Identity-First Security: From Zero Trust to Resilience
Identity-First Security: From Zero Trust to Resilience

Identity-First Security: From Zero Trust to Resilience
Identity-first security is a model where every access decision is anchored on a verified, continuously evaluated identity human, machine or AI agent rather than on a “trusted” network perimeter.
In 2026, enterprises in the US, UK and EU are using identity-first security as the control plane for Zero Trust architectures and cyber resilience, reducing lateral movement, tightening compliance and keeping critical services online even during attacks. Put simply: identity-first security turns Zero Trust from a slogan into day-to-day reality.
In 2026, identity-first security has quietly become the control plane for Zero Trust and cyber resilience. Instead of trusting anything “inside the network,” organisations make every access decision based on verified, continuously evaluated identity, backed by least privilege access control and continuous authentication and authorization.
For CISOs and security architects in the US, UK, Germany and the wider EU, this playbook walks through what identity-first security actually means, how it underpins Zero Trust, how it supports GDPR, UK-GDPR, NIS2, HIPAA and PCI DSS expectations, and how to design a practical roadmap with vendor-neutral criteria and examples from New York, London, Frankfurt and Berlin.
Note
This article shares practical patterns and references, but it’s not legal or compliance advice. Always confirm details with your legal, risk and regulatory teams.
Introduction
Identity-first security is an identity-centric security model where users, devices, workloads and APIs are continuously authenticated and authorised on every request, regardless of network location. Instead of relying on a VPN or firewall perimeter, access is granted using least privilege access control, based on risk signals tied to identity, device posture and context.
In practice, identity-first security unifies IAM, SSO, MFA, adaptive policies and identity threat detection and response (ITDR) into a single control plane. It makes it possible to treat every connection as untrusted by default, while still giving people and systems a usable experience.
Why identity replaces the network perimeter for modern enterprises
Identity is replacing the network perimeter because the old assumptions about “inside vs outside” are broken. Remote work, SaaS sprawl, hybrid cloud and APIs mean most critical access now happens over the internet, not from a single office LAN. Machine identities and service accounts now outnumber human identities by more than 80:1, creating a huge attack surface if credentials are reused or over-privileged.
For buyers, the pain shows up as lateral movement after a single compromised VPN account, credential abuse across SaaS tenants, shadow IT subscriptions and complex compliance audits. Identity-first security responds by:
Evaluating identity and device posture per request, not once at login.
Using hybrid cloud security posture management to understand where identities can reach.
Deploying ITDR to detect anomalous behaviour like impossible travel, privilege escalation or suspicious API calls.
The result: a much smaller blast radius when (not if) an attacker gets a foothold.
How the market is converging on identity-first Zero Trust
The market has noticed. Identity security is being folded into broader platforms aimed at AI-era threats, and identity-first security is now table stakes for Zero Trust, not a niche add-on.
Palo Alto Networks has completed a $25B acquisition of CyberArk, explicitly positioning identity security as a core pillar of its platform and highlighting that nearly 90% of organisations have already experienced an identity-centric breach.
CrowdStrike is acquiring identity startup SGNL for around $740M to add “continuous identity” and dynamic authorisation to its Falcon platform, focusing on human, machine and AI identities.
Ping Identity has acquired Keyless to add privacy-preserving, zero-knowledge biometrics and passwordless MFA for AI-powered threat resilience.
Alongside established IAM, ZTNA, ITDR, SSPM and XDR platforms from vendors like Okta, Microsoft, Google Cloud, CrowdStrike, Zscaler and Palo Alto Networks, this consolidation reflects a simple reality: Zero Trust built on networks alone isn’t enough. Identity has become the primary enforcement plane.
