MDR vs XDR vs SOC: How Mid-Sized Firms Should Decide
MDR vs XDR vs SOC: How Mid-Sized Firms Should Decide
MDR vs XDR vs SOC: How Mid-Sized Firms Should Decide
MDR (managed detection and response) is a 24/7 outsourced security service where a provider runs monitoring, threat hunting and incident response for you. XDR (extended detection and response) is the unified technology platform your own or a partner SOC team operates. A SOC is the operational team and process layer that runs those tools day and night.
For 200–1000-employee companies, MDR usually fits starter and scaling teams, XDR plus a small SOC suits more mature security functions, and building a full in-house SOC is only realistic for organisations with significant budget, skills and regulatory pressure.
Introduction
For 200–1000-employee companies in the United States, United Kingdom, Germany and wider European Union (EU), the MDR vs XDR vs SOC decision has quietly become a board-level risk question. Ransomware attacks climbed to more than five thousand published incidents in 2024 alone, and average ransom demands now sit in the high six figures for many sectors. At the same time, there is a global cybersecurity workforce gap of roughly 4.8 million professionals, so mid-market firms cannot simply “hire a SOC team” and be done.
This guide treats MDR vs XDR vs SOC (and SOC-as-a-service) as operating models, not just products. By the end, you’ll have a clear view of which model fits your team size, skills, risk tolerance and regulatory context whether you’re a SaaS company in New York, a healthcare IT provider in London or a Mittelstand manufacturer near Berlin.
At a high level: MDR is a managed detection and response service; XDR is an extended detection and response platform; and a SOC is the people and processes that operate these tools to deliver 24/7 threat monitoring for mid-sized companies. Different combinations suit different maturity levels and that’s what we’ll unpack.
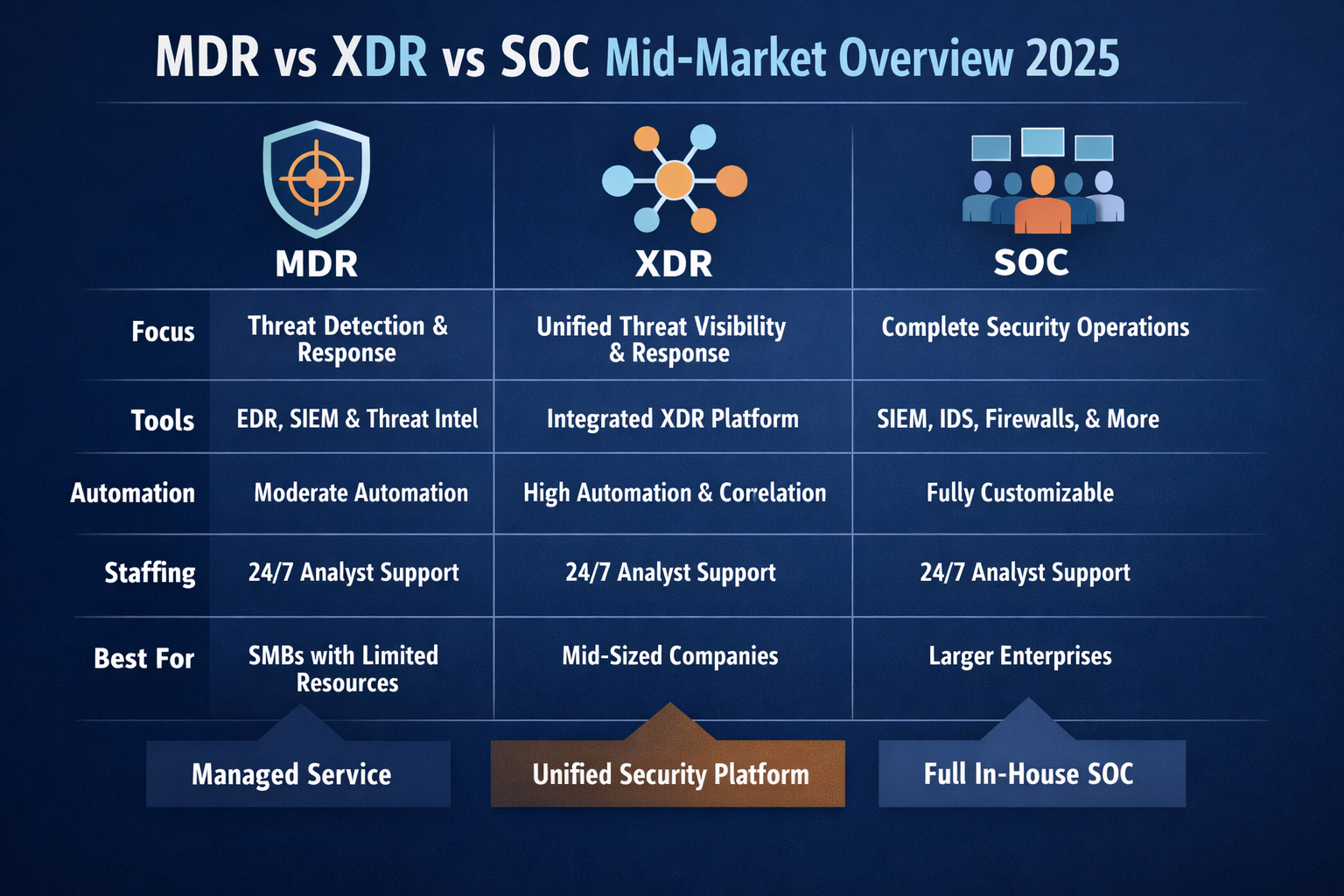
MDR vs XDR vs SOC Key Differences in Plain English
For a 200–1000-employee company, the difference between MDR, XDR and a SOC is mostly about who owns outcomes and who does the work. MDR is an outsourced outcome, XDR is the technology platform, and the SOC is the operational engine that turns all of this into alerts handled and incidents contained.
What MDR Is and How It Works for Mid-Market Organisations
