Secure Your GCC SME with an Incident Response Plan
Secure Your GCC SME with an Incident Response Plan
Secure Your GCC SME with an Incident Response Plan
An incident response plan for SMEs in the GCC is a short, written playbook that explains who does what when a cyberattack hits, from first alert to full recovery. For 2026, SMEs in Saudi Arabia, the United Arab Emirates and Qatar should align this plan with national cybersecurity rules, define clear roles, document key “cyber incident lifecycle” stages, and keep everything bilingual so teams can act fast under pressure.
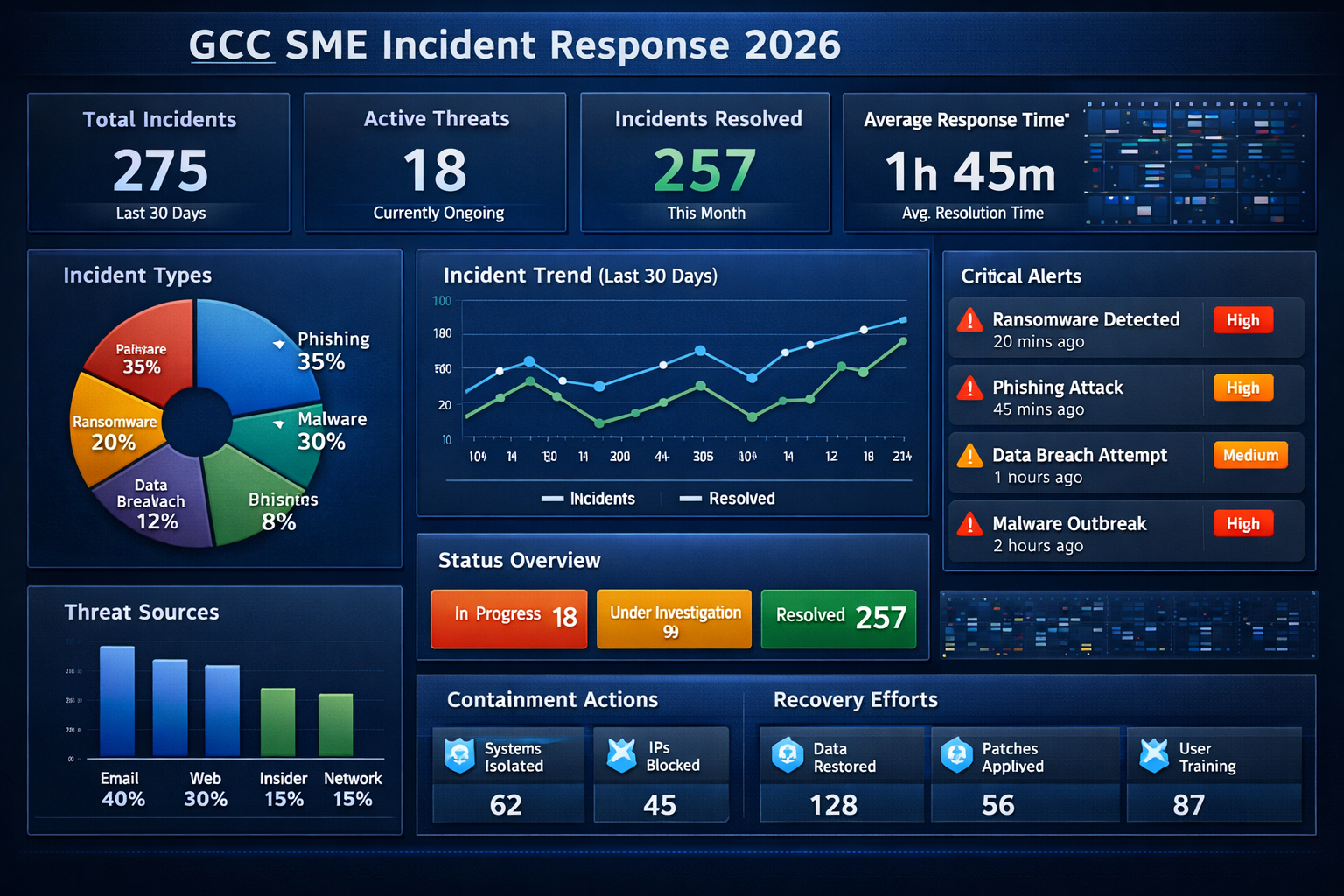
In 2026, SMEs across the Gulf Cooperation Council (GCC) are being hit by ransomware, business email compromise and targeted phishing that feels “too sophisticated” for small teams. Attackers know that a 30-person firm in Saudi Arabia or a family business in the United Arab Emirates often has banking access, cloud systems and supplier data but no in-house security team.