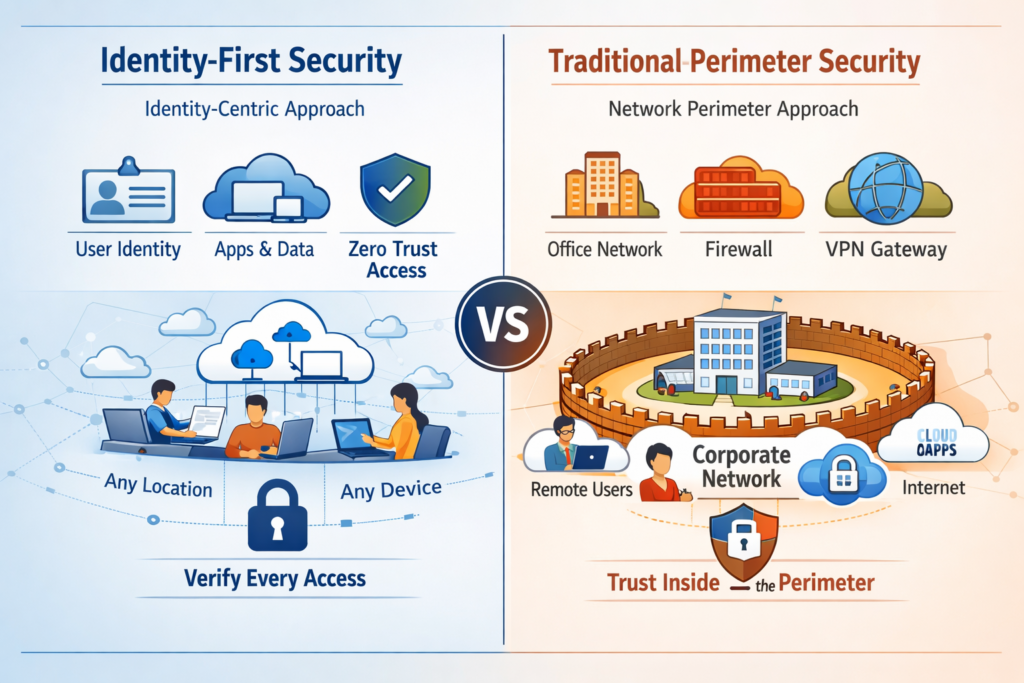
Identity-First Security vs Traditional Perimeter Security
Legacy perimeter models vs identity-first security
Traditional perimeter security assumes a trusted internal network protected by VPNs and firewalls. Once you’re “inside,” there’s a lot of implicit, ambient trust often with flat networks, shared admin accounts and broad access to lateral movement.
At its core, identity-first security vs perimeter security boils down to this:
Perimeter: “Authenticate once at the edge, then move freely.”
Identity-first: “Every request is evaluated based on identity, device, posture and context.”
By issuing per-app, per-session access and enforcing least privilege, identity-first security sharply reduces the blast radius when a credential or endpoint is compromised.
Typical starting point: fragmented IAM, SSO, MFA and on-prem AD
Most enterprises don’t start from a clean slate. The reality in a New York bank, London retailer or Munich manufacturer usually looks like.
Multiple identity providers, plus on-prem Active Directory and legacy LDAP.
VPN concentrators mapped to network segments rather than applications.
Basic MFA for a subset of users, often not enforced on admin accounts.
Adding MFA, SSO or a new ZTNA tool is useful, but it isn’t full identity-first security or Zero Trust. Quick wins include:
Consolidating identities into fewer authoritative IdPs.
Enforcing stronger authentication (MFA everywhere that matters, then moving toward passwordless).
Implementing conditional and step-up policies e.g. stronger factors for privileged actions or access from unmanaged devices.
The roadmap in the final section assumes exactly this starting point and shows how to grow from there.
Regulatory drivers in US, UK and EU
Identity-first security also maps cleanly to regulatory expectations.
US
In healthcare, HIPAA and emerging HHS cybersecurity guidance emphasise risk-based access control, audit trails and rapid incident response. Zero Trust, identity-aware logging and least privilege help US hospitals keep critical patient services online while satisfying HIPAA safeguards.
UK
For UK organisations, especially financial services operating under FCA-aligned controls and Open Banking, the UK’s National Cyber Security Centre (NCSC) explicitly recommends Zero Trust principles like “never trust, always verify” and continuous authentication.
Germany/EU
GDPR and the NIS2 Directive require strong technical and organisational controls, clear accountability and rapid incident reporting for critical infrastructure and digital service providers. Identity-first access controls and detailed access logs help demonstrate compliance for German manufacturers, BaFin-regulated banks in Frankfurt and EU-wide operators.
For boards in heavily regulated sectors, an identity-first Zero Trust story often lands better than a vague “we bought another firewall” narrative.