Managed detection and response (MDR) is a 24/7 security operations service where an external team monitors your environment, hunts for threats and guides or executes incident response on your behalf. In plain terms: MDR is “SOC + tools” delivered as a subscription service, tuned for organisations that can’t staff their own round-the-clock security operations center.
Typical mid-market MDR services cover endpoints, networks, identities, email, cloud workloads and key log sources. They may be fully managed (your provider runs everything) or co-managed (your internal analysts work alongside an outsourced SOC and incident response team). Many MDR providers build on leading extended detection and response platforms and EDR tools from vendors like CrowdStrike, Sophos, Check Point Software Technologies or Rapid7, but sell you an outcome not just licences.
AEO micro-answer What is MDR?
For mid-market security teams, MDR is a managed detection and response service where a specialist provider delivers 24/7 monitoring, threat hunting and incident response across your endpoints, network, cloud and identities.
What XDR Platforms Do Beyond Traditional EDR and SIEM
Extended detection and response (XDR) is a technology platform that correlates signals across endpoints, identities, email, network, SaaS and cloud to spot complex attacks faster than legacy EDR or standalone SIEM. Instead of separate consoles and rules for every tool, an XDR platform unifies telemetry, detection logic and automated response actions.
The key distinction: XDR is a platform you (or your partner) operate, whereas MDR is an outcome-based service that usually includes tooling. Many XDR deployments assume you either have, or are building, a SOC whether in-house or via SOC-as-a-service.
AEO micro-answer What is XDR?
For overstretched IT and security teams, XDR is an extended detection and response platform that unifies alerts and telemetry from endpoints, identities, email, network and cloud into a single detection and response engine.
What a SOC (and SOC-as-a-Service) Actually Delivers
A security operations center (SOC) is the combination of people, processes and tools that monitor your environment, triage alerts, investigate suspicious activity and coordinate incident response 24/7. Whether in one room or fully virtual, the SOC owns operational responsibility for “What happens when the alert fires at 3 a.m.?”
In-house SOCs are built and staffed by your organisation. SOC-as-a-service (SOCaaS) delivers the same functions through an external provider, often layered on top of SIEM and/or XDR tools that you own or they host. SOCaaS is typically priced per user, endpoint or log volume and may integrate with your ticketing tools so your internal IT teams stay in the loop.
