DevSecOps in Middle East for Saudi & UAE Leaders
DevSecOps in Middle East for Saudi & UAE Leaders

DevSecOps in Middle East for Saudi & UAE Leaders
DevSecOps in the Middle East means designing CI/CD pipelines where development, operations and security teams in Saudi Arabia, the UAE and Qatar work as one to automate security and compliance from day one. In practice, it combines secure CI/CD tooling, cloud controls and policy-as-code so organisations can meet frameworks like SAMA, TDRA and QCB without slowing product delivery.
Introduction
In Riyadh, Dubai and Doha, cyber security has moved from an “IT issue” to a board-level business risk. For many CIOs and CISOs, the pressure is clear: deliver more digital products, on mobile and cloud, while proving alignment with SAMA, ECC-2, TDRA, PDPL, NDMO and QCB. At the same time, talent is scarce and most teams are working in bilingual Arabic/English environments across multiple time zones.
DevSecOps in Middle East is how GCC organisations turn that pressure into an advantage. In simple terms, DevSecOps in MENA means building CI/CD pipelines where security and compliance are automated into every commit, merge and deployment so a Riyadh bank, a Dubai smart city project or a Doha fintech can move fast without losing control. Instead of bolting on security at the end, DevSecOps brings security engineers, developers and ops together around one shared delivery pipeline and one set of policies.
Mak It Solutions already sees this pattern in broader cloud modernisation and DevOps work for global clients, and the same lessons apply directly to regulated GCC teams. You don’t need a Silicon Valley-sized engineering org to adopt DevSecOps; you need a realistic roadmap, the right controls and the right partners.
What DevSecOps in Middle East Really Means for MENA Organisations
From global DevSecOps definition to GCC reality
Globally, DevSecOps is “DevOps with security built in”: shared ownership, automation, and continuous testing throughout the secure software development lifecycle (SSDLC). In the GCC, the context is sharper: most Saudi, UAE and Qatar organisations operate under sector regulators, national cyber strategies and data residency rules that affect every architecture decision.
For a Saudi bank or TPP in Open Banking KSA, DevSecOps means.
Pipelines that enforce SAMA Cybersecurity Framework and ECC-2 controls automatically.
Environments tagged and isolated for different data classifications under NDMO and PDPL.
Deployments restricted to approved cloud regions like AWS Middle East (Bahrain) or me-central-1 in the UAE and Doha.
For UAE digital government services (such as UAE Pass–backed portals), DevSecOps adds continuous security and compliance monitoring to already fast-paced agile delivery. For Qatar e-government platforms, it means building on top of local cloud regions (GCP Doha, Azure Qatar Central) with clear evidence of where data lives.
DevSecOps vs traditional AppSec for MENA banks and fintechs
Traditional AppSec in many GCC banks still looks like: long checklists, manual reviews before go-live, and penetration tests once or twice a year. This keeps auditors happy on paper, but security issues typically appear late when a release is already committed to a date or a regulator.
DevSecOps in MENA financial services is different:
Security gates are inside the CI/CD pipeline (SAST, SCA, IaC checks) instead of at the very end.
Threat modelling is done with product and business teams early, especially for Open Banking APIs and high-risk journeys like onboarding and KYC.
Security teams provide reusable policies and templates rather than individual approvals.
The result is faster release cycles with fewer emergency fixes exactly what SAMA, TDRA and QCB expect when they talk about “risk-based” and “mature” cyber postures rather than just forms and checklists.
How DevSecOps supports Vision 2030 and UAE digital government goals
Saudi Vision 2030, UAE digital government and Qatar National Vision 2030 all hinge on reliable, citizen-centric digital services. DevSecOps is one of the practical ways to translate those strategies into day-to-day behaviour:
Vision 2030 projects in KSA (smart cities, digital health, logistics platforms) need repeatable, compliant pipelines more than bespoke heroics.
UAE digital government initiatives like UAE Pass benefit from standardised secure CI/CD so new services don’t each reinvent security.