Zero Trust Architecture Built on Identity
Key building blocks of a Zero Trust architecture in 2026
A Zero Trust architecture in 2026 treats every network, user, device and workload as untrusted by default. Identity, device, network, application, data and workloads become pillars under a unified policy engine that continuously evaluates risk.
Core building blocks (AEO micro-answer)
Identity
Strong, centralised identities for humans, machines and AI agents.
Device & network
Device posture, micro-segmentation and encrypted connections.
Apps & data
Per-app access, least privilege and fine-grained authorisation.
Workloads & automation
Policy-based, API-driven access for cloud, containers and non-human identities.
The mantra “never trust, always verify” is enforced on every request, not just at login.
Identity security controls that enforce Zero Trust
Identity-first security becomes the enforcement layer for Zero Trust via.
IAM/IGA & SSO/MFA
Central identity lifecycle and strong authentication.
ZTNA instead of VPN
Per-application access, often using device posture and user risk, rather than giving users a broad network tunnel.
Identity threat detection and response (ITDR)
Analytics to spot suspicious identity behaviour impossible travel, MFA fatigue, anomalous service account use.
Context-based policies
Signals from EDR/XDR, SSPM and cloud posture tools feed into adaptive access decisions.
In a hybrid environment spanning AWS, Azure and Google Cloud, plus SaaS like Microsoft 365 and Salesforce, continuous authentication and authorization turn identity into a programmable security fabric rather than a static directory.

Zero Trust for hybrid cloud and SaaS in US, UK and EU
Hybrid cloud Zero Trust in 2026 means assuming workloads may be compromised and designing for workload identity, micro-segmentation and just-in-time access. For non-human identities, platforms like Aembit advocate “identity over network” so applications and services authenticate to each other using strong identities, not shared secrets baked into configs.
Consider a London-based bank with data centres in Frankfurt and workloads across AWS and Azure:
Regulators and internal policy require data residency in the EU, so production databases stay in Frankfurt.
Developers in London and New York access those workloads over ZTNA, using workload identities and just-in-time privileged elevation.
German BaFin and EU NIS2 controls are supported by centralised identity logs, fine-grained entitlements and strong MFA for critical systems.
A similar approach works for US enterprises with strict PCI DSS and HIPAA requirements: keep sensitive data in tightly segmented environments, expose only necessary app endpoints via Zero Trust, and tie every access path back to identity-aware policies.
Cyber Resilience in an Identity-First, Zero Trust World
Cyber resilience strategy vs backup, DR and business continuity
A cyber resilience strategy in 2026 is about the ability to absorb, adapt and safely continue operating during attacks, not just restore from backups later. Cyber resilience vs business continuity is the difference between “we never went offline” and “we were down for days but eventually restored from tape.”
Backups, DR and BCP matter but on their own, they assume you can afford to be offline. Identity-first Zero Trust adds:
Reduced blast radius via least privilege and micro-segmentation.
Faster containment through identity-aware kill switches and policy changes.
Immutable backups and rapid recovery designed into normal operations.
Why cyber resilience matters in the era of AI-driven attacks
AI-powered cyber attacks have changed the tempo: adversaries use generative AI to craft phishing at scale, test credentials and move laterally faster than humans can respond. Recent research shows a growing share of breaches now involve “shadow AI” tools and generative AI–enhanced phishing, with a subset of organisations reporting 20%+ of incidents tied to poorly governed AI usage.
Identity-first security plus Zero Trust improves ransomware resilience by.
Limiting which identities can reach crown-jewel systems in the first place.
Detecting suspicious identity behaviour (mass file encryption, privilege escalation)
Enforcing break-glass procedures and privileged access workflows during incidents.
Sector snapshots: US healthcare, UK public sector, German manufacturing
US healthcare (HIPAA)
Hospitals rely on identity-first Zero Trust to keep EHR, PACS and critical clinical systems available while isolating infected segments and tightly controlling vendor remote access. HHS cybersecurity guidance increasingly points to identity-aware logging, multi-factor authentication and rapid incident response as table stakes.
UK public sector & NHS ecosystem
Guidance from the National Cyber Security Centre and departmental security teams encourages Zero Trust for mixed estates, helping NHS trusts maintain patient services even when legacy systems and modern cloud platforms must coexist.
