Zero Trust Roadmap for SMEs in GCC (Step-by-Step)
Zero Trust Roadmap for SMEs in GCC (Step-by-Step)
Zero Trust Roadmap for SMEs in GCC (Step-by-Step)
A practical zero trust roadmap for SMEs in Saudi, UAE and Qatar starts with stabilising identities, access and endpoints in the first 90 days, then gradually introducing zero trust network access (ZTNA), segmentation and continuous monitoring over 3–12+ months. Instead of ripping and replacing firewalls, GCC SMEs can layer an identity-centric security model on top of what they already have, aligned with SAMA, TDRA and Qatar Central Bank expectations.
Introduction
A mid-sized trading company in Riyadh recently lost a week of operations after a simple phishing email led to ransomware spreading across a flat network where everyone used the same VPN and shared “admin” passwords. Stories like this are becoming uncomfortably common for SMEs in Saudi Arabia and the wider region.
For SMEs across United Arab Emirates and Qatar, the risk now looks like a bank’s risk: cloud apps everywhere, remote users, third-party vendors and regulators asking hard questions. But most SMEs still have one “IT guy”, an old VPN, a single firewall at HQ and growing compliance pressure.
Here’s a clear zero trust roadmap for SMEs in the GCC: a three-phase plan (0–90 days, 3–12 months, 12+ months), how to align it with frameworks from the Saudi Central Bank (SAMA), the Telecommunications and Digital Government Regulatory Authority (TDRA) and Qatar authorities, and how to do it without a big-bang replacement of your existing tools. While examples focus on Saudi, UAE and Qatar, the same patterns apply to SMEs in Kuwait, Bahrain and Oman.
Note.
This guide is for general awareness and does not replace formal legal, regulatory or financial advice.
What Is Zero Trust Security for GCC SMEs?
From Perimeter Security to Zero Trust in SMEs
Traditional security assumed a strong perimeter: once a user was “inside” the office or VPN, they were trusted. For many GCC SMEs this still means a single firewall, a site-to-site VPN and broad access for anyone who connects. Remote work, SaaS and third-party vendors have broken this castle-and-moat model.
Zero trust flips this mindset into an identity-centric security model: every user, device and session must be verified continuously, whether they sit in the office, in a branch in Jeddah or on 4G in Dubai. Access to your ERP, accounting system or HR portal is granted based on identity, device health and context not just network location.
Core Zero Trust Principles for SMEs in KSA, UAE and Qatar
In business language, the core principles look like this.
Never trust, always verify
Every login to email or your cloud CRM must pass multi-factor authentication and basic device checks.
Least privilege access control
Finance staff only see finance systems; warehouse users only see WMS; admins have named accounts, not shared ones.
Assume breach
Design your environment so that if one laptop in Doha is compromised, the attacker cannot automatically reach your finance database.
Continuous authentication and authorisation
Risky logins (new country, unusual device) face extra checks or limited access.
For SMEs, this can start with simple policies: no more shared accounts, admin access via privileged accounts only, and role-based access to accounting, payroll and customer data.
Why Zero Trust Is Becoming Essential for GCC SMEs
Attackers increasingly go after SMEs in the supply chains of banks, oil & gas and government projects. Ransomware, email takeover in Arabic and English, and stolen cloud credentials are now routine. If your company supports a major bank in Riyadh, a ministry in Abu Dhabi or a project owner in Doha, you are part of their risk surface.
Zero trust gives you a structured, auditable way to show big customers and regulators that access is tightly controlled, monitored and logged even if your internal team is small.
GCC SME Reality: Constraints, Risks and Readiness
Limited Security Teams and Shared IT Roles
In many SMEs, one person runs helpdesk, servers, Wi-Fi, vendors and “security” for 100+ users. Others lean on an outsourced IT provider who keeps systems running but doesn’t own risk or compliance. There’s rarely a CISO or cyber lead, which makes complex frameworks hard to implement.
A practical zero trust roadmap for SMEs in this reality must assume limited in-house skills and time. It should lean on simple configuration changes, managed services and automation rather than big internal security teams.
Legacy VPNs, Flat Networks and Shadow SaaS
The typical setup: one VPN account shared by multiple people, a flat LAN where finance, HR, dev and guest Wi-Fi all talk to each other, and dozens of unapproved SaaS tools in use by marketing or sales. This makes lateral movement trivial for attackers.
Zero trust doesn’t mean replacing everything overnight. It means tightening identity controls on what you already use, then layering zero trust network access (ZTNA) and micro-segmentation of networks over time.