Qatar’s e-government and digital ID efforts rely on both local cloud regions and clear segregation-of-duties, which DevSecOps helps encode into tooling.
For GCC leaders, DevSecOps is not just a technical trend it’s one of the delivery engines of national digital strategies.
Compliance-Led DevSecOps in Saudi Arabia, UAE and Qatar
SAMA Cybersecurity Framework, ECC-2 and NDMO.
Saudi banks and fintechs are expected to align with the SAMA Cybersecurity Framework, ECC-2 and NDMO data management controls. These frameworks require documented secure SDLC, vulnerability management, logging, and incident response not just firewalls.
In DevSecOps terms, key SAMA/ECC-2 controls translate into:
Secure SDLC → mandatory SAST/SCA in CI, branch policies, signed commits.
Vulnerability management → automated dependency checks, container image scanning and defined SLAs per severity.
Logging & monitoring → centralised logs from pipelines and runtime, linked to SOC workflows.
Change management → pull-request workflows with approvals, plus immutable deployment history.
Saudi teams can start by mapping each SAMA control to a concrete pipeline control, then using one pilot product to validate that SAMA evidence can be exported directly from CI/CD and cloud platforms.
TDRA, UAE Information Assurance and National Cybersecurity Strategy
TDRA and the UAE Information Assurance Regulation require critical UAE entities to adopt specific cyber controls, particularly around risk management, asset inventory, incident handling and data protection.
For a Dubai or Abu Dhabi team, the DevSecOps view is:
Tag CI/CD projects and cloud resources according to UAE IA classifications.
Require code, infrastructure as code and container manifests to be scanned automatically before deployment.
Use Azure UAE North/UAE Central or AWS me-central-1 for workloads that must stay in-country, with conditional policies preventing accidental deployment elsewhere. ([AWS Documentation][5])
This approach gives CISOs an evidence trail aligned with the UAE National Cybersecurity Strategy while keeping sprint velocity intact.
QCB and sectoral rules in Qatar.
Qatar Central Bank (QCB) guidance focuses heavily on protecting payment systems, banking platforms and customer data. When combined with national cyber directives and Qatar’s push for local cloud, it implies:
Strong access controls on CI/CD, with MFA and role-based permissions for production deployments.
Segregation between build, test and production environments, with non-production data anonymised.
Use of local regions like GCP me-central1 (Doha) or Azure Qatar Central for sensitive workloads, plus clear backup and DR patterns.