Germany/EU manufacturing and energy
German manufacturers embracing Industrie 4.0 and DACH energy providers refine OT/IT segmentation and build NIS2-compliant identity controls for remote maintenance, SCADA access and supplier integrations, supervised by regulators like BaFin for financial services. (
For CISOs in sectors like healthcare, public sector and manufacturing, identity-first cyber resilience is increasingly a board-level requirement, not a “nice to have.”
Cybersecurity Trends 2026: AI, Identity & Zero Trust
AI-powered attacks, shadow AI and identity abuse
Cybersecurity trends 2026 are identity-centric.
AI helps defenders detect anomalies faster, but it also accelerates credential stuffing, phishing and deepfake-based social engineering. Studies linked to IBM’s Cost of a Data Breach report show that shadow AI and poorly governed AI tools are already implicated in a meaningful fraction of breaches, adding hundreds of thousands of dollars to average breach costs.
Shadow AI also spawns new machine and API identities that are.
Often created outside security review.
Poorly tracked in existing IAM and IGA tools.
Over-privileged by default.
Identity-first security answers with continuous identity risk scoring, ITDR and strong governance of AI workloads and agentic systems.
Post-quantum, NIS2 and EU digital sovereignty
Post-quantum cryptography, NIS2 and EU digital sovereignty are converging around a need for transparent, risk-based access controls:
Post-quantum cryptography
CISOs are inventorying cryptographic dependencies and planning for algorithm transitions, often in lockstep with identity infrastructures (PKI, certificates, tokens). (Mak it Solutions)
NIS2-compliant Zero Trust architecture in the EU
ENISA’s NIS2 technical guidance emphasises strong access management, continuous monitoring and incident reporting for essential and important entities. (ENISA)
EU digital sovereignty & data residency
EU regulators expect clarity on where identities and data live. Identity-first controls with detailed logs support accountability under GDPR and sector rules.
Identity-first access logging who accessed what, when, from where, under which policy becomes a primary evidence source for auditors.
Future of identity security in the AI era
The future of identity security in the AI era is already visible.
Passwordless and phishing-resistant authentication.
Continuous, adaptive authentication based on behaviour and risk.
ITDR that fuses identity analytics, UEBA and threat intel.
Hybrid cloud security posture management spanning human, machine and AI identities.
For CISOs, a few “no-regret moves” stand out:
Standardise on a small number of authoritative identity platforms (for people and workloads).
Enforce phishing-resistant MFA and start pilots for passwordless flows.
Deploy ITDR and integrate identity telemetry into your SOC.
Map out non-human identities (APIs, workloads, bots) and bring them under policy.
Align your identity-first security and Zero Trust programme explicitly with NIS2, GDPR/UK-GDPR, HIPAA and PCI DSS expectations.
Designing Your Identity-First Zero Trust Roadmap
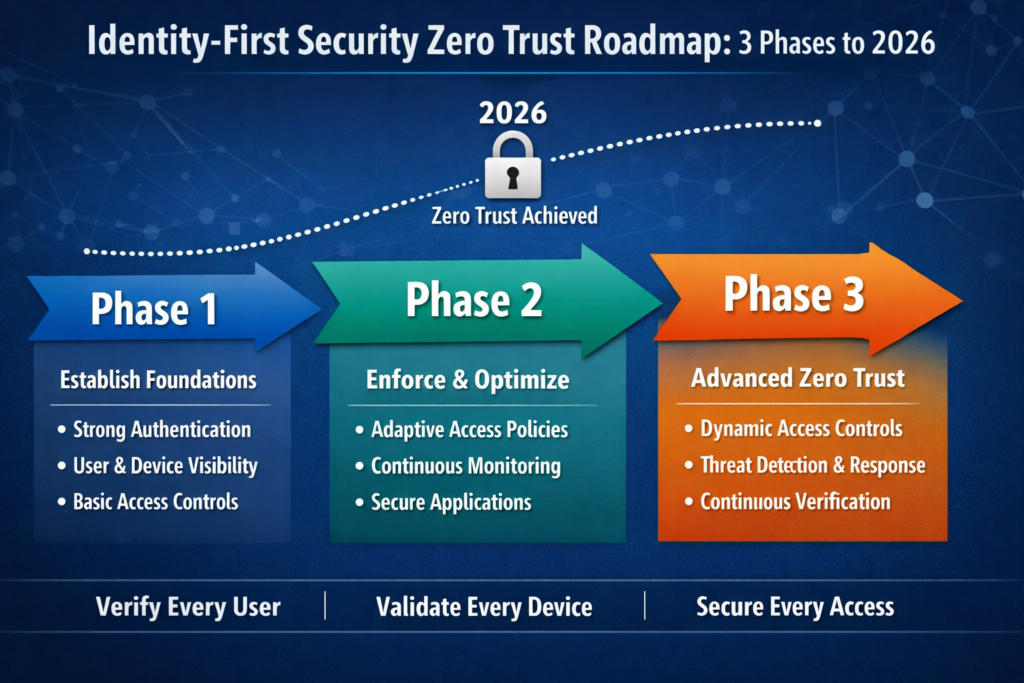
A 3-phase identity-first security roadmap for 2026