Regulators like the National Cybersecurity Authority (NCA), Saudi Central Bank (SAMA) Telecommunications and Digital Government Regulatory Authority (TDRA) and Qatar Central Bank (QCB) now expect even small organizations to show they can detect, contain and report incidents properly. Yet most SMEs still only have a generic “IT policy”.
In plain English: a GCC incident response plan for SMEs is a short, practical document that tells your team exactly how to handle a cyber incident from first alert to “post-incident review and root cause analysis”. For GCC SMEs, this guide gives you a simple cyber incident lifecycle, region-specific compliance pointers, and a 2026-ready template structure you can adapt in Word or PDF.
Note
This article is general guidance, not legal or regulatory advice. Always check the latest national frameworks and consult your legal or compliance advisors where needed.
What Is an Incident Response Plan for SMEs in the GCC?
Plain-English definition for busy SME owners
An incident response plan is a step-by-step playbook for handling hacks, fraud and data leaks, not just a generic IT policy. It explains who takes charge, how you investigate, which systems you isolate, how you talk to customers and banks, and when you notify regulators. Even a 10–50-person clinic in Riyadh or trading firm in Dubai needs this written down so decisions aren’t made in panic over WhatsApp.
Cyber incidents vs business continuity and disaster recovery
Business continuity and disaster recovery focus on keeping operations running after physical or large-scale outages like your data centre going down or a major cloud outage. Incident response is narrower and sharper: security incident detection and containment for things like a hacked email, malicious transfer, or compromised POS terminal. You might still stay open for business, but your plan tells you how to limit damage, collect evidence and avoid making the situation worse.
Real-world SME cyber incidents in Saudi, UAE and Qatar
