Ransomware Trends 2025: Stats, AI Threats, Defense
Ransomware Trends 2025: Stats, AI Threats, Defense
Ransomware Trends 2025: Stats, AI Threats, Defense
Ransomware trends 2025 show attackers shifting to AI-assisted phishing, double/triple extortion and data-theft-only campaigns that hit US, UK and EU organisations across healthcare, manufacturing, finance and the public sector. To stay ahead, CISOs need a 2025-ready ransomware defense stack that combines identity-first security, resilient backups, tested incident response and compliance with GDPR/DSGVO, UK-GDPR, NIS2, HIPAA and other sector regulations.
Introduction
Ransomware in 2025 is no longer “one server down for a day”. It’s weeks of disruption, leaked data on public leak sites and headlines that pull in regulators and boards. When a pathology provider in London was hit, NHS hospitals had to cancel operations and divert patients; similar campaigns have knocked US state and local governments offline and forced EU manufacturers in Berlin and Vienna to halt production lines for days.
Ransomware trends 2025 are driven by three forces: AI-powered attacks that supercharge social engineering, data-theft extortion that weaponises GDPR-style penalties, and growing regulatory and cyber insurance pressure in the United States, United Kingdom, Germany and the wider EU. This guide walks through how these ransomware statistics and patterns vary by region and sector, then gives you a practical roadmap to design a 2025-ready defense stack for your own organisation.
Why Ransomware Trends 2025 Matter for US, UK and EU Businesses
For security leaders in New York, London or Munich, ransomware in 2025 remains one of the most likely ways to trigger a major incident, regulatory investigation and board-level crisis. Ransomware trends 2025 matter because they show where attackers are focusing, which controls fail first and what regulators now consider “basic hygiene”.
Note
Nothing in this article is legal or financial advice. Always consult your own legal, compliance and risk experts.
Fast facts key ransomware statistics 2025
Across the US, UK and EU, ransomware remains a top cyber threat, with data-theft extortion and downtime costs rising even when ransoms are not paid. Some global datasets suggest ransomware accounts for a large share of reported cyber incidents, while ENISA continues to list ransomware among the most impactful threats against EU organisations. EU-focused reports also indicate that a large proportion of cybercrime incidents against organisations involve ransomware or related data breaches.
Sophos’ State of Ransomware research indicates that by 2025 the average ransom payment sits around the seven-figure mark, while average recovery costs (forensics, legal work and rebuilding systems) are higher still.At the same time, EU manufacturing case studies show ransomware and cyber extortion causing prolonged production outages and supply-chain disruption across multiple countries.
When you review ransomware statistics 2025, it helps to distinguish three buckets:
Attack attempts blocked by email security, EDR/XDR and identity controls.
Successful encryption events files and systems are locked.
Data exfiltration-only events no encryption, but cyber extortion based on stolen data.
That last category is growing quickly and often slips through classic “encryption-only” metrics.([Heimdal Security][6])
How 2025 compares to previous years
Compared with 2022–2023, ransomware trends 2025 show a clear pivot from “encrypt first, negotiate later” to double and triple extortion. Attackers now:
Steal data.
Encrypt systems.