AEO micro-answer What is a SOC?
A SOC is the operational security team that runs monitoring tools, triages alerts and manages incident response 24/7, whether staffed internally or delivered as SOC-as-a-service by an external provider.
MDR vs XDR vs SOC for 200–1000 Employee Companies
Side-by-Side Comparison Table: MDR vs XDR vs SOC vs SIEM
For a 200–1000-employee company, the practical difference between MDR, XDR and a SOC is how much you outsource, how fast you can go live and how many people you must hire.
AEO micro-answer Core difference for 200–1000 employee companies
For 200–1000-employee organisations, MDR outsources both tooling and 24/7 operations, XDR is mainly a platform your own or a partner SOC must run, and a full in-house SOC with SIEM/XDR gives maximum control but requires the most headcount, budget and time.
| Dimension | MDR (Service) | XDR (Platform) | In-House SOC | SIEM (Tool Only) |
|---|---|---|---|---|
| Ownership of outcomes | Mostly provider | You (or SOC) | You | You |
| Primary “thing” | Managed detection and response services | Extended detection and response platform | Security operations center team | Log management & correlation platform |
| 24/7 coverage | Included in service | Requires staffing or SOCaaS | Requires full rota | Not included |
| Staffing requirement | Small internal liaison team | 2–5+ analysts for mid-market SOC | 6–15+ people for 24/7 cover | Analysts needed to interpret alerts |
| Tooling dependence | Provider stack + your stack | XDR + possible SIEM/SOAR | XDR/EDR + SIEM + SOAR + threat intel | SIEM + separate EDR/other tools |
| Time to value | Weeks | Months | 9–18 months typical | Months |
| Cost profile (3-year) | Predictable subscription | Licences + some headcount | Highest (tools + salaries + overhead) | Tools only, risk of hidden OPEX |
Including SIEM here picks up “MDR vs XDR vs SIEM” intent: SIEM is a log analytics and alerting engine, not a full operating model. It becomes powerful once wired into MDR or your SOC.
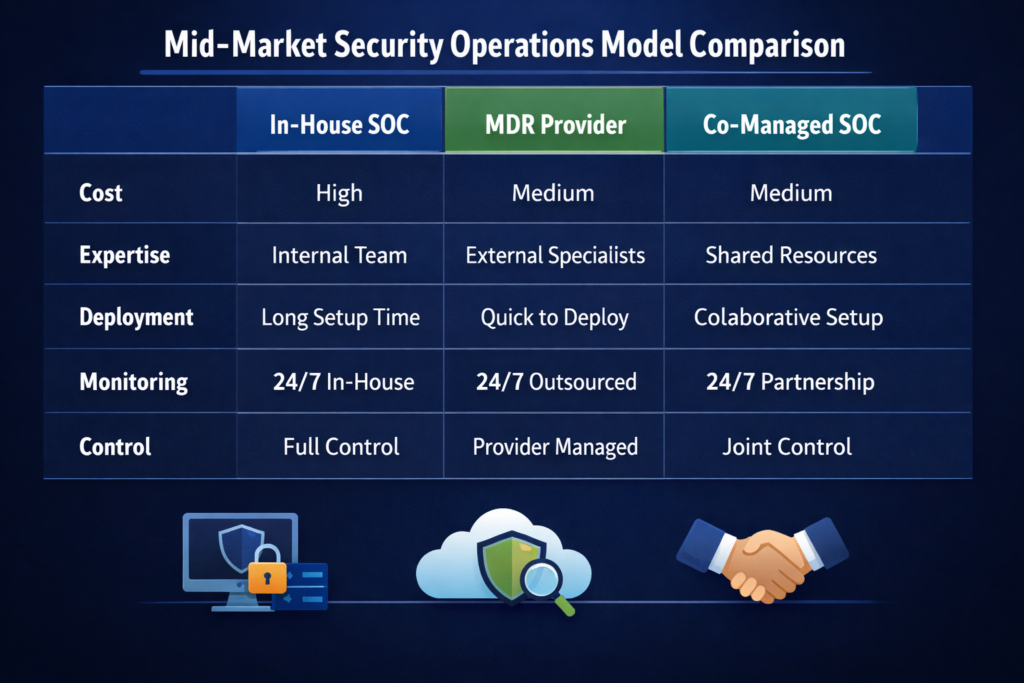
Strengths and Limitations of Each Model for Mid-Market Environments
For 200–1000-employee firms.