Compliance Pressure from SAMA, TDRA and Qatar Frameworks
SMEs providing services to banks, telecoms or government entities are increasingly asked about access control, logging and data protection. Partners expect you to show who can access what, from where, and with which approvals.
A structured roadmap gives you a way to map controls to SAMA’s cybersecurity expectations, TDRA linked UAE guidance and Qatar’s national strategies turning a technical journey into something your board and auditors can understand.
Step-by-Step Zero Trust Roadmap for SMEs in GCC
Direct answer (AEO): For GCC SMEs with small teams, a practical zero trust roadmap has three phases: stabilise identities and devices in the first 90 days, introduce ZTNA and segmentation over 3–12 months, then automate monitoring and compliance mapping after 12 months. Each phase builds on the previous one, so you can move at your own pace without disrupting business.
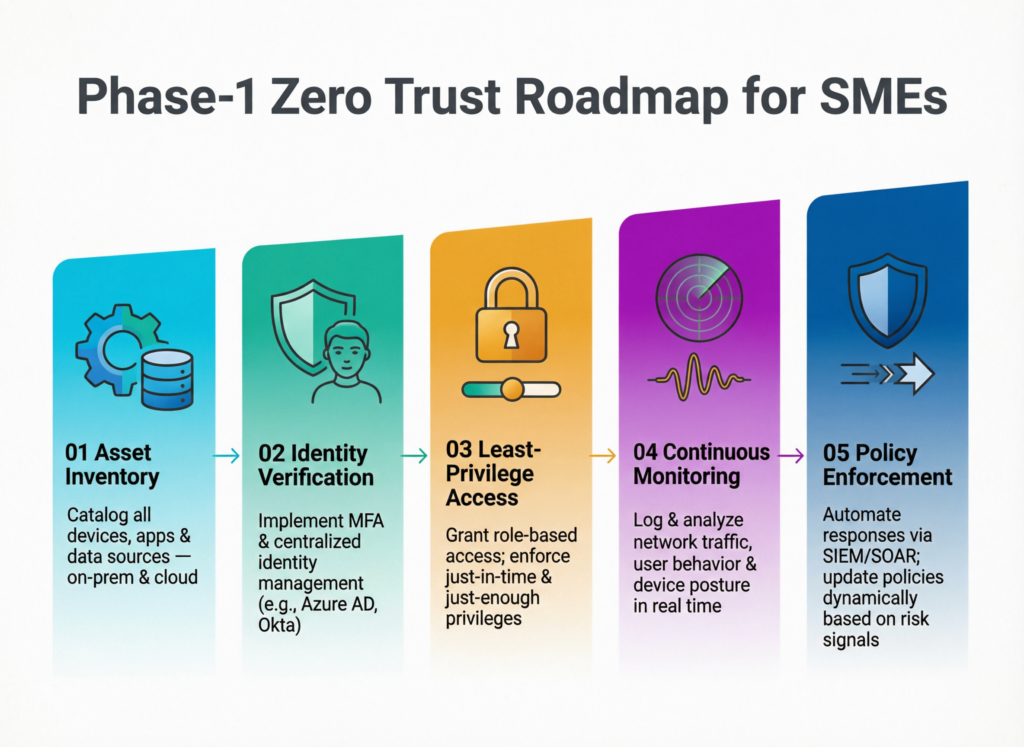
Phase 1 (0–90 Days) Stabilise Identities, Access and Endpoints
In the first 90 days, focus on low-cost, high-impact controls: enable MFA for email, VPN and critical SaaS, remove shared accounts and patch key devices. These steps alone drastically reduce risk for small businesses in Saudi and UAE.
Core actions
Inventory
List users, laptops/phones and critical apps (ERP, finance, HR, CRM, cloud storage). Identify your “crown jewels”.
Access hygiene
Enforce MFA, disable shared accounts, ensure ex-employees lose access and implement basic least privilege on systems like accounting and CRM.
Endpoint basics
Standardise OS patching, deploy EDR/AV, enforce disk encryption on laptops and set secure configuration baselines.
Phase 2 (3–12 Months) Introduce ZTNA, Segmentation and Strong Policies
Phase 2 is where the zero trust roadmap for SMEs becomes visible in daily operations:
Zero trust network access (ZTNA)
Start with remote access to one or two apps e.g., finance portal or internal CRM while keeping legacy VPN for other workloads during transition.
Segmentation
Separate finance from guest Wi-Fi, production from test, and OT/IoT devices (CCTV, POS, sensors) from core business systems.
Role-based access control
Formalise roles (finance analyst, branch manager, contractor), assign permissions and schedule access reviews every quarter.
Phase 3 (12+ Months) Automate, Monitor and Integrate with Compliance
Once the basics are stable, you can act more like a regulated enterprise even as an SME.
