to:
Intra-region HA within each sovereign or hyperscale region.
Multi-region DR within the same country or GCC where possible.
Sector-specific DR tests (e.g., simulations similar to those used under FCA/BaFin guidance in UK/EU) to prove scenarios to SAMA, QCB or TDRA.
How GCC Organisations Do Multi-Cloud
Banking and Fintech Under SAMA, TDRA, QCB and ADGM/DIFC Rules
In banking and fintech:
Saudi banks combine sovereign KSA clouds with global hyperscalers under SAMA outsourcing rules; Open Banking in KSA often runs on APIs exposed from cloud-native platforms hardened for PDPL and NDMO.
UAE banks operating under TDRA, UAE Central Bank and in ADGM/DIFC often place core banking in UAE sovereign or local regions, then use EU/UK regions for cross-border treasury and analytics.
Qatar banks must comply with the QCB Cloud Computing Regulation, typically anchoring core in Ooredoo/MEEZA while leveraging selective services from hyperscalers.
Across these, patterns often resemble European banks under BaFin or EBA Outsourcing Guidelines – just tuned for GCC regulators instead of EU bodies.
Government and Smart City Workloads in Riyadh, Dubai and Doha
Governments and smart cities (Riyadh, Dubai, Doha, Neom) are major consumers of sovereign cloud:
Saudi’s DGA cloud guidelines and Cloud First Policy push agencies to move workloads to registered cloud providers while preserving data residency.
UAE’s FedNet and sovereign clouds host national ID (like UAE Pass), justice and smart-city platforms integrating traffic, IoT, public safety and citizen services.
Qatar’s government portals and digital identity platforms increasingly rely on CRA-aligned sovereign clouds, with MEEZA and Ooredoo expanding capacity to meet AI workloads.
These architectures look a lot like modern NHS or German e-Gov platforms – just tuned to GCC languages, regulations and regional interconnects.
Retail, Logistics and Healthcare Examples with Local Providers
In retail, logistics and healthcare:
stc cloud / sccc and Solutions by stc provide localized cloud for supply-chain, e-commerce and health providers needing KSA data residency.
e& enterprise, OneCloud and du National Hypercloud support regional retailers, airlines and hospital groups that must keep data in UAE while connecting to EU/US partners.
Ooredoo and MEEZA serve as the sovereign backbone for Qatari healthcare, logistics hubs and FIFA-era infrastructure, now extended for AI-driven services.
Here, multi cloud is usually less about regulation and more about combining latency, customer experience and partner ecosystems across GCC, EU and global markets.
Roadmap and Best Practices for Designing a Multi-Cloud Strategy in the Middle East
Step-by-Step Roadmap from Assessment to Go-Live
A practical cloud workload migration roadmap for GCC CIOs:
Inventory workloads
Catalogue applications, data stores and integrations across KSA/UAE/Qatar entities.
Note sector (banking, gov, healthcare, logistics, retail, fintech).
Classify data
Apply PDPL/NDMO, TDRA, CRA and QCB classifications to data (public, internal, confidential, restricted).
Map health/financial data to HIPAA/PCI-like sensitivity to guide controls.
Map to regulators
For each workload, identify applicable regulators: SAMA, TDRA, CRA, QCB, sector ministries, etc.
Use this to decide which workloads must stay in sovereign clouds vs hyperscalers.
Choose regions and providers
Select sovereign clouds (stc, Solutions by stc, FedNet, OneCloud, du National Hypercloud, Ooredoo, MEEZA) and hyperscalers (AWS, Azure, GCP, OCI) per country and use-case.
Check availability of hyperscale cloud regions in Middle East and EU that match your compliance needs.
Design landing zones
Build standardized landing zones with identity, logging, encryption and network baselines in each cloud.
Align with a common cloud governance and security framework across all clouds.
Pilot and prove
Start with 1–2 representative workloads in each country; run DR drills, penetration tests and cost reviews.
Validate regulator expectations (SAMA, TDRA, CRA/QCB) early, similar to how you’d engage BaFin or NHS Digital in Europe.
Scale and optimize
Roll out by domain (e.g., digital channels, analytics, back-office) while embedding FinOps and compliance reviews into BAU.Continuously tune which workloads run where based on cost, latency, AI features and regulation.
Building a GCC-Focused Cloud Governance Board and Operating Model
Organisationally, successful GCC multi cloud programs usually:
Establish a GCC Cloud Governance Board with representation from:
CIO / Head of Architecture (strategy, patterns, platform)
CISO (security, identity, data protection)
Risk & Compliance (PDPL, TDRA, CRA, QCB, sector rules)
Legal & Procurement (contracts, SLAs, exit, data transfer)
Business Unit leaders from KSA, UAE, Qatar
Define R&R across countries e.g., regional cloud leads in Riyadh, Dubai and Doha who own provider relationships and operational KPIs.
Align with global HQ where relevant (US, UK, EU) so GCC strategies also reflect GDPR/UK-GDPR, BaFin, FCA or HIPAA expectations.
Monitoring, FinOps and Compliance Reviews
Multi cloud is never “set and forget,” especially in a region where regulations and sovereign offerings evolve quickly:
Monitoring & Observability unify metrics, logs and traces across clouds; standardize SLOs and alerts.
FinOps monthly cost allocation, anomaly detection and right-sizing per cloud and per country.