MDR
Strengths: Fast time-to-value, 24/7 coverage, access to senior threat hunters, predictable cost, and clear SLAs for detection and response.
Limitations: Less direct control over tooling choices, potential data residency questions, and some vendor lock-in (especially if using a single provider’s platform end-to-end)
XDR (without MDR)
Strengths: Deep visibility and automation, powerful correlation across attack surfaces, and flexibility to build your own SOC operating model.
Limitations: Still requires skilled analysts, runbooks and on-call coverage. Without a strong SOC, XDR can become an expensive “single pane of alert fatigue”.
SOC / SOCaaS
Strengths: Custom playbooks, integrations with your ticketing and DevOps stack, tailored reporting for regulators like BaFin or the European Central Bank (ECB), and strong internal ownership.
Limitations: High hiring and retention costs across time zones, plus continuous investment in SIEM, XDR, SOAR and threat-intel integrations.
Choosing by Security Maturity.
A useful way to think about MDR vs XDR vs SOC is by security maturity.
Starter (1–2 IT generalists, no SOC)
Often a 200–300-person SaaS or manufacturing firm in Dublin or Austin.
Best fit: MDR or SOC-as-a-service, because you need 24/7 threat monitoring for mid-sized companies without hiring a full SOC.
Scaling (small security team, some tools)
Maybe a 500-person fintech in Frankfurt with EDR, some SIEM, and a security lead.
Best fit: MDR on top of your existing stack, or a hybrid model where XDR plus outsourced SOC handles off-hours.
Mature (established SOC, strong processes)
Often a 1000-person financial or healthcare firm in New York or London with a CISO, SOC manager and multiple analysts.
Best fit: XDR plus internal SOC, sometimes with specialist MDR for high-risk workloads or incident response retainers.
Searchers typing “MDR vs XDR”, “MDR vs SOC” or “SOC vs MDR vs XDR” are usually somewhere along this maturity path; the closer you are to “starter”, the more likely MDR will be the right default.
MDR vs XDR for Mid-Sized Businesses in the US, UK and EU
Typical Mid-Market Constraints.
Mid-market companies in New York, London and Berlin tend to share three realities.
Small internal teams
Often just a handful of IT/security staff juggling infrastructure, cloud and compliance.
No night shift
True 24/7 coverage requires at least 8–10 people on a rota; most mid-market firms simply don’t have that.
Skills shortages and salary pressure
Competing with global banks and hyperscalers for experienced SOC analysts is hard, especially in high-cost cities.
This is why many mid-market teams now prefer managed detection and response services and security operations center as a service models: they want managed outcomes, not more dashboards.
When MDR Is the Better Fit for Mid-Market Organisations
MDR is usually the better starting point when you:
Have 200–1000 staff, minimal SOC capability and a mix of on-prem, cloud and SaaS systems.
Need immediate 24/7 coverage to satisfy customer audits, board questions or regulators.
Operate in regulated sectors like US healthcare under HIPAA, UK SMEs supplying the NHS, or German Mittelstand manufacturers subject to NIS2 and GDPR/DSGVO.
AEO micro-answer MDR vs XDR for mid-sized business
For most mid-sized businesses in the US, UK and EU, MDR is the safer default because it combines a mature technology stack with a 24/7 outsourced SOC and incident response team, whereas XDR alone still expects you to staff and run your own operations.
When XDR Plus a Small Internal SOC Makes Sense
XDR plus a small internal SOC becomes attractive when you already have.
A dedicated security team with at least 3–5 analysts.
On-call processes, incident runbooks and a clear incident commander role.