Think of a payroll officer at a logistics SME in Jeddah who clicks a fake “HR update” and sends salaries to an attacker’s IBAN. Or a small clinic in Riyadh locked by ransomware the night before appointments, with patient files encrypted. In Dubai, a trading company approves a fake supplier invoice after a business email compromise. In Doha, a professional services firm accidentally exposes client documents via misconfigured cloud storage. These are typical cases your plan must cover.
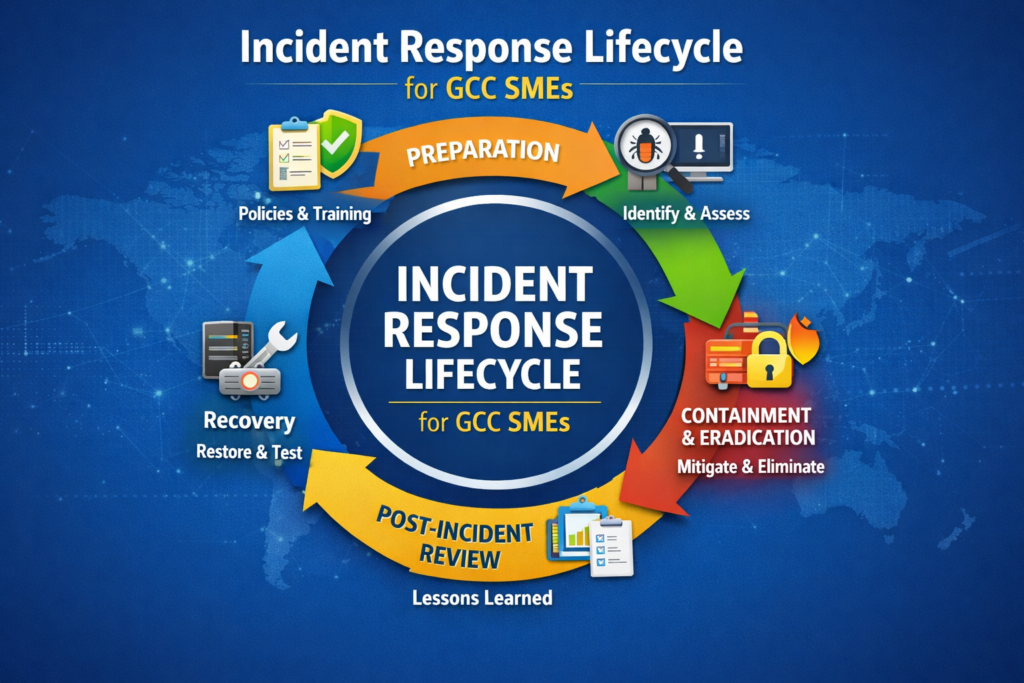
Core Stages of the Incident Response Lifecycle for Small Businesses
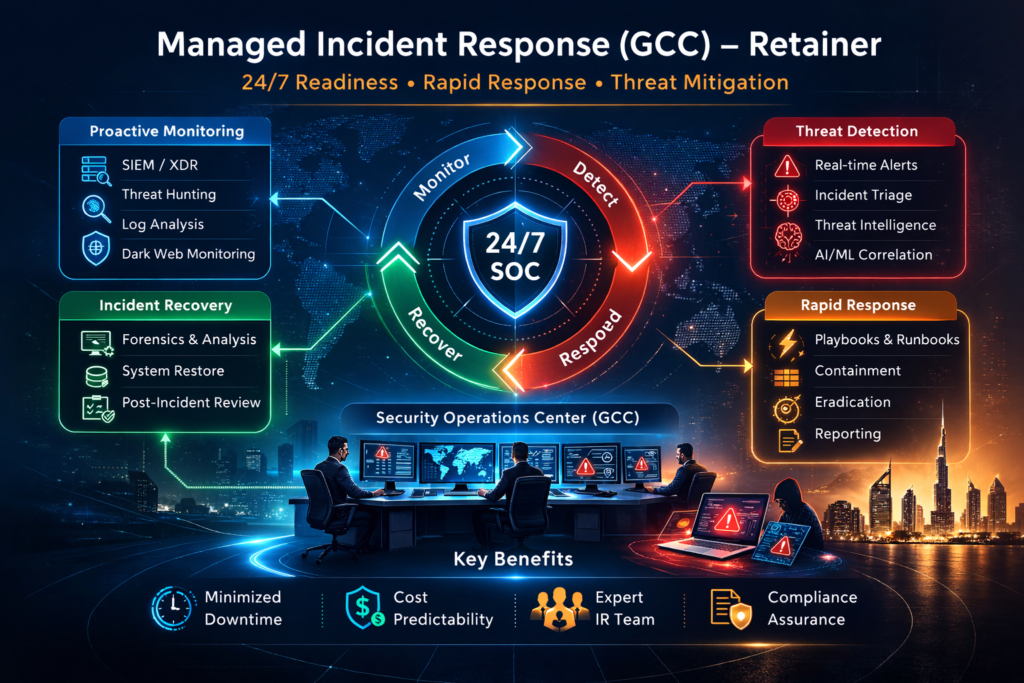
For small businesses in the GCC, the cyber incident lifecycle usually follows five stages: Prepare, Detect & Analyse, Contain & Eradicate, Recover and Lessons Learned. Your 2026 plan should describe each stage in one or two pages, tailored to your actual tools and people.
Prepare policies, contacts and tools ready before an attack
Preparation is your small business cyber resilience strategy. List critical assets (accounting systems, clinic HIS, e-commerce platform), name one incident owner, and create a call tree with Arabic and English contacts. Ensure you have basic EDR/antivirus, logging on cloud accounts, and tested backups ideally in a local cloud region like AWS Bahrain or Azure UAE Central so data residency needs are easier to meet.
Detect & Analyse spotting incidents early in SME environments
Most SME incidents start with small signals: login alerts from unusual locations, invoice details quietly changed, or your website suddenly redirecting to a spam page. Decide who checks bank notifications, email security alerts and web dashboards, and how often. Your plan should define what counts as a “suspected incident”, who triages it within 15–30 minutes, and when to escalate to external support.
Contain & Eradicate stopping the spread without killing the business
Containment for SMEs is about simple, low-risk moves: resetting compromised accounts, isolating affected laptops from Wi-Fi, disabling suspicious API keys and blocking malicious domains or IPs. The plan should clarify when it’s safe to disconnect a branch office VPN, and when you must immediately call your bank or a managed incident response provider. Eradication focuses on removing malware, closing exposed ports and tightening rules, not just “reboot and hope”.