Organisations can design an identity-first security Zero Trust roadmap for 2026 that meets US, UK and EU regulations by following a phased approach aligned to their current estate and regulatory obligations, then mapping controls to frameworks like GDPR/UK-GDPR, NIS2, HIPAA and PCI DSS. Start by inventorying identities and access paths, then modernise identity and access controls, and finally extend Zero Trust and cyber resilience across hybrid cloud and OT.
A simple three-phase roadmap.
Phase 1 (0–3 months): Discovery & assessment
Inventory human, machine and AI identities; map crown-jewel systems and access paths.
Review IAM, SSO, VPN, ZTNA and directory services (including on-prem AD).
Baseline compliance posture for GDPR/UK-GDPR, NIS2, HIPAA, PCI DSS and SOC 2.
Phase 2 (3–9 months): Modernise identity
Consolidate IdPs where practical; rationalise groups and roles.
Roll out strong authentication (MFA, then passwordless pilots) and context-based access policies.
Pilot Zero Trust for priority use cases (e.g. remote admin access, third-party access to SaaS).
Phase 3 (9–18 months): Scale Zero Trust and cyber resilience
Extend identity-first Zero Trust to hybrid cloud, SaaS, OT/IoT where relevant.
Integrate ITDR, XDR, SSPM and cloud posture tools into a single identity-centric view.
Formalise cyber resilience scenarios, including ransomware and AI-driven identity abuse.
US enterprises can explicitly align this roadmap with NIST and HHS guidance, while German organisations can show how identity-first security and Zero Trust support DSGVO and NIS2 obligations.
Building a cyber resilience operating model and metrics
Cyber resilience isn’t a project it’s an operating model. That model should clarify.
Roles
CISO, CIO, head of infrastructure, risk, compliance, product teams and regional leads (e.g. US, UK, DACH).
Rhythms
Quarterly tabletop exercises, purple teaming, identity-centric incident simulations, and regular reviews of privileged access.
Useful metrics include:
Mean time to detect/respond (MTTD/MTTR) identity-driven incidents.
Reduction in privileged accounts and standing admin access.
Number of critical services able to operate during exercises (vs failing over to DR)
Ransomware recovery time and data integrity measures.
These metrics give boards from New York to London to Berlin a language to judge whether identity-first cyber resilience is improving.
Selecting platforms and partners across US, UK and EU
When selecting platforms and partners, look for.
Identity-first design
Native support for humans, machines and AI agents.
Zero Trust architecture support
Per-app access, continuous evaluation, micro-segmentation hooks.
ITDR capabilities
Behavioural analytics, integration with existing SIEM/SOC.
Data residency & certifications
Options for EU-only data processing, plus SOC 2, ISO 27001, PCI DSS alignment and HIPAA readiness where relevant. (PCI Security Standards Council)
Delivery partners in hubs like London, New York, Frankfurt and Berlin can help with local regulatory nuance and sector specifics. Rather than jumping straight into a product RFP, many CISOs start with an identity-first security and Zero Trust workshop or a maturity assessment to build consensus on priorities.
Key Takeaways
Identity-first security treats identity as the control plane for Zero Trust, replacing ambient, network-based trust with continuous authentication and authorization.