If DevSecOps pipelines can produce auditable logs and configuration drift reports, QCB audits become faster and less painful.
Integrating Security into GCC CI/CD and Cloud-Native Pipelines
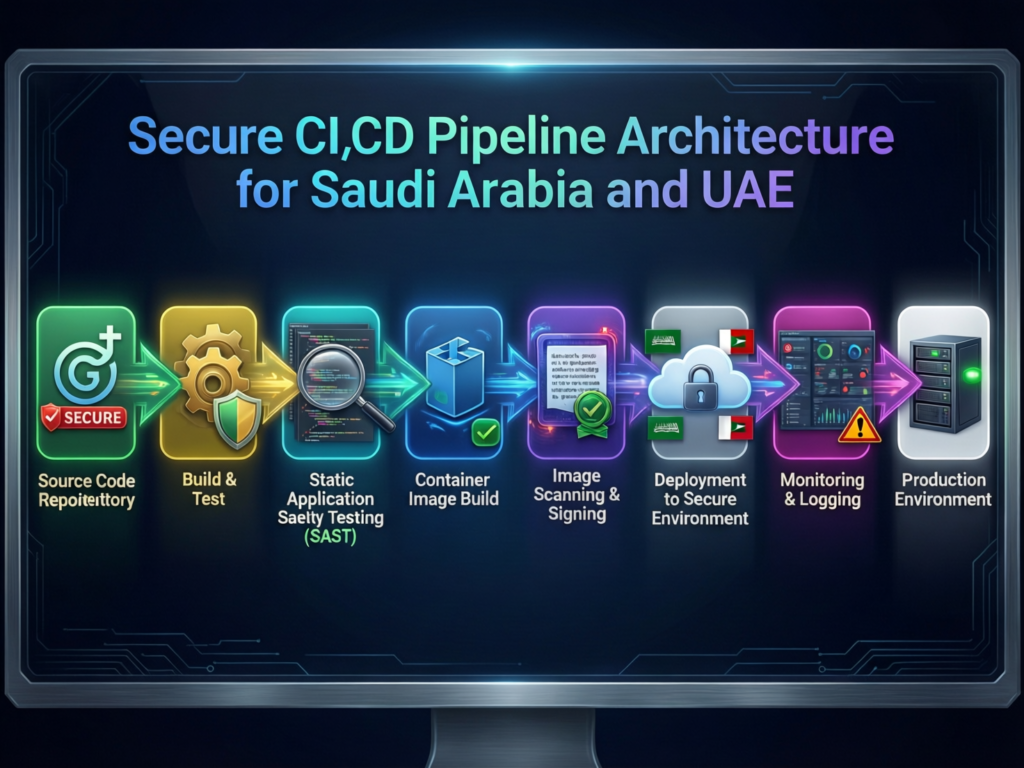
Example secure CI/CD pipeline for a Riyadh or Dubai product team
So, what does DevSecOps look like in a Saudi or UAE CI/CD pipeline in practice? A typical pattern for a bank, fintech or government portal might be.
Commit & merge
Developers push to Git; protected branches enforce code review and security checks.
Build stage
Unit tests, SAST and software composition analysis run automatically.
Security gate
If high-severity issues appear, the pipeline fails and tickets are created.
Package & scan
Containers are built, signed and scanned; IaC templates are checked for misconfigurations.
Deploy to staging
DAST, API testing and performance tests run against a staging environment.
Approval & production
Only authorised roles can approve promotion to production, with full logging for NDMO and regulator audits.
Teams working with Mak It Solutions often pair this with broader architecture choices like monolith vs microservices and cloud region strategy, using playbooks similar to those in their microservices vs monolith and cloud comparison guides.
Shift-left security testing.
GCC leaders often ask: how can we integrate SAST/DAST and secrets scanning into pipelines without slowing releases? A pragmatic approach is to shift left gradually:
Run fast SAST and secrets scanning on every push; reserve heavier tests for merges or nightly pipelines.
Use SCA and container scanning to keep third-party libraries and base images in check.
Automate policy-as-code, for example blocking deployments if high-risk issues exist in internet-facing services.
Instead of security “stopping” a release on launch day, the pipeline becomes the negotiation space developers see issues immediately, and security teams define the rules in code.
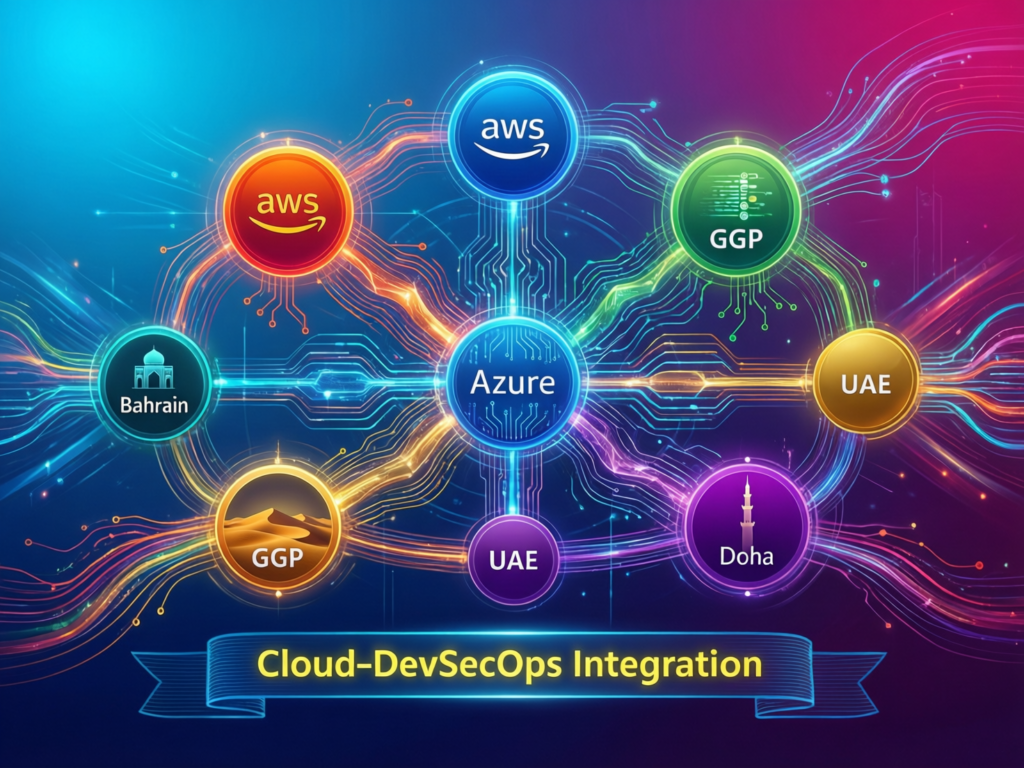
Cloud DevSecOps on AWS Middle East, Azure UAE and GCP Doha regions
For GCC organisations, cloud DevSecOps is really about using local regions safely.
AWS Middle East (Bahrain & UAE) for Saudi and GCC banks that want proximity and data residency.
Azure UAE North/UAE Central and Qatar Central for public sector and telecoms workloads that require in-country processing.
GCP Doha (me-central1) for Qatar digital government and analytics projects that must stay under local jurisdiction.