Centralised logging and alerting: Use a managed SIEM/SOC provider to collect logs from firewalls, ZTNA, your identity provider and key apps.
Continuous authentication and device posture: Enforce conditions such as “no access from unmanaged devices” or “step-up MFA for high-risk logins”.
Compliance alignment: Map your controls to internal policies, risk registers and audit evidence for SAMA, TDRA or QCB, so security work directly supports regulatory obligations.
Mapping Your Zero Trust Roadmap to GCC Regulations
Aligning Zero Trust Controls with SAMA and NDMO in Saudi Arabia
Saudi SMEs working with banks or fintechs often face questionnaires based on the SAMA Cybersecurity Framework. Zero trust helps you answer them with confidence: identity and access management, privileged access, logging and monitoring all align directly to SAMA domains.
Data classification, residency and backup strategy can be linked to guidance from the National Data Management Office (NDMO), especially when using cloud regions such as AWS Bahrain for sensitive workloads. Having a documented zero trust roadmap for SMEs shows banks and partners that your controls are maturing over time, not just on paper.
Connecting Zero Trust to UAE National Cybersecurity Strategy and TDRA Guidance
In the UAE, the National Cybersecurity Strategy and TDRA-linked initiatives emphasise resilience, continuous monitoring and incident readiness. Least privilege, strong identity controls and centralised logging all support these objectives.
For SMEs in Dubai and Abu Dhabi especially those serving government entities or operating in smart city projects showing structured ZTNA, segmentation and monitored access makes it easier to pass vendor risk assessments and security due diligence.
Considering Qatar’s NCSA and QCB Expectations for SMEs
In Qatar, smaller financial and fintech players supervised by the Qatar Central Bank increasingly need to show that customer data and payment processes are tightly controlled. Zero trust gives you a simple narrative: access is identity-driven, logged and regularly reviewed; production data is segregated from test; third-party access is time-bound and monitored.
Doha-based SMEs can also strengthen data protection by choosing nearby cloud regions such as GCP Doha and encrypting sensitive data both in transit and at rest.
Technology Choices: ZTNA, SASE and Managed Services for GCC SMEs
Using Existing Firewalls and VPNs Versus Moving to ZTNA
Most SMEs in the region cannot afford to replace their entire network in one go. A phased approach uses existing firewalls and VPNs as a base while gradually moving critical apps behind ZTNA.
“VPN plus” might mean keeping the tunnel for less sensitive systems while putting finance, HR and admin portals behind a ZTNA service with strong identity checks. Over time, as confidence grows, more apps move to zero trust network access and the old VPN is retired.
Comparing Global Platforms with Local MSSPs in Riyadh, Dubai and Doha
Global ZTNA/SASE vendors offer powerful platforms, but many SMEs prefer working with local managed security service providers (MSSPs) in Riyadh, Dubai or Doha. Local partners can configure, monitor and respond in Arabic and English, understand tender requirements and coordinate on-site when needed.
A hybrid model often works best: a global platform for technology and a regional MSSP for implementation, monitoring and regulatory interpretation.
Budgeting Zero Trust for SMEs in KSA, UAE and Qatar
Budget discussions should mirror your phases:
0–90 days
Mostly configuration changes plus modest MFA and EDR licences.
3–12 months
ZTNA/SASE licences, segmentation projects and some professional services.
12+ months
Managed SOC or SIEM, advanced automation and periodic audits.
Framing spend this way helps founders and CFOs in Saudi Arabia, UAE and Qatar see zero trust as a staged investment rather than a one-off “big bang” project.
Practical Zero Trust Use Cases and Quick Wins in GCC Industries
Fintech and Regulated Startups in ADGM, DIFC and Riyadh
A fintech in Abu Dhabi Global Market (ADGM) or Dubai International Financial Centre (DIFC), or a payment startup in Riyadh, can use zero trust to protect admin portals, APIs and core platforms. Admin access is limited to named accounts with MFA; developer access to production is via just-in-time approvals; all activity is logged for investors and regulators.
Government Suppliers and Critical Infrastructure SMEs Across GCC
SMEs supplying ministries, smart city projects or OT environments often plug into government portals and SCADA systems. Zero trust lets them isolate project environments, enforce least privilege for engineers and contractors, and restrict access to specific apps rather than whole networks. This both reduces risk and makes tender responses much stronger.
Retail, Logistics and Distributed Workforces in Dubai and Doha
A retail and logistics SME with branches in Dubai, Jeddah and Doha can use zero trust to secure POS terminals, warehouse systems and last-mile delivery apps. ZTNA can restrict access so branch staff only see their local systems, while micro-segmentation keeps POS, guest Wi-Fi and back-office systems separate. Using cloud regions like Azure UAE Central for ERP and GCP Doha for analytics helps with performance and data locality.
