Ransomware Defense Playbook for US, UK, and EU Teams
Ransomware Defense Playbook for US, UK, and EU Teams

Ransomware Defense Playbook for US, UK, and EU Teams
Ransomware has shifted from “rare disaster” to “probable event” for mid-size and enterprise organisations across the US, UK, Germany and the wider EU. Recent research suggests the average total cost of a ransomware attack in 2024 was in the region of $5 million once you include ransom, downtime, recovery and reputational damage. At the same time, only around a quarter of victims now pay, as more organisations invest in cyber resilience instead of hoping it never happens
That’s exactly where a ransomware defense playbook earns its place: turning vague intentions into concrete steps your teams can follow on a bad day.
What Is a Ransomware Defense Playbook?
A ransomware defense playbook is a single, repeatable guide that brings together your prevention, containment and recovery workflows so security, IT and legal teams can respond consistently under pressure. Instead of scattered Word docs and tribal knowledge, it gives you one agreed process across backups, network segmentation and a ransomware incident response plan.
Core Components: Backups, Segmentation and Incident Response
At its core, a ransomware defense playbook weaves together a ransomware backup strategy, network segmentation and a ransomware incident response playbook into one workflow.
Backups are your safety net: layered, immutable and frequently tested so you can recover without paying.
Segmentation limits blast radius by making “network segmentation to prevent ransomware spread” a default design choice, not an afterthought.
Incident response defines who leads, who communicates and how your technical, legal and PR teams work together.
Many teams wrap this into a broader ransomware recovery plan that covers business continuity, vendor coordination and post-incident hardening. Together, these elements form a double-extortion ransomware defense strategy that assumes attackers may both encrypt and exfiltrate your data
Who Needs a Ransomware Defense Playbook? (SMBs to Regulated Enterprises)
Pretty much everyone above “very small business” territory needs a ransomware defense playbook. That includes CISOs, IT directors, OT/ICS security leads and risk managers in.
Mid-size US businesses in New York, Austin or Chicago juggling cyber-insurance questionnaires and state breach laws.
UK SMEs in London or Manchester facing UK-GDPR, NHS or FCA-adjacent expectations.
German Mittelstand manufacturers around Frankfurt, Munich or Stuttgart operating OT networks and subject to BaFin or NIS2 rules.
Common triggers include cyber-insurance renewals, board concern after a sector peer is hit, or regulators tightening expectations on cyber resilience against ransomware.
How a Playbook Supports Compliance and Cyber Insurance
A structured ransomware defense playbook becomes evidence. Auditors, regulators and insurers want to see:
Backup testing records including restore tests and RPO/RTO results.
Segmentation diagrams showing critical zones, remote access paths and OT/ICS boundaries.
IR runbooks roles, call trees and legal/privacy workflows.
This documentation helps demonstrate alignment to GDPR/DSGVO and UK-GDPR breach handling, HIPAA safeguards for US healthcare, PCI DSS requirements for cardholder data, SOC 2 security controls and NIS2 expectations for “essential and important” entities in the EU.
Designing Your Ransomware Incident Response Plan
A ransomware incident response plan defines who does what in the first minutes, hours and days of an attack, covering technical, legal and communication workflows. It should be built so you can follow CISA’s StopRansomware guidance while tailoring it to your own business and regulators.

Prepare and Detect: Roles, Runbooks and Tooling
To build a ransomware incident response plan following CISA guidance, start by defining clear roles:
Incident Commander overall decision-maker and bridge to execs/board.
Technical Lead / Forensics containment, triage, evidence preservation.
IT Operations backup protection, restores and infrastructure changes.
Legal / Privacy breach assessment, notifications, regulator engagement.
Communications Lead staff, customer, media and partner messaging.
Codify these roles into IR runbooks, call trees and bridge line details, backed by your SIEM/SOAR, EDR/XDR, ticketing and collaboration tools. CISA’s ransomware response checklist is a useful template for the “who calls whom, in what order” aspects.