Existing SIEM, ticketing and ITSM tools that you want tightly integrated.
Why might a mature mid-market security team prefer XDR plus an internal SOC over fully managed MDR?
Because they want deeper customisation, closer integration with internal processes and the ability to tune detections and playbooks themselves often important for highly regulated financial services or critical infrastructure. MDR may still complement this setup for specific workloads (e.g. cloud or OT environments) or as a backup incident response service.
Build vs Buy SOC, MDR and SOC-as-a-Service
The True Cost and Complexity of Building an In-House SOC
A 24/7 in-house SOC is rarely “just hire a few analysts”. Typical roles include:
SOC manager
Tier 1–3 analysts (at least 6–8 to cover shifts)
A security engineer for tooling and integrations
Salary expectations for these roles in the United States, United Kingdom and Germany, especially in cities like New York, London and Berlin, push total annual staffing into the high six or low seven figures before tooling. On top of that you need SIEM, XDR/EDR, SOAR, ticketing, threat intelligence and continuous integration work.
Outsourced SOC vs MDR vs XDR with Internal SOC
In practice, mid-market firms tend to land in one of three operating models.
Outsourced SOC / SOCaaS
You own SIEM/XDR; the provider runs monitoring, triage and first-line response.
MDR
Provider brings both stack and people; you focus on business context, approvals and remediation.
XDR with internal SOC
You own platform, people and process; maybe use specialist providers for red teaming or incident response.
These map directly to queries like “SOC as a service vs MDR”, “24/7 SOC vs MDR outsourcing” and “XDR with internal SOC vs fully managed MDR”.
Decision Triggers.
Common triggers that tell a mid-sized business it’s time to move from tool-only (EDR, SIEM, XDR) to MDR or SOCaaS include.
Persistent alert fatigue and untriaged incidents.
Board or regulator questions you can’t answer quickly.
New obligations under NIS2, UK-GDPR or sector rules like Open Banking.
AEO micro-answer Why many mid-sized businesses choose MDR instead of building a 24/7 SOC
Many mid-sized businesses in the US and Europe choose MDR instead of building their own 24/7 SOC because MDR sidesteps the global skills shortage, cuts the time to achieve continuous monitoring from years to weeks, and converts unpredictable hiring and tooling costs into a predictable subscription aligned with compliance expectations.
Compliance, Data Residency and Regional Requirements
How MDR and XDR Support GDPR, UK-GDPR and NIS2
GDPR/DSGVO, UK-GDPR and the NIS2 Directive all expect you to detect, investigate and report incidents in a timely, documented way, with adequate technical and organisational measures. MDR and XDR help by centralising logs, detections and incident history so you can evidence controls and timelines to auditors.
For EU organisations or US/UK businesses serving EU customers data residency matters. Many choose XDR and SIEM deployments in EU regions of Amazon Web Services (AWS), Microsoft Azure or Google Cloud, and then require their MDR or SOCaaS provider to keep telemetry and analyst access inside the European Economic Area.