Governance, Culture and Next Steps for GCC SMEs
Building an Identity-Centric Security Culture Across Arabic and English Teams
Zero trust fails if people still share passwords on WhatsApp. SMEs should run simple awareness sessions in Arabic and English focused on phishing, MFA and why identity-centric security matters. Make it clear who owns security decisions: founders for risk appetite, IT for implementation and line managers for access approvals.
Measuring Zero Trust Maturity and Communicating with Executives
You don’t need a complex framework. A simple maturity model (initial, developing, defined, optimised) mapped to your zero trust roadmap for SMEs is enough. Track metrics like percentage of users with MFA, number of privileged accounts, high-risk alerts per month and mean time to respond. Use visuals in executive updates to show progress each quarter.
When to Engage a Local Zero Trust Partner in KSA, UAE or Qatar
It’s time to bring in a partner when alerts become noise, multi-cloud is getting complex or regulators start asking detailed technical questions. Look for providers with real GCC references, experience mapping to SAMA/TDRA/Qatar requirements and the ability to integrate with your existing stack. A digital partner such as Mak It Solutions can also connect your security roadmap with your broader web, mobile and data platforms.
If you’re an SME in Saudi Arabia, UAE or Qatar, zero trust doesn’t have to be overwhelming or expensive. A clear three-phase plan can take you from shared passwords to regulator-ready security in manageable steps.
Mak It Solutions can help you design and implement a practical zero trust roadmap that aligns security, cloud and application development whether you need strategy only or end-to-end execution. Reach out to discuss your environment, and we’ll map a tailored 90-day and 12-month plan for your business.( Click Here’s )
FAQs
Q : Is zero trust security mandatory for SMEs working with banks or fintechs in Saudi Arabia and the UAE?
A : Zero trust itself is not usually named as a mandatory standard, but SMEs working with banks, fintechs or financial regulators must meet strict cybersecurity and access-control requirements. Frameworks such as the SAMA Cybersecurity Framework in Saudi Arabia and UAE financial sector expectations emphasise strong identity management, logging and least-privilege controls. A zero trust approach is often the easiest way for a small supplier to demonstrate that access to banking or payment data is tightly governed, monitored and revocable when contracts end.
Q : Can a small company in Riyadh or Dubai start zero trust without hiring a full-time CISO?
A : Yes. Many SMEs in Riyadh and Dubai begin their zero trust journey with a small internal owner (often the head of IT or operations) supported by an external security partner. The first phases MFA rollout, removing shared accounts, basic segmentation do not require an in-house CISO. Over time, you can formalise governance through a virtual CISO service, managed SOC and quarterly risk reviews. This model aligns well with national initiatives such as Saudi Vision 2030 and UAE digital-transformation programmes, which encourage SMEs to adopt mature security without excessive overhead.
Q : How does zero trust help GCC SMEs comply with data residency rules when using cloud services?
A : Zero trust and data residency work together. By tightly controlling identity, device posture and access paths, SMEs can confidently use cloud regions that respect local rules such as AWS Bahrain, Azure UAE Central or GCP Doha while limiting who can reach sensitive workloads. Policies can restrict access based on user role, geography and device health, with all activity logged for audits. This makes it easier to show regulators or partners that personal and financial data is processed in approved locations and only by authorised, verified users.
Q : What is the difference between VPN and ZTNA for remote workers in Doha or Abu Dhabi?
A : Traditional VPNs create a secure tunnel into your entire network: once connected, users often see far more than they need. Zero trust network access (ZTNA) instead grants access only to specific applications, based on identity and device checks. For remote workers in Doha or Abu Dhabi, this means they connect to, say, ERP and email—not to the whole office LAN. ZTNA also enables granular logging, conditional access and easy revocation, supporting expectations from bodies like TDRA and Qatar’s national cybersecurity initiatives.
Q : How long does it usually take a small GCC business to reach a basic zero trust maturity level?
A : Most small GCC businesses can achieve a solid basic zero trust posture in 9–18 months if they follow a phased roadmap. The first 90 days cover high-impact actions such as MFA, inventory and endpoint hardening. Months 3–12 focus on ZTNA, segmentation and role-based access control. Beyond 12 months, SMEs typically add managed detection, continuous authentication and deeper compliance mapping. The pace depends on complexity and resources, but aligning with national strategies like Saudi Vision 2030 or Qatar’s digital-economy goals can help secure internal support and budget.