The First 24 Hours After a Ransomware Attack
The first 24 hours should roughly follow a ransomware response checklist for CISOs.
Isolate affected systems segment or disconnect infected endpoints, servers and OT segments.
Protect backups immediately verify that backup repositories are isolated, immutable and not yet compromised.
Preserve evidence collect volatile data, logs and snapshots before wiping or rebuilding.
Identify the ransomware family using threat intel and IR partners to understand TTPs.
Assess blast radius which domains, plants, cloud accounts and SaaS apps are affected.
Engage legal and leadership including initial notifications under GDPR, UK-GDPR or HIPAA where relevant.
This aligns with typical “ransomware emergency response guide” patterns while leaving room for sector-specific details.
Legal, Regulatory and Communications Workflows
Your plan must include legal, privacy and PR workflows because regulatory risk is often as painful as the technical incident.
Under GDPR/DSGVO and UK-GDPR, you may have as little as 72 hours from becoming aware of a personal data breach to notify your data protection authority (for example, ICO in the UK or a German DPA)
Sector regulators like BaFin and the ECB expect banks and insurers to treat ransomware as part of broader ICT and cloud-outsourcing risk management ([BaFin][8]). In the US, HHS/OCR enforces HIPAA breach rules for hospitals and insurers, while state AGs and sector regulators add extra reporting layers.
On communications, define pre-approved playbooks for internal staff, customers, partners and the media. Run them in exercises so you’re not drafting your first ransomware press release in the middle of an outage.
Ransomware Backup Strategy and Recovery Plan
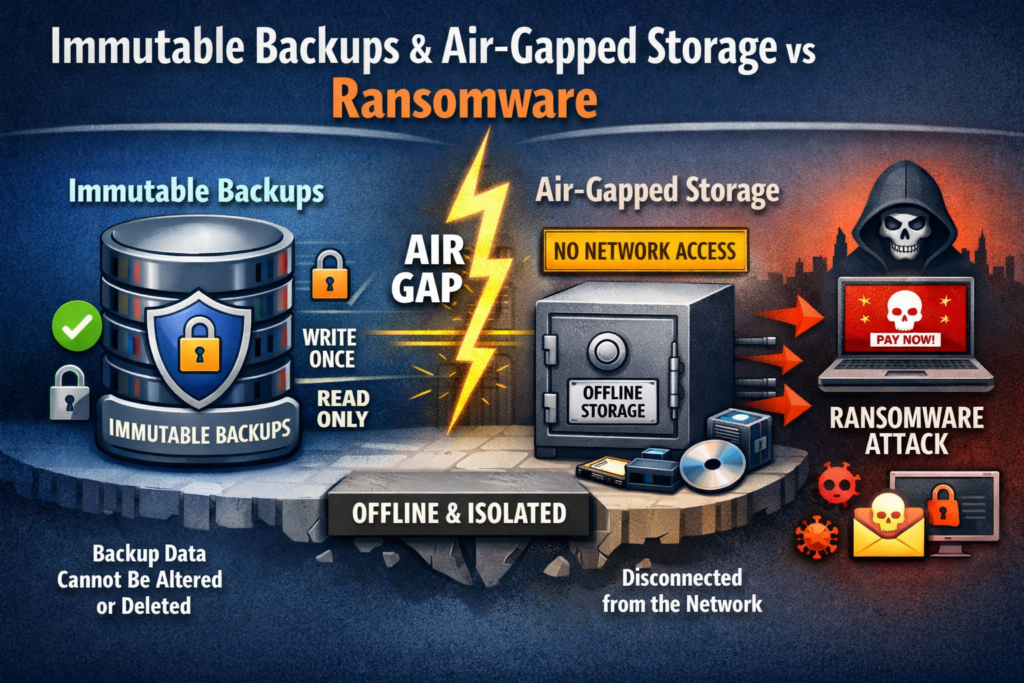
A ransomware-resilient backup strategy uses layered copies (the 3-2-1-1-0 rule), immutable storage and frequent restore tests so you can recover without paying the ransom. In many cases, the strength of your ransomware backup strategy determines whether you can shrug off a double-extortion attempt or are forced to negotiate.