DevSecOps adds identity guardrails (least-privilege IAM, workload identities), network baselines (private endpoints, service meshes), and continuous compliance checks. Articles such as Mak It Solutions’ AWS vs Azure vs Google Cloud comparison and cloud cost optimization guides show how to align these technical choices with TCO and governance, not just security.
DevSecOps Adoption & Culture in GCC Organisations
Ownership between security, DevOps and product in bilingual teams
In KSA, UAE, Qatar, Kuwait, Bahrain and Oman, most teams are bilingual and multi-cultural. That’s a strength—but only if ownership is clear. A practical RACI often looks like:
Product owns risk appetite, customer impact and prioritisation.
Engineering/DevOps owns pipelines, infrastructure as code and run-time reliability.
Security owns policies, threat models and validation of controls.
Regular rituals joint threat-modelling workshops, bilingual playbooks, shared dashboards matter more than job titles. Mak It Solutions’ work on human-centred change management shows that without this cultural layer, even the best DevSecOps tools fail.
Data residency, logging and segregation-of-duties in regulated GCC sectors
Saudi PDPL, NDMO guidance and sectoral policies in UAE and Qatar all stress data residency, logging and proper segregation-of-duties. In DevSecOps terms this means.
Pipelines deploying personal or financial data must target approved regions only.
Logging covers both the app and the pipeline (who approved what, when and from where).
No single engineer can both approve code and push to production in critical systems especially in banks, healthcare and telecoms.
This is exactly where DevSecOps overlaps with governance and cost controls; teams often reuse the same tagging and policies used for cloud cost optimization to enforce compliance and audit readiness.
Working around the DevSecOps talent gap.
Every GCC CIO knows the problem: there simply aren’t enough senior DevSecOps engineers. Recent analysis of IT brain drain and talent flows in Arab countries shows how the GCC is competing globally for cloud, security and data skills.
Practical responses include:
Managed DevSecOps platforms run by a partner like Mak It Solutions, who already operate CI/CD, cloud and observability for multiple clients.
Virtual security guilds across Riyadh, Jeddah, Dubai and Doha, where a small number of experts define patterns consumed by product teams.
Capability-building engagements, combining architecture, DevOps and coaching, similar to the way Mak It Solutions approaches microservices, blockchain in MENA and change management for regulated industries.