Add extra pressure via DDoS, harassment of executives or direct outreach to your customers and suppliers
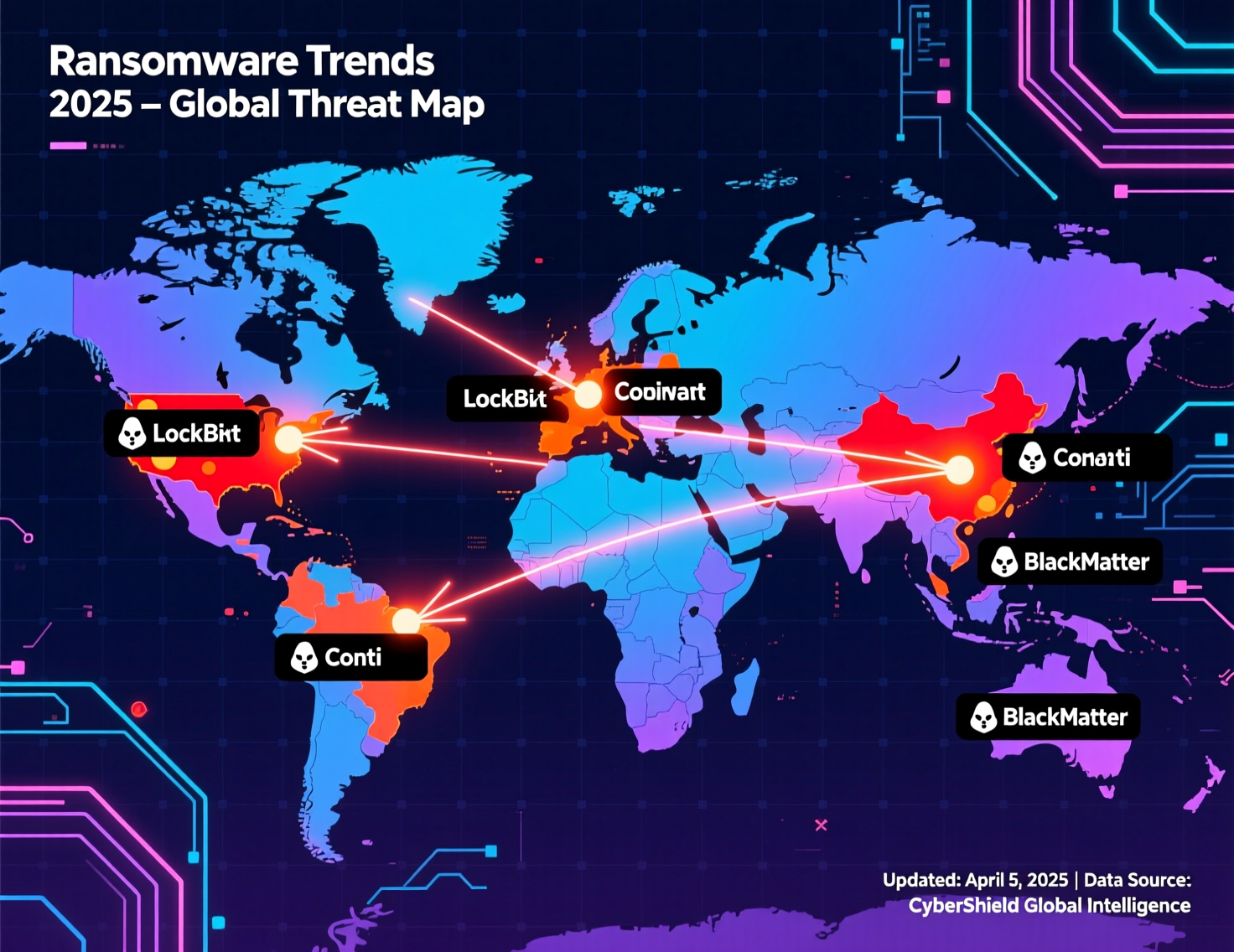
“Spray and pray” ransomware spam is less attractive. We see more targeted operations against hospitals, SaaS providers, industrial/OT environments and municipal networks in Washington DC, London boroughs and German states.([enisa.europa.eu][5]) Average ransom demands surged into 2024 (some datasets suggest around $2M per incident), but actual payments and median demands are now more volatile as more organisations refuse to pay and law enforcement continues to pressure major ransomware-as-a-service (RaaS) groups.
The biggest shift between 2023 and ransomware trends 2025 is that data leak sites and cyber extortion markets have become the main stage. Victims are listed publicly within days, and stolen data is auctioned or dumped even when a ransom is paid.
Who is most at risk SMBs, enterprises and public sector
Small and mid-sized organisations are often hit hardest by ransomware because they have fewer security staff, more legacy systems and inconsistent backup strategies In New York or Seattle, mid-market manufacturers and healthcare providers often run a mix of on-prem ERP, OT and cloud SaaS with under-resourced SOC coverage.
In the UK, local councils and NHS trusts in regions like London and Manchester face constant pressure: complex estates, old IT and critical citizen services make them attractive ransomware targets.([The Guardian][9]) In Germany, Mittelstand manufacturers around Berlin, Frankfurt and Munich are prime targets because of high-value IP and tightly coupled supply chains, as reflected in BSI and ENISA analyses of OT-heavy environments.