3-2-1-1-0, Immutability and Air-Gapped Backups
For ransomware, the 3-2-1-1-0 rule is a practical baseline:
3 copies of your data
on 2 different media types
1 copy offsite
1 copy offline/air-gapped or immutable
0 backup integrity errors from regular testing
Combine immutable storage and air-gapped backups for example, write-once cloud object locks plus offline copies – so attackers can’t easily encrypt or delete your backups. UK NCSC’s guidance on ransomware-resistant backups emphasises resilience to destructive actions, including attacks on backup control planes.
Tie this architecture explicitly to PCI DSS expectations for protecting cardholder data and to typical cyber-insurance clauses around backup frequency and test evidence.
Backup and Disaster Recovery Planning for US, UK and EU Organisations
Different GEOs emphasise different things.
US healthcare (HIPAA) focus on ePHI availability, documented DR plans and evidence that critical clinical systems (EHR, imaging) can be restored within safe clinical windows.
UK public sector & NHS align with NCSC guidance and NHS-specific business continuity rules for trusts and local authorities.
EU finance (GDPR, BaFin/ECB) show that backup and DR locations, including cloud regions, respect data residency and outsourcing supervision rules.
If you operate multi-region cloud (AWS, Microsoft Azure, Google Cloud), document which workloads run in which regions (for example, Frankfurt vs Dublin) and where their backups replicate. This is particularly important for EU data under GDPR and for Open Banking APIs handling payment data.
Testing Restores, RPO/RTO and Proving Cyber Resilience
Backups don’t matter if you can’t restore fast. Design and rehearse a ransomware recovery plan that covers:
Critical business apps (ERP, CRM, trading, billing)
OT systems in plants or utilities.
SaaS platforms (HR, collaboration, CRM) where you rely on vendor-side retention.
Define RPO/RTO per system, run ransomware tabletop exercise and runbook drills around realistic scenarios, and store evidence of test results for boards, auditors and insurers. Industry studies show average ransomware downtime can run to multiple weeks; every hour you shave off recovery has a direct cost impact.
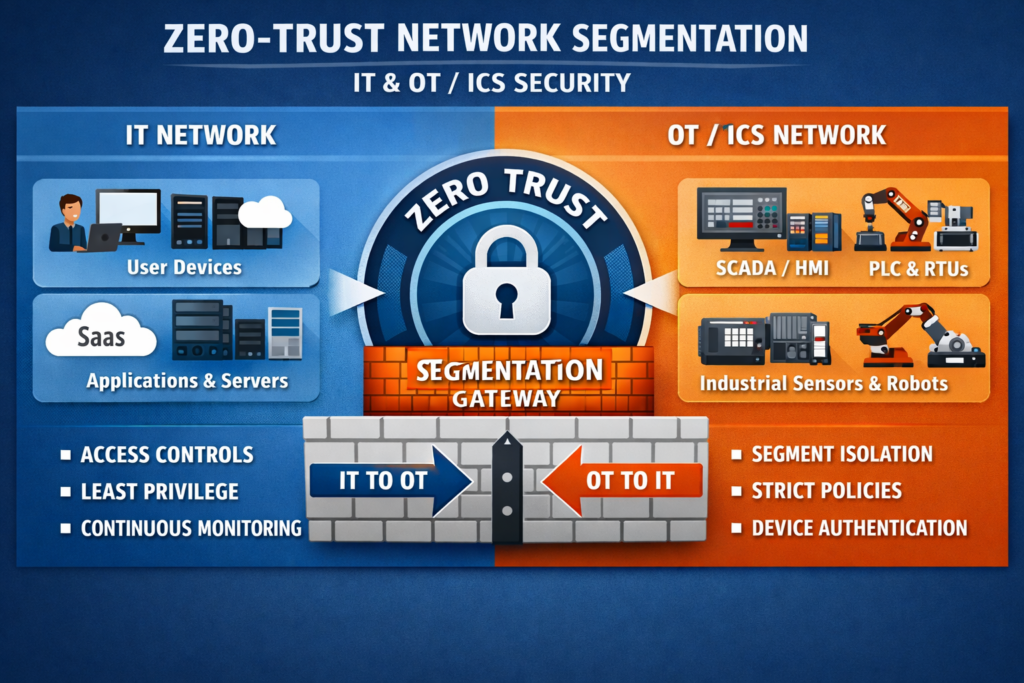
Network Segmentation for Ransomware Containment
Network segmentation limits how far ransomware can spread, breaking the attack path into smaller zones that are easier to monitor, isolate and recover. Think of segmentation as the backbone of zero trust ransomware protection: assume compromise and limit lateral movement by default.