Recover & Lessons Learned bringing systems back safely
Recovery should be controlled: restore systems from clean backups, verify integrity, then gradually bring services like POS, online banking, or patient portals back online. After every major incident, run a short “lessons learned” meeting to document root cause, update policies and training, and refine your incident response plan for SMEs. This review closes the loop and feeds into stronger controls.
GCC Regulatory Expectations for SME Incident Response
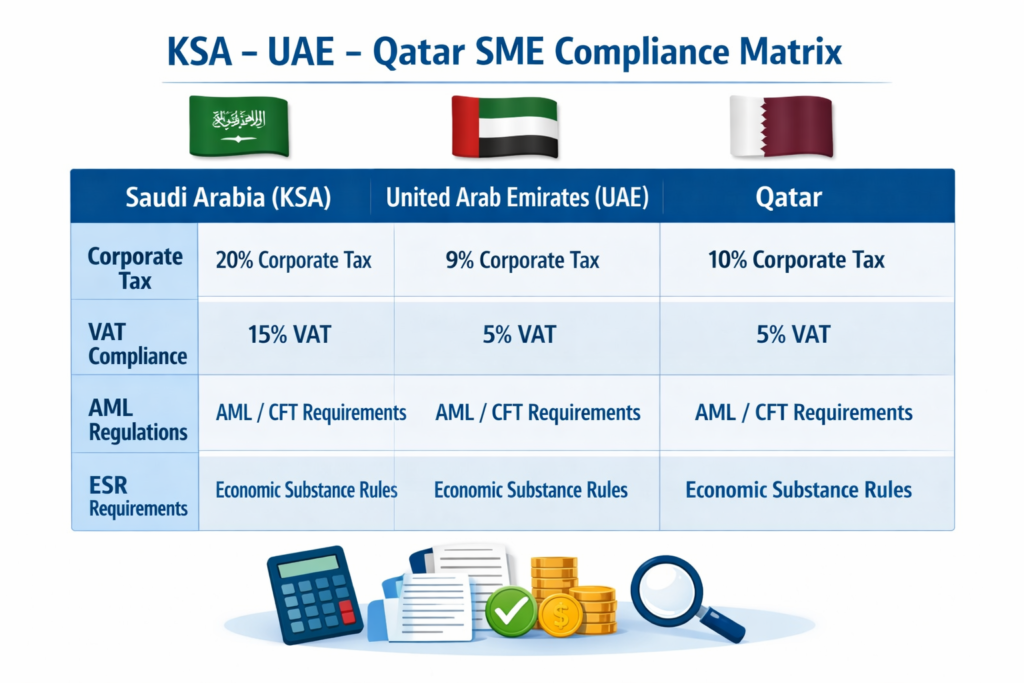
Saudi Arabia aligning SME plans with NCA ECC and SAMA
For KSA SMEs, especially banks and fintechs, the incident response section of your plan should mirror the National Data Management Office (NDMO) and NCA Essential Cybersecurity Controls: clear roles, classification of incidents, logging, evidencing, and defined escalation paths.Under SAMA’s Cyber Security Framework, financial SMEs must also define incident management processes, reporting lines and regulatory breach notification timelines (banking & fintech) so serious cases are reported promptly to SAMA.
Snippet for KSA SMEs:
To align with national controls, a KSA SME’s plan should include named roles, severity levels, log and evidence requirements, containment steps, communication templates, and clear timelines for reporting severe incidents to NCA or SAMA where applicable.
UAE incident response expectations under UAE Information Assurance / NESA
In the UAE, TDRA’s Information Assurance Regulation and the older NESA IAS standards expect entities and key suppliers to maintain incident management policies, classification, escalation, and evidence collection capabilities.Even if you are an SME vendor to a large government entity or a bank in Abu Dhabi or Dubai, your plan should show who can coordinate with their security team, how quickly you’ll notify them, and how you’ll support investigations in zones like Abu Dhabi Global Market (ADGM) or Dubai International Financial Centre (DIFC)
Qatar building on QDB Cyber Security Manual, NCSA and QCB
Qatar SMEs can lean heavily on the Qatar Development Bank (QDB) Cyber Security Manual and frameworks from the National Cyber Security Agency (NCSA) to define simple playbooks and training. Financial and payments-focused SMEs must also reflect QCB’s requirements on secure operations, monitoring and incident handling, particularly for PSPs and fintechs.