Large enterprises can typically absorb direct financial losses, but SMBs in both the US and EU still face existential risk. Some analyses suggest a significant fraction of SMEs close within six months of a major ransomware incident.
State of Ransomware 2025 Global, Regional and Sector View
The most important ransomware trends 2025 for US, UK and European businesses are: rising data-theft extortion, AI-driven phishing, and persistent attacks on healthcare, manufacturing and the public sector. The playbook is global, but each country and industry sees a different flavour of the same threats.
Attack volume, dwell time and ransom payments in 2025
Organisations in the US, UK and Germany report daily or weekly ransomware attempts, though only a subset progress to full encryption or public data leaks. EU-level reporting suggests thousands of serious cyber incidents in the 12 months to mid-2025, with ransomware among the most damaging.
Dwell time the period between initial compromise and ransomware deployment has generally shortened as attackers automate discovery and lateral movement. At the same time, many incidents still show weeks of undetected access inside cloud and SaaS environments before extortion begins. Average recovery times range from around a week to well over a month, and roughly one-third of organisations report taking longer than four weeks to fully restore business operations.([Spacelift][12])
In 2025, most victims incur significant business interruption costs even when no ransom is paid, driven by containment, forensic investigations, legal review and regulatory reporting. The ransom payment, if it happens, is just one line in a much larger incident-response bill.
Ransomware attacks 2025 by industry
Ransomware attacks 2025 show clear hotspots
Healthcare
US hospitals and insurers subject to HIPAA face frequent ransomware and cyber extortion targeting EHR systems and medical devices. UK NHS trusts continue to see attacks that lead to postponed appointments and diverted ambulances, while EU hospitals face similar pressures under GDPR and NIS2.
Manufacturing & OT
EU manufacturing has been hit by multiple ransomware incidents leading to prolonged downtime in 2024–2025, especially in Germany and Central/Eastern Europe, where OT and industrial control systems are closely integrated with IT networks.
Financial services
BaFin-regulated firms and UK Open Banking providers face aggressive ransomware and data-theft campaigns that target payment systems, trading platforms and customer data.
Public sector & education
US school districts, UK local councils and EU public administrations are repeatedly targeted because of sensitive data, constrained budgets and slower patching cycles.
Many high-impact cases are cross-border supply-chain incidents, where a single SaaS, IT services or industrial vendor is compromised and ransomware spreads to customers across several EU countries.
Regional hotspots US, UK, Germany and wider Europe
United States
Critical infrastructure, state/local government, healthcare and SaaS providers hosted on AWS, Azure and Google Cloud are prime targets. CISA’s StopRansomware initiative continues to publish joint guidance and sector-specific playbooks.
United Kingdom
NHS trusts, retailers and local councils remain heavily targeted, with NCSC as the main advisor for both public-sector and private companies. Recent UK data shows hundreds of major ransomware incidents and a sharp increase in cyber insurance claims.
Germany
BSI Lageberichte and related EU reports keep highlighting ransomware as a leading threat to Mittelstand and industrial/OT environments, especially in manufacturing and critical infrastructure.
Wider EU
ENISA’s Threat Landscape 2025 report maps thousands of incidents across France, the Netherlands, the Nordics and Central/Eastern Europe, emphasising ransomware and DDoS as key attack types against public administration and manufacturing.
How Ransomware Tactics Evolved by 2025
By 2025, ransomware is less a single piece of malware and more a business model. RaaS operations, initial access brokers and data leak marketplaces form a cybercrime ecosystem that mirrors SaaS — complete with support, dashboards and “partner” programmes.
From single to double and triple extortion
A double extortion ransomware attack combines file encryption with theft of sensitive data. Triple extortion adds further pressure via DDoS, harassment of executives, or threats aimed at your customers and partners. In 2025, most high-impact ransomware incidents involve double or triple extortion encryption alone rarely provides enough leverage.
US healthcare providers have seen attackers threaten to dump patient records or publish medical images. UK retailers have faced threats to leak customer card data and loyalty profiles. German financial institutions worry about stolen trading data, Open Banking API keys and BaFin scrutiny if sensitive information ends up on leak sites.