Macro vs Microsegmentation.
Macrosegmentation splits your estate into big zones corporate IT, OT/ICS, cloud production, DMZ, guest networks and so on.
Microsegmentation restricts traffic within those zones at the workload or identity level.
A good microsegmentation ransomware defense model enforces least-privilege communication between apps and services, making it much harder for ransomware to jump from a compromised workstation to domain controllers, databases or OT HMIs. Explicitly call this out in your playbook as “network segmentation to prevent ransomware spread” so architects treat it as a core requirement, not a nice-to-have.
Zero Trust Network Segmentation for IT, OT and ICS
Zero trust principles never trust, always verify, enforce least privilege apply across.
IT networks identity-aware firewalls, ZTNA for remote access, per-app access policies.
Cloud segment VPCs/VNETs, lock down management planes, enforce conditional access to admin consoles.
OT/ICS segment production lines, PLC networks and safety systems; restrict remote vendor access; align to OT/ICS ransomware defense playbooks from national CSIRTs and sector regulators.
Document these controls in your playbook diagrams so IR teams know which “valves” they can close during an incident.
Segmentation Patterns for US, UK and German Environments
Concrete examples help bring the ransomware defense playbook to life.
US hospitals and critical infrastructure isolate clinical networks from admin IT; carve out high-value systems (EHR, PACS, OT) into tightly controlled segments with dedicated jump hosts.
UK public sector networks separate citizen-facing portals, internal line-of-business apps and legacy systems; align controls with NCSC and NHS guidance.
German manufacturing plants treat OT production cells and MES/SCADA as separate “castles” with limited, audited connections back to ERP in Frankfurt or other EU data centres.
In multi-region cloud environments (for example, AWS eu-central-1 Frankfurt plus Azure UK South), the playbook should specify how to contain a compromised region and fail over only from known-good backups.
GEO-Specific Ransomware Defense Playbook
The core ransomware defense playbook is global, but reporting, backups and segmentation must reflect local laws, regulators and critical-infrastructure rules. You don’t want one team following HIPAA logic while another assumes GDPR covers everything.
United States: Federal Guidance, HIPAA and State Laws
In the US, anchor your playbook to CISA’s StopRansomware guidance and sectoral rules: HIPAA for healthcare, GLBA and state laws for finance, and a patchwork of state breach-notification laws
A typical example: a mid-size US hospital in New York aligns its IR runbooks and backup strategy so it can both satisfy its cyber-insurer and show HHS/OCR it can restore clinical systems to safe operation without paying attackers. That same ransomware defense playbook for mid-size US businesses can be reused by insurers, SaaS providers and universities with modest tweaks.
United Kingdom: NCSC Guidance, UK-GDPR and NHS Context
In the UK, base your playbook on NCSC malware and ransomware guidance plus UK-GDPR expectations . Your workflows should include:
Breach triage and risk assessment aligned to ICO guidance.
Incident notification paths to ICO and, for NHS bodies, relevant NHS and regional authorities.