Compliance Reviews periodic alignment against NDMO, TDRA, CRA, QCB, PDPL and sector-specific updates, similar to periodic GDPR/PCI DSS reviews in EU/US.
Partnering with a specialist can help here especially one that already runs these loops for SaaS, cloud and analytics clients across US, UK, Germany, EU and the Middle East, like the team at Mak It Solutions. makitsol.com+1
Turning GCC Compliance into Multi-Cloud Advantage
Key Takeaways for Saudi, UAE and Qatar CIOs
Compliance is the design canvas start from PDPL, NDMO, TDRA, CRA, QCB and sector rules, then design multi cloud that makes compliance easy, not painful.
Sovereign + hyperscale is the new normal expect at least one sovereign cloud plus one or two hyperscalers in any serious GCC architecture.
Resilience and AI go hand-in-hand resilience patterns must protect localized data while still allowing AI workloads to tap regional/global GPU capacity.
Governance beats tools cloud governance boards, clear R&R and bilingual operations matter more than any specific platform feature.
FinOps is mandatory at scale once cloud spend grows, multi cloud without FinOps quickly becomes unsustainable.
When to Bring in a Multi-Cloud Consulting Partner in GCC
You should consider bringing in a multi cloud consulting partner when:
You operate across Saudi, UAE and Qatar with mixed banking, government, healthcare or logistics workloads.
You need a cloud workload migration roadmap that respects PDPL, NDMO, TDRA, CRA and QCB, while still leveraging AI services from hyperscalers.
Your internal teams are strong technically but stretched thin on regulatory mapping, FinOps or architecture documentation.
A partner like Mak It Solutions can help you design the architecture, governance and implementation plan, then work alongside your in-house teams to deliver so you get the benefits of a mature global cloud practice without slowing down your GCC transformation.
If you’re planning or refreshing your multi cloud strategy in Middle East and need to balance compliance, resilience and AI innovation across Saudi, UAE and Qatar, you don’t have to do it alone. Mak It Solutions works with CTO/CIO teams worldwide to design cloud architectures, build secure landing zones and optimize TCO for complex, regulated environments.
Share your current landscape and regulatory constraints, and our Editorial Analytics Team can help you turn them into a concrete architecture and execution roadmap. Visit the Mak It Solutions Services and Cloud Cost Optimization pages or reach out via the Contact page to start a focused discovery conversation. ( Click Here’s )
FAQs
Q : Is multi cloud hosting allowed under Saudi SAMA and PDPL regulations for banks?
A : Yes multi cloud hosting is allowed for Saudi banks, but it must strictly follow PDPL, NDMO and SAMA outsourcing rules. In practice, this means classifying data, keeping restricted personal and financial data within KSA sovereign or approved government clouds, and ensuring SAMA-compliant contracts with clear audit, incident reporting and exit provisions. Many banks use sovereign KSA clouds for core systems while leveraging hyperscalers for analytics, much like EU banks balance GDPR with EBA guidance.
Q : How can UAE companies ensure TDRA-compliant data residency when using multiple hyperscalers?
A : UAE companies typically anchor sensitive workloads in TDRA-aligned infrastructures like FedNet, OneCloud or National Hypercloud, then place less sensitive workloads in global hyperscale regions. The National Cloud Security Policy and TDRA guidance expect clear data classification, documented residency rules, and strong encryption and access controls for any cross-border processing. By using region-restricted services, customer-managed keys and audited connectivity, UAE enterprises can use multiple clouds while ensuring regulated data never leaves the UAE without proper safeguards.
Q : What are the main multi cloud options for Qatar organisations under the CRA Cloud Policy Framework?
A : Under the CRA Cloud Policy Framework and QCB Cloud Computing Regulation, Qatar organisations usually combine local sovereign providers with selected global clouds. Ooredoo’s Multi-Cloud Local Connect and MEEZA’s sovereign cloud/AI platforms provide in-country infrastructure for regulated data, while hyperscalers are used for less sensitive services and advanced analytics. The key is to follow CRA/QCB rules on data protection, transparency and security controls, with clear policies on which workloads can run where and under what residency conditions.
Q : Do GCC companies need separate multi cloud strategies for on-prem, public cloud and sovereign cloud zones?
A : They need one overarching hybrid multi cloud strategy, but with differentiated patterns for on-prem, public cloud and sovereign zones. On-prem often hosts legacy or latency-sensitive systems; sovereign clouds host regulated data and critical government or banking workloads; public clouds host customer-facing apps and AI platforms. The strategy should define how data flows between these zones, how identity and logging are unified, and how regulatory controls are consistently applied similar in spirit to how large European organisations integrate on-prem, EU-based clouds and global regions under a single governance framework.
Q : How do costs of a multi cloud strategy compare between Saudi, UAE and Qatar deployments?
A : Costs differ by country, provider mix and regulatory requirements. Saudi and UAE sovereign clouds may have higher per-unit prices but can reduce compliance overhead and latency, while global hyperscalers often offer better discounts and AI services but add egress and residency-management costs. Qatar organisations may pay a premium for fully localised infrastructure via Ooredoo and MEEZA, particularly for GPU-heavy AI workloads. A cross-country FinOps model that compares total cost of ownership not just VM hourly rates is essential to avoid surprises as deployments scale.