Data exfiltration-only extortion attacks.
A growing number of campaigns skip encryption entirely and focus on cyber extortion and data exfiltration. Attackers compromise Microsoft 365, Google Workspace or cloud file stores, quietly copy data and then send extortion notes claiming proof of access.
These “pure extortion” attacks are attractive for threat actors because there’s no noisy encryption phase, business operations can continue and defenders may underestimate the severity. For European organisations, however, any confirmed data exfiltration can trigger GDPR/DSGVO, UK-GDPR and NIS2 breach-notification obligations, even if you can restore systems from backup within hours.
Ransomware-as-a-service (RaaS) and the cybercrime business model
The ransomware-as-a-service (RaaS) ecosystem splits responsibilities across:
Developers who maintain the ransomware code and infrastructure.
Affiliates who run campaigns and share profits.
Initial access brokers who sell credentials or footholds into US, UK and EU networks.
RaaS marketplaces provide playbooks, support channels and dashboards that look disturbingly like legitimate SaaS products. This has lowered the barrier to entry for less-skilled threat actors targeting SMEs in Austin, London or Berlin with off-the-shelf kits.([Heimdal Security][6])
AI-Powered Ransomware and Next-Gen Threats in 2025
AI-powered and AI-assisted ransomware attacks are harder to detect and stop in 2025 because they generate convincing, personalised phishing and constantly mutate malware to evade traditional defenses. For many SOC teams, this is the single biggest shift in the ransomware threat landscape.
AI-enhanced phishing, deepfakes and social engineering
AI-enhanced phishing and deepfake voice/email attacks make it far harder for users in Seattle, London or Frankfurt to spot social engineering. Attackers use generative AI tools to:
Craft flawless emails in local languages.
Mimic executive writing styles.
Generate audio deepfakes that sound like a real CFO, clinician or partner.
AI allows attackers to personalise phishing at scale, bypassing simple keyword-based content filters and outpacing traditional user awareness training. Combined with compromised MFA prompts or push fatigue, the “human layer” becomes much less predictable.

Self-modifying malware and autonomous intrusion tools
On the technical side, malware increasingly uses AI assistance to mutate, re-pack and dynamically change Indicators of Compromise (IOCs). This makes signature-only defenses obsolete and forces greater reliance on behavioural EDR/XDR analytics.
Attackers also lean on automated discovery tools to map cloud and hybrid estates — from AWS and Azure to on-prem VMware and Kubernetes searching for exposed services, misconfigured IAM roles and vulnerable SaaS integrations. These tools can script lateral movement in minutes, turning a single phished credential into ransomware impacting entire data centres in New York or Frankfurt.
For SOC teams, this raises alert volume and complexity. XDR tools are critical, but without tuned detections, threat hunting and 24/7 monitoring (whether in-house or via MDR), AI-assisted attackers still have the time advantage.
Impact on critical infrastructure and regulated sectors
AI-powered ransomware has severe implications for critical infrastructure and regulated sectors:
US
CISA advisories and joint FBI alerts continue to flag ransomware against hospitals, energy, transport and water utilities as national security issues.
UK
NCSC and NHS guidance emphasise segmented networks, patching and backup design to protect against ransomware that can jump from IT to clinical systems.
Germany/EU
ENISA and national bodies warn that AI-driven malware and extortion put NIS2 essential and important entities (including cloud, SaaS and OT operators) under heightened scrutiny.
Cyber insurance underwriters now routinely ask detailed questions about AI risks, EDR coverage, backup resilience and zero trust adoption before issuing or renewing ransomware cover.
Ransomware, Regulation and Cyber Insurance in 2025 (US/UK/EU)
Compliance and insurance don’t stop ransomware, but in 2025 they heavily influence how you must prepare and respond. Reporting timelines, ransom-payment restrictions and minimum technical controls all shape your ransomware incident response plan.
GDPR/DSGVO, UK-GDPR and NIS2 obligations after ransomware
In Europe, most ransomware incidents that involve data exfiltration become reportable personal-data breaches under GDPR/DSGVO and UK-GDPR. Even if you quickly restore from backups, regulators usually expect notification when attackers have accessed or copied personal data.