GCC DevSecOps scenarios in practice
A Riyadh fintech aligns its pipeline with SAMA CSF by enforcing encryption-by-default, mandatory SAST and secrets scanning before any API touching Open Banking data is deployed.
A Dubai e-commerce and logistics platform uses infrastructure as code, container security and blue/green deployments to keep releases frequent while staying compliant with UAE IA.
A Doha SME hosting citizen-facing services uses GCP Doha plus GitOps workflows to keep all code, logs and backups within Qatar while still adopting Kubernetes and managed databases.
Skills, Training and Tooling for DevSecOps in MENA
Upskilling developers and ops into DevSecOps engineers in Riyadh, Dubai and Doha
Most GCC DevSecOps engineers start as strong developers or SRE/ops people. The fastest path is usually to upskill your existing teams rather than wait for “unicorn” hires from abroad.
Typical learning journeys include:
Core cloud certifications (AWS, Azure, GCP) tied to local regions like AWS Bahrain or Azure UAE.
Security fundamentals: NIST, ISO 27001, SAMA CSF, UAE IA, QCB requirements.
Hands-on labs in SAST/DAST tools, IaC security and Kubernetes hardening.
Mak It Solutions’ content on IT certifications and GCC talent strategy can help HR and L&D teams structure long-term upskilling across Saudi Arabia, UAE and Qatar.

Choosing GCC-friendly DevSecOps tools for secure CI/CD
When picking DevSecOps tools, GCC leaders should ask three questions:
Can this run in or integrate cleanly with AWS Bahrain, Azure UAE, or GCP Doha?
Does it support Arabic where necessary (dashboards for business stakeholders, localised notifications)?
Can it export evidence aligned with SAMA, TDRA and QCB audits?
Some teams run cloud-native security scanners inside the same regions as their workloads, while others choose SaaS tools but restrict data sharing. Mak It Solutions often helps clients combine these tools with front-end, back-end and BI services so DevSecOps is part of a wider modernisation strategy, not a separate silo.
Building an internal DevSecOps Center of Excellence for banks, government and telecoms
A DevSecOps Center of Excellence (CoE) is a small team that owns standards, patterns and enablement. In GCC banks, government and telecoms, a CoE typically:
Defines golden pipeline templates (e.g., for mobile apps, APIs, data platforms).
Curates a “blessed” toolchain aligned with SAMA, TDRA and QCB guidance.
Measures maturity over time across portfolios in Riyadh, Jeddah, Dubai, Abu Dhabi and Doha.
Partners like Mak It Solutions can bootstrap the CoE by providing reusable blueprints, then gradually hand ownership back to your internal engineers similar to how they support cloud, Adobe Commerce and blockchain programmes elsewhere.
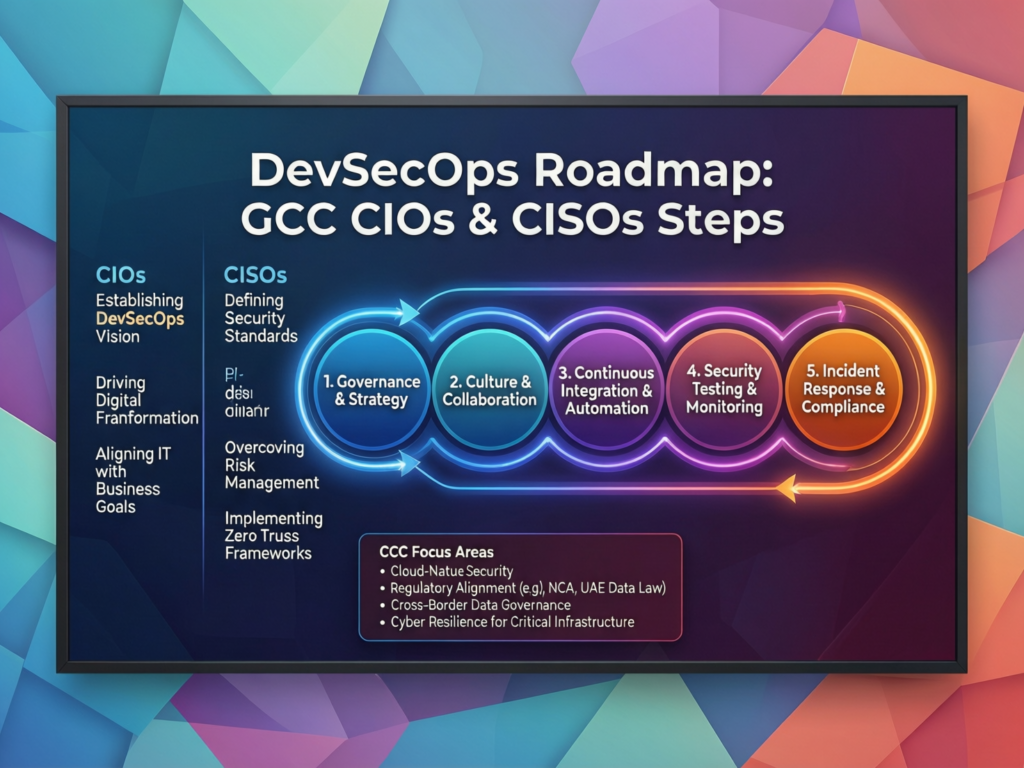
A Practical DevSecOps Roadmap for GCC CIOs and CISOs
Assess current SDLC, CI/CD and compliance gaps