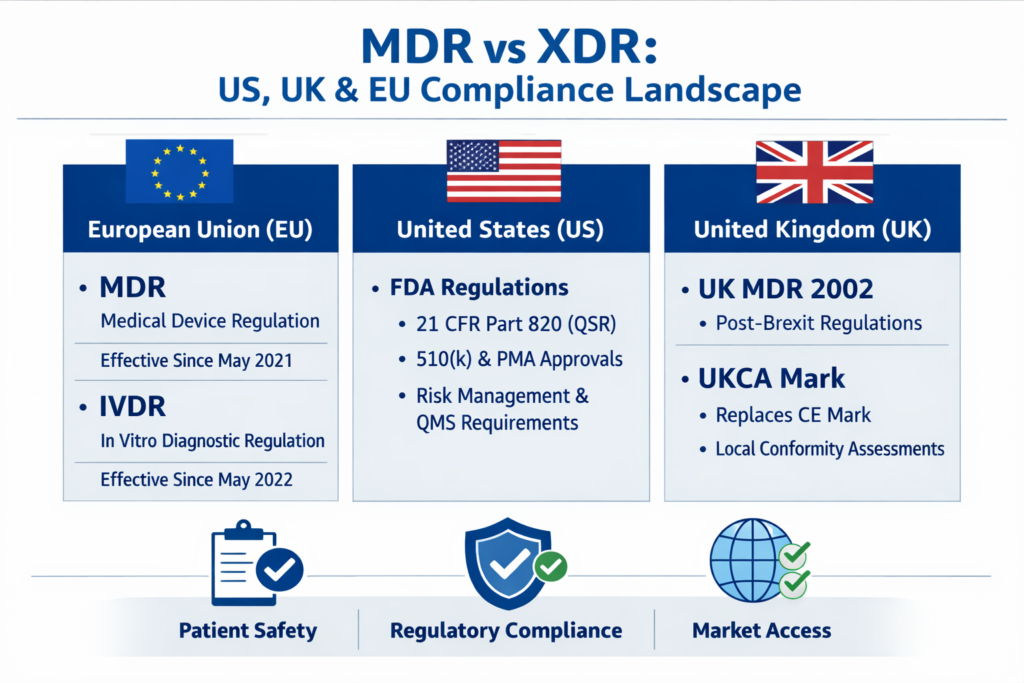
Sector-Specific Needs: HIPAA, PCI DSS, SOC 2 and Financial Regulators
US healthcare (HIPAA)
MDR and XDR must support log retention, access monitoring and incident response aligned with the HIPAA Security Rule’s safeguard requirements.
PCI DSS
Payment environments need strict logging, file-integrity monitoring and network segmentation; XDR/SIEM plus MDR can provide continuous monitoring and evidence for assessments.
SOC 2 & financial regulators
UK/EU cloud-first firms and European financial institutions supervised by BaFin and the ECB often require vendors to hold SOC 2 reports and demonstrate specific controls for monitoring, access, encryption and incident response.
UK NHS, Open Banking and German Mittelstand Examples
Concrete examples help.
A London-based NHS supplier might use MDR on top of XDR to prove continuous monitoring and incident response coverage for NHS Data Security and Protection Toolkit reviews.
An Open Banking fintech in London or Frankfurt may prefer XDR plus a small internal SOC, with additional MDR or SOCaaS coverage for critical APIs regulated by the FCA or BaFin.
A German Mittelstand manufacturer subject to NIS2 and sector safety rules might choose MDR with an EU-based SOC and strict data residency as a pragmatic compromise between resilience and cost.
Note
This article is for general information only and is not legal, financial or compliance advice. Always consult qualified advisors for regulatory decisions.
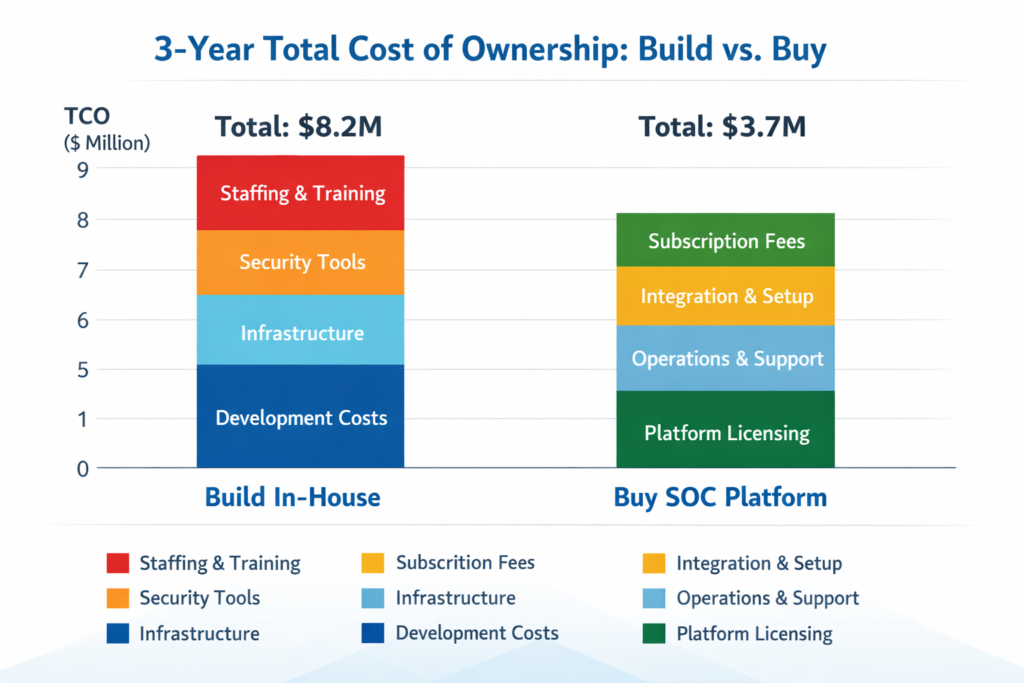
Three-Year TCO: MDR vs XDR vs Building a SOC
Cost Components to Include in a 3-Year Model
When comparing MDR vs XDR vs SOC over three years, include
Platform licences and subscriptions (EDR/XDR, SIEM, SOAR)
MDR or SOCaaS service fees
Cloud/SIEM storage and egress
Staffing (salaries, benefits, on-call)
Training, certifications and turnover
Integration and maintenance effort
MDR shifts more of these into a single external line item; XDR and in-house SOC keep more cost in-house.
Example 3-Year TCO Scenarios for 200, 500 and 1000 Staff
Numbers will vary by sector and region, but directional patterns for US/UK/EU mid-market firms look like this (licences and services only, excluding major breach costs):
200 staff
MDR: typically cheaper than hiring even 2–3 full-time analysts.
XDR + ad-hoc monitoring: lower subscription cost, higher risk of missed incidents.
500 staff
MDR or SOCaaS: mid six-figure spend over 3 years, but with full 24/7 coverage.