Under NIS2, essential and important entities (e.g. hospitals, utilities, cloud and SaaS providers) must submit an early warning within 24 hours, a more detailed report within 72 hours and a final report within one month. Non-compliance can lead to significant fines and increased supervisory attention.
For CISOs in Berlin, Brussels or Amsterdam, ransomware is not just an operational crisis but a regulatory one incident response plans must bake in legal, DPO and CSIRT engagement from the outset.
US requirements HIPAA, PCI DSS, SOC 2 and state laws
In the United States, HIPAA treats many ransomware incidents affecting electronic protected health information (ePHI) as presumed breaches unless you can demonstrate a low probability of compromise.PCI DSS requires rapid investigation and coordination with card schemes for any incident involving payment card data, while SOC 2 for SaaS providers emphasises availability, confidentiality and security controls relevant to ransomware.
Layered on top of this, US state breach-notification laws impose overlapping timelines and thresholds that vary by state. For a SaaS vendor in San Francisco or New York, you may need to coordinate notifications across dozens of states as well as sector regulators.
Reporting, ransom payment restrictions and cyber insurance trends
In the UK, policymakers are actively debating measures to curb ransom payments, especially for critical national infrastructure such as the NHS. Ideas on the table include stricter reporting of ransom payments and even partial bans, with possible national-security exemptions.
In Germany, BaFin and BSI pay particular attention to ransomware resilience in financial services and critical sectors, focusing on backup design, incident reporting and operational continuity.Insurers increasingly refuse to cover ransom payments if certain minimum controls (MFA, EDR/XDR, immutable backups, documented IR playbooks) are missing or poorly implemented.
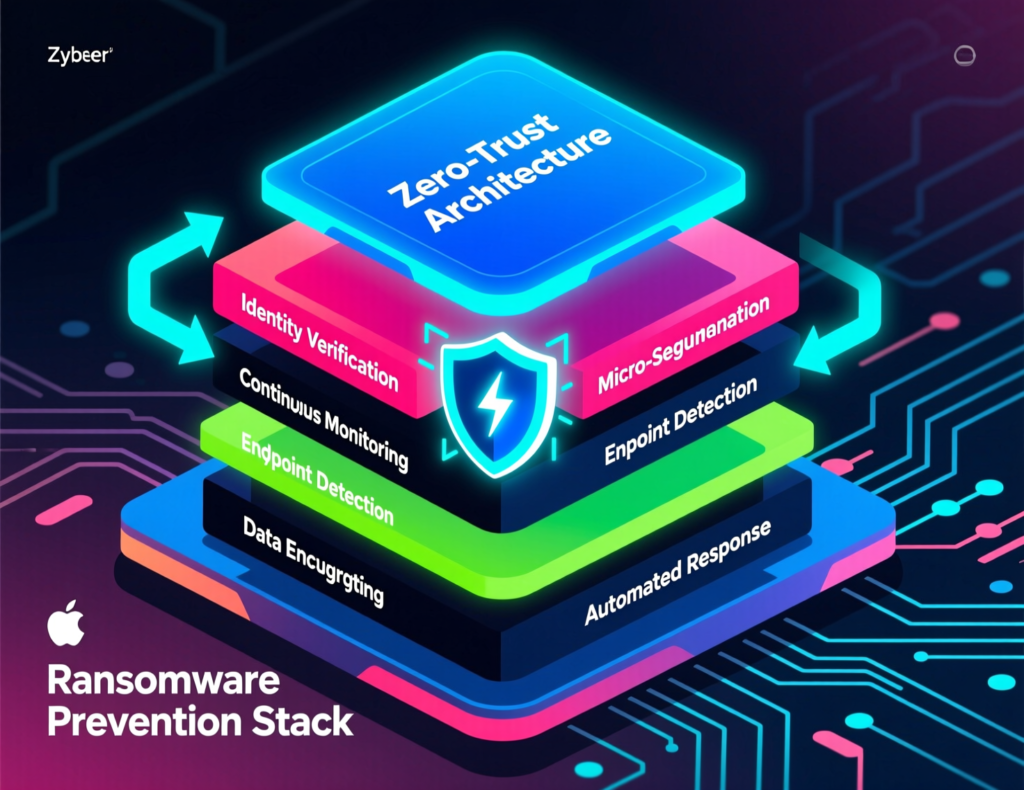
Building a 2025-Ready Ransomware Protection Stack
Effective ransomware protection in 2025 starts with identity, email and endpoint controls working together, backed by resilient backups and a tested incident response plan. For mid-sized organisations in the US, UK and Germany, this is achievable in roughly 90 days with focused effort.