Ransomware-resistant backups following NCSC’s cloud backup principles.
Recent incidents including ICO guidance following fines against large UK outsourcers after cyberattacks show regulators are increasingly willing to penalise weak cyber hygiene and poor incident handling.
Germany & Wider EU.
For Germany and the wider EU, the playbook should reference BSI and ENISA guidance on incident response and cyber crisis management, plus the emerging NIS2 regime for essential and important entities.
Map reporting obligations to national CSIRTs and sector regulators.
For banks and insurers, align cloud and backup design with BaFin supervisory expectations and ECB outsourcing guidance.
Include data residency and Schrems-II-aware backup location design for EU personal data.
Testing, Tabletop Exercises and Continuous Improvement
A ransomware defense playbook only works if it’s tested; tabletop exercises and recovery drills turn documents into muscle memory. Many high-impact incidents show that slow or confused responses can massively increase cost and downtime.
Ransomware Tabletop Exercises for US, UK and EU Teams
Design ransomware tabletop exercise and runbook scenarios that feel real to your executives:
A double-extortion attack on a New York fintech with stolen trading data.
A London NHS-adjacent supplier unable to process patient referrals.
A Berlin manufacturing plant whose OT network is partially encrypted.
Run sessions where technical teams, legal, PR and execs walk through the playbook step by step: detection, triage, containment, legal decisions, communications and recovery. Capture gaps and refine your IR runbooks and ransomware recovery plan template after each exercise.
Metrics, SLAs and Learning from Incidents
Define a small set of metrics and SLAs, for example.
Time to detect (TTD) from initial compromise to first alert.
Time to contain (TTC) from alert to stopping lateral movement.
Time to restore (TTR) from containment to business-ready service.
Communication SLAs how quickly key stakeholders are informed.
Use post-incident reviews (including near misses) to feed improvements back into backups, segmentation and IR plans, just as you’d use post-mortems in software reliability or FinOps
When to Bring in MDR Providers and IR Retainers
Managed Detection and Response (MDR), XDR platforms and specialist IR consultancies can significantly improve early detection and containment. Your playbook should define:
When to escalate to your MDR/XDR provider.
How and when to activate your IR retainer.
Who owns coordination between internal teams and external experts.
For many mid-size organisations without 24/7 SOC coverage, these partners are the difference between a contained ransomware incident and a full-blown, weeks-long outage.
Putting It All Together.
The outcome you want is a living playbook your team can use tomorrow, not a theoretical policy sitting in a GRC tool. To build a ransomware defense playbook that combines backups, segmentation and incident response into one repeatable process, treat these pillars as a single end-to-end journey from prevention to recovery.
Checklist: Minimum Viable Ransomware Defense Playbook
Your minimum viable playbook should include at least.
A named incident commander and core IR team with contact details.
A documented ransomware incident response plan template (roles, runbooks, checklists, decision trees).
A ransomware recovery plan template with RPO/RTO targets, system prioritisation and restore playbooks.
Documented backup architecture (3-2-1-1-0), immutable and air-gapped copies and test schedules.
Segmentation diagrams showing how to isolate critical zones in IT, OT and cloud.
GEO-specific legal and regulator workflows (US, UK, Germany/EU).
A schedule for tabletop exercises and post-incident reviews.
Choosing Tools, Platforms and Partners
You don’t need a particular vendor to execute this playbook, but you do need tools that fit together:
Backup platforms that support immutable storage and orchestrated recovery.
Segmentation and identity platforms aligned to zero trust ransomware protection (for example, strong IAM, ZTNA, microsegmentation)
SIEM/SOAR, EDR/XDR and logging pipelines that support rapid triage and automation.
Cloud platforms (AWS, Azure, Google Cloud) configured with least-privilege admin and region-level guardrails.
When evaluating partners, look for those who can help you design, test and operationalise the playbook not just sell point tools.
30–90 Day Roadmap to Implement Your Playbook
Here’s a practical 30–90 day roadmap.