XDR + small SOC: similar total cost if you already planned to grow the team.
1000 staff
MDR: still competitive, particularly for multi-region operations.
Full SOC build: can climb into the low millions over 3 years once you include tooling, salaries, and turnover backfill.
AEO micro-answer How to compare 3-year TCO
A mid-market company should compare three-year TCO for MDR vs XDR vs building a SOC by modelling all internal and external costs (licences, cloud, SOC headcount, training and integrations) and then overlaying risk reduction for example, how each option affects mean time to detect, mean time to respond and breach cost exposure.
Beyond Cost.
Cost is only half the story. MDR vs XDR vs SOC also affects.
Dwell time and blast radius Faster detection and response often matter more than minor licence savings.
Assurance Can you show auditors, customers and regulators that alerts are triaged 24/7 with documented actions?
Board reporting MDR and mature SOCs should help you report on incident trends, control effectiveness and regulatory alignment.
Before deciding, CIOs and CISOs should ask.
If a critical alert fires at 2 a.m., who sees it, who triages it and how quickly?
Can we realistically hire and retain enough analysts to run an in-house SOC for the next three years?
Which option best supports our compliance obligations (GDPR/DSGVO, NIS2, HIPAA, PCI DSS, SOC 2, Open Banking)?
How will this decision look if we suffer a major incident in the next 18 months?
How to Choose A Simple Decision Framework for MDR vs XDR vs SOC
Quick Self-Assessment Checklist for CIOs and CISOs
Answer these yes/no questions:
Do we have at least 3 dedicated security analysts today?
Can we fund and staff true 24/7 coverage without burning out the team?
Are our SIEM/XDR tools already integrated with ticketing, identity and cloud?
Do we operate in highly regulated sectors (banking, healthcare, critical infrastructure)?
Do customers and auditors already expect detailed SOC and incident response evidence?
Are we comfortable writing and maintaining our own detection rules and playbooks?
Is our primary region US/UK/EU with strict data residency and local-language needs?
Roughly
Mostly no → MDR or SOC-as-a-service
Mixed → MDR plus your existing tools, or SOCaaS on top of XDR
Mostly yes → XDR + internal SOC, optionally with MDR for specific use cases
Place image: ciso-decision-framework-mdr-xdr-soc-checklist.png
Decision Matrix by Maturity, Region and Sector
Starter, US/UK/EU SaaS or manufacturing MDR with regional SOC and clear SLAs.