If you’re modernising your stack, you may also be rethinking your cloud, web or SaaS architecture areas where partners like Mak It Solutions can help you align security and scalability across US, UK and EU regions.
Core controls identity, email, endpoint and SaaS protection
A solid 2025 ransomware defense stack typically includes:
Identity-first security
Enforce MFA everywhere, prioritising phishing-resistant methods (FIDO2/WebAuthn, platform authenticators) for admins and high-risk users, aligned with NIST guidance.
Implement privileged access management (PAM) for domain, cloud and SaaS admin roles.
Email and collaboration security
Advanced phishing and attachment/URL inspection for Microsoft 365 and Google Workspace.
Conditional access to block logins from unusual locations or risky devices.
Endpoint, server and cloud workload protection
EDR/XDR on endpoints and critical servers, with centralised logging to a SIEM or XDR console.
Managed detection and response (MDR) or SOC-as-a-Service for 24/7 monitoring if you lack in-house coverage.
SaaS and identity posture management
Regularly audit OAuth apps, shared mailboxes and dormant accounts in SaaS platforms.
When you build or modernise line-of-business or SaaS platforms, integrate these controls into your architecture. Experienced development partners like Mak It Solutions can help bake in identity-first security, logging and backup patterns across web applications and mobile apps from day one.
Zero trust strategy and ransomware backup best practices
Zero trust is no longer a buzzword in ransomware defense it’s how you stop a single phished account turning into a full-domain compromise:
Use zero trust network access (ZTNA) instead of flat VPNs.
Segment OT and critical systems (e.g., hospital EHR and industrial control systems) from general IT.
Apply least privilege to admins, service accounts and third-party vendors.
For backups, 2025 best practice converges on:
The 3-2-1-1 rule (three copies of data, two media types, one off-site, one immutable/offline).
Immutable backups and object-lock in cloud storage, plus periodic offline snapshots.
Isolated backup admin credentials and strict RBAC so ransomware can’t easily delete backups.
The UK NCSC provides detailed principles for ransomware-resistant backups, and CISA’s StopRansomware guide includes step-by-step recovery guidance you can adapt for AWS, Azure and on-prem environments.
People, process and the first 24 hours after an attack
Your incident response plan for ransomware should be simple enough to execute at 2am, yet robust enough to satisfy regulators and insurers:
Define roles (CISO, IT lead, DPO, communications, legal, business owners).
Prepare playbooks for both encryption and data-exfiltration-only scenarios.
Pre-agree how and when to involve DFIR providers, legal counsel, cyber insurers, CISA/FBI (US), NCSC (UK), BSI (Germany) or relevant CSIRTs.
In the first 24 hours, focus on.
Containing the attack (isolate affected systems, disable compromised accounts).
Preserving evidence for forensics and potential law enforcement.
Establishing a high-level regulatory and notification position (GDPR/DSGVO, UK-GDPR, NIS2, HIPAA, state laws).
Communicating clearly with leadership, staff and critical partners; avoid speculative external statements until facts are confirmed.
Mak It Solutions can also help translate these playbooks into operational runbooks embedded in your monitoring and IT workflows, alongside secure-by-design SaaS and cloud architectures.