Consolidating IAM, enforcing strong MFA/passwordless, and deploying ITDR are high-impact, low-regret moves for US, UK, German and wider EU enterprises.
Cyber resilience goes beyond backup and DR; it combines identity-first Zero Trust, immutable backups and tested incident playbooks so core services keep running.
AI, shadow AI and exploding machine identities make identity-centric controls and continuous identity risk scoring essential in 2026.
A three-phase roadmap discover, modernise, scale helps organisations align identity-first Zero Trust with GDPR/UK-GDPR, NIS2, HIPAA, PCI DSS and SOC 2.
Choosing vendors and partners with strong identity, Zero Trust and regional compliance capabilities is as important as any single technology feature.
Concluding Remarks
Identity-first security isn’t a buzzword it’s how Zero Trust and cyber resilience actually get implemented in real networks, with real users and real regulators watching. For CISOs and architects across the US, UK, Germany and the wider EU, the challenge is less about picking a magic platform and more about designing an identity-centric operating model that can adapt as AI, regulation and business models evolve.
If your organisation is still anchored on VPNs and implicit trust, now is the moment to move identity to the centre of your architecture, start shrinking the blast radius and turn Zero Trust from a slideware slogan into day-to-day practice.
If you want help turning this playbook into a concrete roadmap for your organisation, you don’t have to do it alone. The team at Mak It Solutions already works with cloud, AI and analytics leaders across the US, UK, Germany and the wider EU on Zero Trust, data and application architectures.
Share your current landscape, regulatory pressures and key systems, and request an identity-first security and Zero Trust workshop. Together, you can map a phased roadmap that’s realistic for your estate and aligned with your board’s risk appetite and compliance obligations.( Click Here’s )
FAQs
Q : How does identity-first security reduce lateral movement during a breach?
A : Identity-first security reduces lateral movement by removing the idea of a “trusted internal network” and evaluating each access request individually. Instead of giving a compromised VPN account broad network access, Zero Trust and ZTNA limit access to specific applications and services with least privilege access control. Continuous authentication and authorization plus ITDR mean that unusual behaviour like mass file access or privilege escalation—can be detected and blocked quickly, shrinking the blast radius of any one compromised identity.
Q : What role does device posture play in an identity-first Zero Trust model?
A : Device posture provides context about whether an endpoint or workload is safe enough to trust, even when the user or service has valid credentials. In an identity-first Zero Trust model, access policies often require managed devices, recent patches, running EDR and encrypted storage before granting access to sensitive applications or data. If posture degrades say, EDR is disabled or the OS is outdated the system can deny access or require step-up authentication. This ties device health directly to identity and least privilege decisions.
Q : Can small and mid-sized enterprises adopt identity-first security without ripping and replacing existing tools?
A : Yes. Small and mid-sized enterprises can phase in identity-first security by consolidating a few key identity systems, enforcing stronger MFA and adding ZTNA for the highest-risk access paths. Many modern IAM, SSO and ZTNA solutions integrate with existing directories like Active Directory and common SaaS platforms, so you don’t need a big-bang replacement. Starting with admin and third-party access, then expanding to broader user groups, lets SMEs improve security and compliance while staying within realistic budget and staffing limits.
Q : How should CISOs budget for identity-first security and Zero Trust initiatives in 2026?
A : CISOs should budget for identity-first security and Zero Trust as a multi-year transformation, not a one-off purchase. Typical categories include consolidating IAM/SSO/MFA platforms, adding ZTNA and ITDR, modernising logging and analytics, and funding process changes like access reviews and tabletop exercises. Many organisations reallocate spend from legacy VPN and perimeter tools to identity-first platforms, and justify investments using breach cost data that shows compromised credentials and identity-centric breaches among the most expensive incident types.
Q : Which metrics best demonstrate that an identity-first cyber resilience strategy is working?
A : Strong identity-first cyber resilience programmes track both security and continuity metrics. On the security side, look at reductions in standing privileged accounts, improved MFA coverage, faster MTTD/MTTR for identity incidents and fewer successful phishing or credential abuse events. On the resilience side, measure how many critical services can operate during simulated attacks, how quickly you can isolate compromised identities or segments, and how long it takes to restore normal operations without paying ransoms. Over time, boards should see improved incident outcomes and lower business disruption.