Scaling, European fintech or payments XDR + MDR or SOCaaS, with strong PCI DSS and Open Banking reporting.
Mature, regulated bank or insurer XDR + internal SOC, hybrid with MDR for cloud or branch networks, strict data residency in EU or UK regions.
Next Steps and How to Engage a Shortlist of Providers
Practical next actions for mid-market teams:
Inventory your current tools, log sources and cloud regions.
Define minimum SLAs for detection, triage and incident response.
Shortlist MDR, SOCaaS and XDR vendors with experience in your region and sector.
Ask for three-year TCO models, data residency options and compliance mappings (GDPR/DSGVO, NIS2, HIPAA, PCI DSS, SOC 2).
Run a 60–90-day pilot with clearly defined success criteria.
If you want help, Mak It Solutions can plug MDR/XDR choices into your wider cloud, data and AI roadmap, drawing on related work in GCC cybersecurity, IAM and AI governance.
If you’re wrestling with MDR vs XDR vs SOC for a 200–1000-employee organisation, you don’t need another vendor pitch you need a clear, numbers-backed operating model. Our Editorial Analytics Team at Mak It Solutions works with engineering, security and compliance leaders to map real-world threats, budgets and regulations to the right combination of MDR, SOCaaS and XDR.
Book a short MDR/XDR readiness and TCO review, and we’ll help you benchmark your current setup, model three-year options and design a realistic roadmap that fits your region, sector and security maturity.( Click Here’s )
FAQs
Q : Do I still need a SOC if I invest in a managed MDR service?
A : In most mid-market environments, MDR gives you SOC-like capabilities without building a full internal SOC team. You still need owners for policies, approvals and remediation actions, but the MDR provider handles 24/7 monitoring, triage, threat hunting and much of the incident workflow. Some larger firms layer a small internal SOC on top of MDR to own playbooks, stakeholder communication and integration with internal IT and DevOps teams.
Q : Is MDR or XDR better if we already have a SIEM and some in-house analysts?
A : If you already own SIEM/XDR licences and have a handful of analysts, the choice depends on your coverage gap. If you struggle with night and weekend coverage, MDR or SOC-as-a-service on top of your existing tools can be the fastest win. If your analysts have bandwidth and you want more control, investing in XDR plus improved processes and automation may deliver better long-term value, with MDR retained as an escalation or specialist incident response option.
Q : How does MDR pricing typically scale for a 200 vs 1000 employee organisation?
A : MDR pricing is usually tied to protected endpoints, users, data volume or a mix of all three. For a 200-person company, MDR often costs less than hiring two full-time SOC analysts once you factor in benefits and tooling; for a 1000-person organisation, total MDR spend can reach the mid six figures over three years but still undercut the fully loaded cost of a 24/7 in-house SOC. Always compare bundled MDR pricing against the combined cost of licences, storage, staffing and on-call.
Q : What SLAs and response times should mid-market companies demand from MDR or SOC-as-a-service providers?
A : Look for clearly defined SLAs across detection, triage and response. Common targets include: initial triage of high-severity alerts within 15 minutes, incident engagement within 30–60 minutes, and defined escalation paths for containment actions. For regulated sectors, insist on documented runbooks, regular reporting, and evidence that the provider can support regulator notifications (e.g. GDPR/DSGVO breach reporting timelines or financial regulator expectations) as part of their standard service.
Q : How quickly can a US, UK or EU mid-sized business realistically go live with MDR compared to building its own SOC?
A : Many mid-sized organisations in the US, UK and EU can onboard MDR in 4–12 weeks, depending on the number of log sources, cloud platforms and identity systems involved. Building an in-house SOC with hiring, tooling, integrations and playbooks often takes 9–18 months to reach comparable maturity, especially given the global cybersecurity skills shortage. MDR is therefore a common choice for firms that need 24/7 coverage and compliance evidence this year, not in two budget cycles.