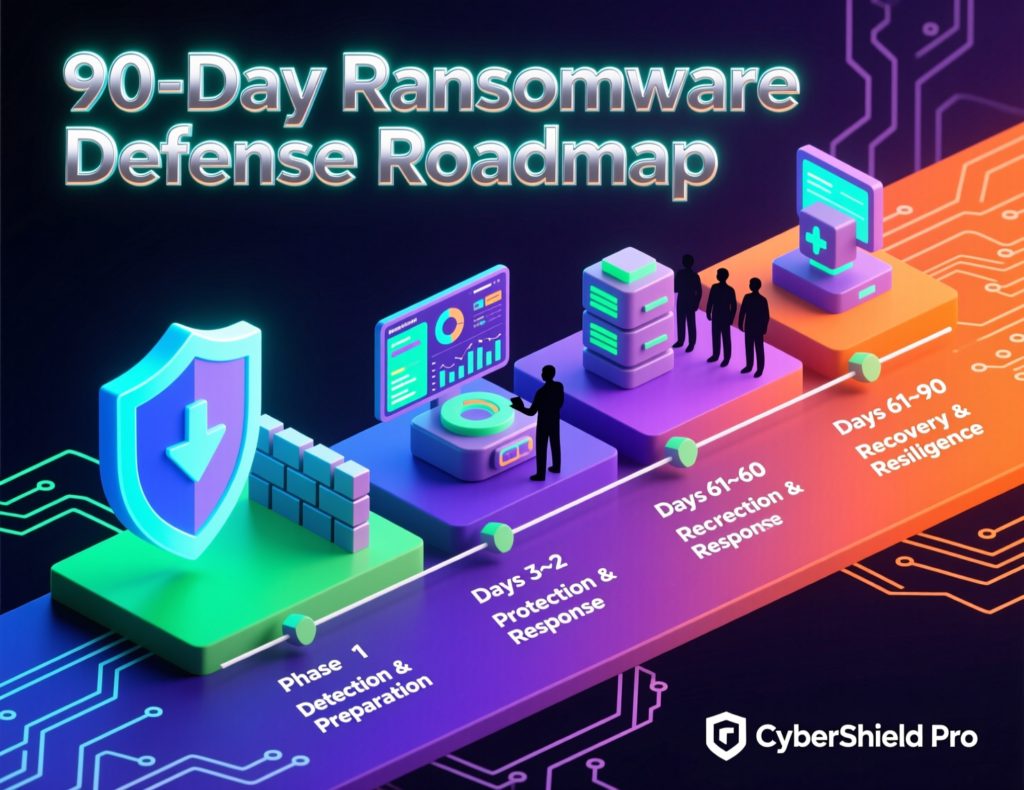
90-Day Roadmap to Stay Ahead of Ransomware Trends 2025
Mid-sized organisations in the US, UK and Germany can significantly improve ransomware resilience in 90 days by combining focused assessment, priority control rollout and realistic testing.
30-day assessment know your exposure
In the first 30 days
Run a targeted ransomware readiness assessment across US, UK and German operations.
Map critical assets: ERP, EHR, core banking/finance, OT/ICS and key SaaS (CRM, HR, collaboration).
Identify regulatory touchpoints (GDPR/DSGVO, UK-GDPR, NIS2, HIPAA, PCI DSS, SOC 2).
Review existing backups and test at least one restore for a key system.
If you lack internal bandwidth, a specialist partner like Mak It Solutions can combine technical discovery with business and compliance mapping especially useful if you operate in both EU/US and GCC or other high-regulation regions.
60-day hardening implement priority controls
Days 31–60 are about execution
Enforce MFA on all remote access, VPN, email and key SaaS apps.
Patch internet-facing systems and high-risk CVEs prioritised by exploit likelihood.
Roll out or tune EDR/XDR coverage for servers, endpoints and cloud workloads.
Harden backups (immutability, segmentation, access controls) and document restore procedures.
Deliver focused phishing and AI-enhanced social engineering awareness campaigns for high-risk roles (finance, HR, executives, IT).
90-day optimisation test, measure and partner up
By days 61–90
Run tabletop exercises simulating double extortion and data exfiltration-only scenarios.
Test a full restore of one critical system and measure Recovery Time Objective (RTO) and Recovery Point Objective (RPO).
Refine your ransomware IR playbooks based on exercise findings.
Decide where external partners (MDR/SOC-as-a-Service, DFIR retainers, secure cloud/web development) add the most value.
Mak It Solutions regularly helps US, UK, German and wider EU organisations align application, cloud and data architectures with their ransomware defense strategies from secure web platforms to analytics and SEO-driven content that educates customers about security posture and resilience.
Key Takeaways
Ransomware trends 2025 show a shift toward AI-enhanced phishing, double/triple extortion and data exfiltration-only campaigns that hit US, UK, German and wider EU organisations across healthcare, manufacturing, finance and the public sector.