Days 0–30
Assess current state, run a quick risk workshop, document your rough playbook, protect backups and implement a few quick-win segmentation rules.
Days 30–60
Harden backup architecture (3-2-1-1-0), refine segmentation for critical systems, align IR runbooks to CISA, NCSC, ENISA and local regulators, and brief executives
Days 60–90
Run at least one ransomware tabletop exercise, refine templates and agree on an ongoing test and metrics schedule.
From there, you iterate treating ransomware defense as an ongoing capability, not a one-off project.

Key Takeaways
Ransomware is a “when, not if” risk for mid-size and enterprise organisations in the US, UK, Germany and the wider EU.
An effective ransomware defense playbook combines backups, network segmentation and incident response into one end-to-end process.
GEO-specific legal and regulatory workflows (GDPR/DSGVO, UK-GDPR, HIPAA, PCI DSS, NIS2) must be baked into your IR and recovery plans.
Immutable storage, air-gapped copies and regular restore tests are non-negotiable for ransomware-resilient backups.
Tabletop exercises, clear metrics and trusted MDR/IR partners turn static documents into real-world cyber resilience against ransomware.
If you’d like help turning this guidance into a concrete, regulator-ready ransomware defense playbook, Mak It Solutions can work with your security, IT and risk teams to design and test the right mix of backups, segmentation and IR processes for your environment. Whether you’re a hospital in the US, a council in the UK or a manufacturer in Germany, we can help you move from “we’d be in trouble” to “we’ve rehearsed this.”
Start by shortlisting your critical systems and current backup setup, then reach out to discuss a focused 30–90 day playbook implementation sprint tailored to your GEOs and regulators.( Click Here’s )
FAQs
Q : What is the first step in creating a ransomware runbook for my organisation?
A : The first step is to define ownership: appoint an incident commander and a core IR team spanning security, IT operations, legal/privacy and communications. Once roles are clear, you can draft a simple ransomware runbook that covers detection, containment, backup protection, legal assessments and communications in the first 24 hours, then refine it after tabletop exercises and real incidents.
Q : How often should we test our ransomware backups and full recovery process?
A : At minimum, you should test backup restores for critical systems quarterly and run at least one full ransomware recovery drill per year that simulates restoring from a large-scale incident. Highly regulated or mission-critical environments such as hospitals, banks or OT/ICS plants often move to monthly or even continuous testing for their most important workloads. The goal is to prove you can meet your RPO/RTO targets in practice, not just on paper, and to provide evidence for auditors, boards and insurers.
Q : Do cyber-insurance providers require a documented ransomware incident response plan?
A : Most serious cyber-insurance providers now expect a documented ransomware incident response plan and may ask to see evidence such as runbooks, contact lists, backup test reports and segmentation diagrams. Some policies even link coverage to specific controls like multi-factor authentication, immutable backups and 24/7 monitoring. Treat your ransomware defense playbook as a way to both reduce the chance and impact of claims and to streamline renewal discussions with your insurer.
Q : How does a ransomware defense playbook differ for OT/ICS environments compared with standard IT networks?
A : In OT/ICS environments, safety and physical process integrity come first, so the playbook must consider plant shutdown, equipment damage and human safety alongside data loss. You’ll lean more heavily on strict segmentation between IT and OT, vendor access controls and tested procedures for safely isolating production lines or SCADA systems. Incident response must integrate plant engineers and OT vendors, and regulators for energy, transport or manufacturing may impose additional reporting and continuity obligations compared with standard IT networks.
Q : What are the most common mistakes organisations make in a ransomware recovery plan?
A : Common mistakes include assuming backups are usable without testing, failing to protect backup control planes from attack and underestimating how long full restoration will take. Many organisations also overlook SaaS data, third-party dependencies and OT systems, focusing only on core servers. Finally, a lot of recovery plans stop at the technical level and ignore legal, regulatory and communications steps—leading to rushed decisions, delayed notifications and greater regulatory and reputational damage.