Snippet for Qatar SMEs
Use the QDB Cyber Security Manual and NCSA guidance as your checklist: define key assets, common threats (phishing, BEC, ransomware), response steps and contact lists, then turn those into short, role-based playbooks for your Doha teams.
Data residency, logs and cross-border forensics in the GCC
Data residency rules driven by NDMO in KSA, sectoral rules in the UAE and QCB/NCSA expectations in Qatar affect where logs, backups and forensic data can live. Wherever possible, configure logging and backups to regional cloud regions (like AWS Bahrain or GCP Doha) and document in your plan which providers can access what. For serious cross-border cases, your plan should mention when to engage national bodies such as Qatar Computer Emergency Response Team (Q-CERT) or sector regulators.
How to Build a 2026 Incident Response Plan for Your SME
Map your business, risks and roles
Start by listing your critical services: POS and stock systems for retail, HIS for clinics, payment gateways for fintech, or custom portals for government suppliers. Decide who owns cyber incidents at director level and who leads Arabic and English communications. Build a simple RACI so everyone from finance to IT support knows their role before an attack.
Structure your written plan using a 2026 SME template
Next, structure the document: scope, definitions, severity levels, incident lifecycle, communication matrix, regulator notifications, supplier contacts and a playbook index. Keep it to 8–15 pages so managers will actually read it. This is where you can plug in a Mak It Solutions-style template and tailor it to your sector and country.
Create focused playbooks for top SME threats
Turn the core template into 2–4 one-page playbooks: ransomware on a file server, phishing/BEC against finance, website compromise, and lost laptop/mobile. A fintech startup in Riyadh, for example, can map SAMA incident expectations into its payment-fraud playbook, while a Dubai e-commerce brand focuses on card theft and site defacement, and a Doha SME aligns its response with QDB guidance.
Localise for KSA, UAE and Qatar regulations
Finally, add country-specific annexes instead of drowning your main plan in legal text. Separate checklists for NCA ECC and SAMA, UAE IA/NESA, and QDB/NCSA/QCB help you tick regulatory boxes efficiently. This keeps your core process clean while still showing auditors and partners you respect national requirements.
Training, Templates and Tabletop Exercises for GCC SME Teams
Bilingual phishing and incident response checklists for staff
Most incidents start with people, so give staff a one-page Arabic/English checklist: what to do if they click a suspicious link, see a ransom note, or receive a strange WhatsApp from a “supplier”. Keep the language friendly and concrete screenshots, examples, and a big “Call this number immediately” box.
Running a 2-hour tabletop exercise for your management team
Once or twice a year, run a 2-hour tabletop exercise: for example, Friday-night ransomware before salary payments, or a fake email from the CEO asking to transfer funds. Walk through your incident lifecycle, simulate phone calls to banks and regulators, and note every confusion or delay. Those notes become immediate improvements to your plan.
Embedding incident response in onboarding and vendor management
Add incident response responsibilities into HR onboarding: new staff learn how to report issues on day one. For vendors especially cloud, IT and payment partners include basic incident response clauses in contracts: notification timelines, responsibilities and language support. Review all of this at least annually in a short management meeting.
When to Use Managed Incident Response & Retainers in the GCC
Signals you need external incident response help
You probably need external help if you’ve had repeated phishing or fraud, operate across multiple branches or clouds, or feel pressure from regulators, banks or major customers. Another red flag: nobody in your team is comfortable leading an incident outside office hours.
Choosing between local GCC SOCs, MSPs and global providers
Local GCC SOCs and MSPs often bring Arabic-speaking analysts and lived experience with NCA, UAE IA, QCB, ADGM and DIFC rules. Global providers may offer deeper tooling but weaker local context. For most SMEs, a regional partner plus clear playbooks strikes the right balance.
What a practical SME incident response retainer looks like in 2026
A realistic retainer for SMEs includes a defined number of incident hours, remote support, one annual tabletop exercise, and a yearly review of your incident response plan for SMEs. It should also help you align with regulators and cloud providers, not just send you a bill after incidents.
Putting It All Together 2026-Ready Incident Response for GCC SMEs
Quick checklist for your 2026 SME incident response plan
Your 2026 checklist should include.