Average ransom payments hover around seven-figure amounts, but recovery costs and downtime often exceed the ransom itself, especially where OT or hospital operations are disrupted.
Compliance frameworks (GDPR/DSGVO, UK-GDPR, NIS2, HIPAA, PCI DSS, SOC 2) now assume ransomware will happen and impose strict reporting and security expectations.
A 2025-ready ransomware protection stack starts with identity-first security, email and endpoint protection, zero trust segmentation and ransomware-resistant backups, supported by EDR/XDR and MDR/SOC services.
A clear 30-60-90 day roadmap assessment, hardening and testing/optimisation lets mid-sized organisations materially reduce ransomware risk in a manageable timeframe.
Working with a partner like Mak It Solutions to modernise secure web, mobile and SaaS platforms ensures ransomware resilience is built into your digital products and data pipelines from the start.
If you’d like help turning this ransomware trends 2025 analysis into a concrete 90-day action plan, Mak It Solutions can support you across architecture, implementation and ongoing optimisation. Whether you’re modernising a SaaS platform, hardening cloud workloads or building secure analytics dashboards for US, UK, German or wider EU users, our team can align development and security from day one. Reach out via the Mak It Solutions website to schedule a conversation and get a scoped, practical roadmap tailored to your environment.
FAQs
Q : Is paying a ransomware demand illegal in the US, UK or EU in 2025?
A : Paying a ransomware demand is not universally illegal in the US, UK or EU, but it is heavily discouraged and in some circumstances restricted. In many jurisdictions, paying sanctioned entities or terrorist organisations can breach sanctions law, and UK policymakers are actively exploring tighter rules or partial bans for critical national infrastructure such as the NHS. Cyber insurers and regulators increasingly expect organisations to consider alternatives (restores, rebuilds, law-enforcement engagement) and to document why any ransom decision was taken. Always seek legal advice before making payment decisions.
2. What is the average downtime and business cost after a ransomware attack in 2025?
Average downtime after ransomware varies by sector and preparedness, but many organisations report at least a week of disruption, with roughly one-third needing more than a month to fully recover complex environments.Business costs typically include lost revenue, overtime, forensics, legal fees, regulatory penalties, customer compensation and reputational damage. Industry surveys suggest total recovery costs can easily exceed $1.5M for mid-sized and larger organisations, even when the ransom itself is relatively small or not paid at all.
Q : Which sectors are hit hardest by ransomware in 2025, and why?
A : Healthcare, manufacturing, financial services, public sector and education remain the most frequently and severely impacted. Hospitals and NHS trusts are critical because downtime directly affects patient safety and care continuity; manufacturing and OT-heavy sectors in Germany and wider EU are targeted due to tightly coupled, time-sensitive production processes; financial services face high-value data and direct monetary impact; and public sector and education often run legacy systems with constrained budgets.These characteristics make them attractive for double and triple extortion.
Q : How does cyber insurance treat ransom payments and double extortion in 2025?
A : Cyber insurance policies in 2025 are more selective about covering ransom payments. Many require strong baseline controls such as MFA, EDR/XDR, tested backups and documented incident response plans as prerequisites.Insurers also differentiate between single, double and triple extortion; coverage may be narrower for data-leak and reputational harms, especially where regulatory fines or sanctions risks are involved. Some insurers actively encourage incident reporting to CISA, NCSC or national authorities and may refuse payment where ransom negotiations undermine law-enforcement operations.
Q : What should be included in a 2025 ransomware incident response playbook for US, UK and EU organisations?
A : A 2025-ready ransomware IR playbook should define roles and escalation paths; include clear steps for containment, forensics and backup restores; and map regulatory obligations (GDPR/DSGVO, UK-GDPR, NIS2, HIPAA, state breach laws). It should outline when to contact law enforcement (FBI, CISA, NCSC, BSI or national CSIRTs), cyber insurers and external DFIR teams, and it should distinguish between encryption events and data-exfiltration-only extortion.([Internet Crime Complaint Center][13]) Finally, it needs communication templates for staff, customers, regulators and the media, plus a schedule for regular tabletop exercises.