Start with a focused assessment across your Saudi, UAE and Qatar application portfolio:
Map business-critical systems – payments, core banking, citizen portals, telecoms OSS/BSS, logistics platforms.
Baseline controls where do you already have CI/CD, automated tests, cloud security baselines, monitoring?
Overlay this with SAMA, TDRA, QCB and PDPL/NDMO requirements so you can see which applications represent the highest combined business and regulatory risk. A short discovery engagement with a partner like Mak It Solutions (who already offer services across web, mobile, BI and cloud cost optimisation) can accelerate this step.
Pilot secure CI/CD, then scale patterns across teams
Next, choose one high-value product for example, a Riyadh bank’s mobile app, a Dubai digital government service or a Doha e-commerce platform and.
Implement a full DevSecOps pipeline (SAST, SCA, secrets scanning, container and IaC checks, basic DAST).
Harden cloud environments in AWS Bahrain, Azure UAE or GCP Doha, with clear tagging, RBAC and network baselines.
Treat this pilot as a reference implementation. Document patterns in Arabic and English, then roll them out to additional squads with coaching and “inner sourcing” of reusable modules.
Establish metrics, governance and the right DevSecOps partners in GCC
Finally, stabilise and scale.
Define metrics time to remediate vulnerabilities, percentage of services with secure CI/CD, audit findings closed per quarter.
Formalise governance and partnerships SLAs with cloud and DevSecOps partners, CoE charters, and clear escalation paths.
Many GCC organisations find it easier to keep a long-term DevSecOps partner on retainer (for platform engineering, coaching and architecture reviews) while building local talent over time. This is similar to how Mak It Solutions supports microservices migrations, change management, and blockchain pilots without forcing a single pattern on every product.
Concluding Remarks
DevSecOps in Middle East is not a buzzword; it’s the practical way Saudi, UAE and Qatar organisations turn compliance pressure into a secure delivery advantage. By embedding security into CI/CD, aligning pipelines with SAMA, TDRA, QCB and PDPL, and using local cloud regions wisely, GCC leaders can move faster and reduce risk.
You don’t need to transform everything at once one pipeline, one product, one portfolio at a time is enough. If you’d like a GCC-specific DevSecOps assessment or roadmap workshop, Mak It Solutions can help you connect the dots between architecture, security, culture and cloud.
If you’re a CIO, CISO or digital leader in Saudi Arabia, the UAE or Qatar and you’re unsure where to start with DevSecOps in Middle East, you don’t have to figure it out alone. Mak It Solutions combines hands-on engineering (cloud, CI/CD, web and mobile) with advisory work on governance, skills and culture across GCC markets.