Clear lifecycle: Prepare, Detect & Analyse, Contain & Eradicate, Recover, Lessons Learned
Named roles and escalation paths
2–4 focused playbooks for common threats
Mapped regulatory expectations (NCA/SAMA, UAE IA/NESA, QDB/NCSA/QCB)
Bilingual training and tabletop exercises
Basic logging, secure backups and data residency awareness

Next steps for SMEs in Saudi Arabia, UAE and Qatar
Over the next 30 days, document your first GCC incident response plan for SMEs, build one or two priority playbooks and schedule a mini tabletop with leadership. Then review national guidance and close obvious gaps. Finally, explore a light incident response retainer so you’re not alone at 2am.
How to use and maintain the downloadable 2026 template
Treat your plan as a living document. Update it at least yearly, or after any major incident, system change or new regulation. Store it securely in your cloud and on-prem, with limited edit permissions but easy read access for managers, and rehearse it until it becomes muscle memory.
If you’d like help turning this guidance into a tailored, regulator-ready GCC incident response plan for SMEs, the team at Mak It Solutions can support you whether you operate a fintech in Riyadh, a retail brand in Dubai or a services firm in Doha. Explore our broader services overview and specialist web development services or mobile app development services if your incident response depends on custom platforms. When you’re ready to review your existing plan or build one from scratch, simply contact our team for a GCC-focused consultation.
FAQs
Q : Is an incident response plan mandatory for small businesses under Saudi NCA ECC or SAMA rules?
A : The NCA Essential Cybersecurity Controls and SAMA Cyber Security Framework mainly target national and financial entities, but their requirements effectively cascade to many SMEs through contracts and audits. In practice, if you handle sensitive data for banks, fintechs or government entities in Saudi Arabia, you’re expected to demonstrate incident response capabilities that align with these controls clear roles, documented processes, logging and timely reporting. Even when not explicitly “mandatory” by law, having a plan is essential to pass assessments and meet Vision 2030 digital expectations.
Q : How often should a UAE SME test its incident response plan to stay aligned with UAE Information Assurance / NESA expectations?
A : Under UAE IA and related NESA-style standards, entities are expected to maintain and regularly test incident management processes, not just write them once. A practical rhythm for SMEs is to review the plan every 12 months and run at least one tabletop exercise per year, plus a shorter check whenever systems or suppliers change. For high-impact sectors or government suppliers, more frequent simulations every six months help prove to TDRA-regulated customers that your controls are truly effective, not just paperwork.
Q : Do Qatar SMEs need to report every cyber incident to QCB or only severe ones affecting customers and payments?
A : Most Qatar regulations, including QCB’s technology and information security rules for PSPs and fintechs, focus on significant incidents that affect service availability, data confidentiality, integrity or customer funds. Minor internal issues that are quickly contained may be handled locally, provided they are logged and reviewed. However, anything that disrupts payments, compromises sensitive customer data or could impact financial stability should be escalated through your internal process and, where required, formally reported to QCB and other bodies such as NCSA or Q-CERT. Your playbooks should clearly distinguish between “minor”, “major” and “critical” cases.
Q : What’s the simplest way for a micro-business in Riyadh or Dubai to start an incident response plan without a full-time IT team?
A : For micro-businesses, the key is to keep things short and realistic. Start with a two-page document listing critical systems, key contacts (including your bank and main IT provider), steps for dealing with a suspicious email or payment request, and how to disconnect compromised devices. Use free or low-cost security tools from your cloud and email providers, and agree in advance who will take decisions if something serious happens. You can then gradually mature this into a fuller plan using templates and guidance from national frameworks in Saudi Arabia and the UAE.
Q : How can GCC SMEs coordinate incident response across branches in Saudi, UAE and Qatar when using shared cloud services?
A : Cross-border SMEs should centralize incident ownership while respecting local laws. Appoint a regional incident lead plus local coordinators in each country, and store logs and backups in compliant cloud regions for each jurisdiction. Your plan should define one common process, but with annexes covering NCA/SAMA expectations for KSA, UAE IA/NESA requirements for UAE, and QDB/NCSA/QCB guidance for Qatar. During an incident, use shared collaboration tools but be careful about where sensitive evidence is stored, and involve local legal or compliance advisors before notifying regulators.