Reach out via the Mak It Solutions services hub to request a DevSecOps readiness assessment, or discuss a tailored roadmap for your Riyadh, Dubai, Abu Dhabi or Doha teams. Together, you can design secure CI/CD pipelines that satisfy SAMA, TDRA and QCB without slowing your products down.
FAQs
Q : Is DevSecOps formally required for Saudi banks under the SAMA Cybersecurity Framework and ECC-2?
A : DevSecOps is not named explicitly in the SAMA Cybersecurity Framework or ECC-2, but the outcomes they expect documented secure SDLC, continuous vulnerability management, strong logging and incident response are much easier to achieve with DevSecOps practices. For Saudi banks and fintechs, using automated CI/CD pipelines with SAST, SCA, secrets scanning and infrastructure as code is the most practical way to demonstrate compliance over time. It also helps align technology with Vision 2030, where regulators expect institutions to be both innovative and resilient. In practice, most SAMA-supervised institutions are moving in a DevSecOps direction even if they still use other labels internally.
Q : How does DevSecOps help UAE government entities meet the National Cybersecurity Strategy and UAE IA controls?
A : The UAE National Cybersecurity Strategy and UAE Information Assurance Regulation require strong governance around critical systems, from asset inventories to risk management and incident handling. DevSecOps helps by standardising how software is built and deployed: every change passes through the same automated checks, approvals and logging. For ministries, authorities and smart city programmes in Dubai and Abu Dhabi, this means fewer one-off exceptions and a clearer evidence trail for TDRA and internal audits. When CI/CD pipelines run in Azure UAE or AWS me-central-1, and policy-as-code enforces region and access restrictions, compliance becomes part of day-to-day delivery instead of a separate project.
Q : Can Qatar and GCC organisations adopt DevSecOps while keeping code, logs and data inside local cloud regions?
A : Yes. In fact, DevSecOps often makes data residency easier to guarantee, not harder. By codifying infrastructure and deployments, Qatar and broader GCC teams can enforce that all workloads and logs stay in local regions like GCP Doha (me-central1), Azure Qatar Central or nearby AWS Middle East regions Pipelines can include automated checks that fail if a resource is created outside approved geographies. Combined with strong IAM policies and centralised logging, this gives QCB and other sector regulators clear assurance that sensitive data never leaves agreed jurisdictions. Over time, the same patterns can be reused across banking, government, telecoms and healthcare workloads.
Q : What are realistic timelines and maturity stages for DevSecOps adoption in a Riyadh bank or Dubai fintech?
A : Most Riyadh banks or Dubai fintechs can reach a solid baseline DevSecOps maturity in 12–18 months if they focus on one portfolio at a time. Early stages usually involve building pipelines for a few flagship apps, adding SAST/SCA and basic secrets scanning, and hardening access to cloud environments. Once that’s stable, teams add DAST, container security and more sophisticated policy-as-code. A mature stage is where most teams in the bank or fintech use standardised, secure pipelines, and security engineers operate as internal consultants rather than manual approvers. Working with a partner like Mak It Solutions can shorten timelines by reusing proven patterns from previous GCC and international projects, while still aligning with SAMA, TDRA and QCB expectations.
Q : How much budget should CIOs/CISOs in Saudi and UAE allocate for DevSecOps tools, training and consulting in year one?
A : Budgets vary widely, but many Saudi and UAE organisations start by allocating 5–10% of their overall IT or security budget to DevSecOps in the first year. That typically covers CI/CD and security tooling licences, cloud costs for non-production environments, and focused consulting plus training for core squads in Riyadh, Jeddah, Dubai and Abu Dhabi. The goal is not to buy every tool at once, but to invest in one or two strong pipelines, a minimum set of scanners and observability, and structured upskilling aligned with Vision 2030 and the UAE National Cybersecurity Strategy. As DevSecOps matures and demonstrates fewer incidents and smoother audits, it becomes easier to justify higher investment or managed services models in later years.


