Zero Trust Security in 2025: Simple, Practical Guide
Zero Trust Security in 2025: Simple, Practical Guide

Zero Trust Security Explained for 2025 Decision-Makers
Zero trust security is a “never trust, always verify” security model where no user, device or connection is trusted by default, whether it sits inside or outside your network. Access is granted just in time and with least privilege, based on identity, device health and context (such as location and behaviour). That approach helps contain breaches and limit lateral movement across cloud, SaaS and on-prem systems in 2025, even when attackers compromise a single account, VPN or endpoint.
Introduction.
In 2025, zero trust security has become the default design principle for organisations in the US, UK and EU facing AI-assisted phishing, ransomware and supply-chain attacks. Global cybercrime losses climbed into the tens of billions of dollars in 2024, with ransomware alone driving multi-million-dollar incidents for mid-sized businesses.
Classic “castle and moat” security big firewalls, a VPN and implicit trust once you’re inside simply doesn’t match remote work, SaaS sprawl and multi-cloud estates from New York to London and Berlin. Zero trust security, formalised by NIST in SP 800-207, shifts the focus from network location to identity, device posture and granular access to specific resources.
This guide gives decision-makers a plain-English view of what zero trust is, how the model works, how regulations like NIS2, GDPR, UK-GDPR, HIPAA and SEC rules change the stakes, and how to start with low-risk pilots instead of a risky “rip and replace”.
What Is Zero Trust Security in Simple Terms?
Zero trust security is a “never trust, always verify” model that treats every user, device and connection as untrusted by default, whether inside or outside the network. Access is granted just in time and with least-privilege policies, using strong identity, device health checks and context such as location and behaviour. This limits how far an attacker can move if they compromise a single account, VPN or endpoint, which is critical for cloud and remote work in 2025.
Zero Trust Security in One Paragraph
In practice, zero trust means your developer in London or Berlin logging into a CRM or code repo from a laptop doesn’t automatically get full network access. Instead, they authenticate through an identity provider (like Okta or Entra ID), pass MFA, and their device is checked for encryption, patches and EDR health. If everything looks good, they get tightly scoped access only to the specific SaaS app or API they need not the whole subnet. If they suddenly connect from an unusual location or start exfiltrating data, policies can trigger step-up authentication or block the session entirely. That’s very different from the old “VPN into the castle and you’re trusted everywhere” mindset.
“Never Trust, Always Verify”: The Mindset Shift
Traditional security models often treat login as a one-time gate: pass MFA at 9am and you’re effectively trusted until logout. Zero trust replaces this with continuous verification. Every important action accessing a production database in Frankfurt, downloading records from an NHS system in Manchester, or pushing code from Austin is evaluated against identity, device, behaviour and context.
Core ideas include.
Strong identity: phishing-resistant MFA, conditional access and robust identity governance.
Device checks: only healthy, managed devices reach sensitive apps.
Behaviour monitoring: baselines for “normal” user and service behaviour, with alerts when something looks off.
Context-aware policies: rules that adapt to location, time, sensitivity of the resource and current risk score.
Zero Trust vs Traditional Perimeter Security at a Glance
Traditional perimeter security assumes everything inside the network is implicitly trusted once it’s in; zero trust assumes nothing is automatically trusted anywhere, on any network. This drastically limits lateral movement if an attacker compromises a single VPN account, laptop or service account.
Perimeter vs Zero Trust (simplified)
| Aspect | Traditional VPN / Firewall | Zero Trust / ZTNA & Segmentation |
|---|---|---|
| Trust model | Trust inside, verify at perimeter | Never trust, always verify everywhere |
| Access scope | Network-level (subnets) | App/API-level, identity-centric |
| Remote work | Full tunnel VPN into internal LAN | ZTNA to specific apps from any location |
| Lateral movement | Often easy once inside | Microsegmentation / zero trust segmentation (ZTS) |
| Environments | Single data centre | Hybrid + multi-cloud + SaaS (New York, London, Berlin) |
For hybrid and multi-cloud estates across AWS, Azure and Google Cloud regions in Dublin, Frankfurt or Amsterdam, zero trust security aligns far better with how services are actually deployed.

Zero Trust Principles and How the Model Works
Core Principles of Zero Trust in 2025
Core zero trust principles include verifying explicitly (strong identity and device checks), enforcing least-privilege access, assuming breach and designing for containment, and continuously monitoring live sessions.
Verify explicitly
Don’t rely on network location; require MFA, device posture and, for admins in Washington D.C. or Brussels, hardware-backed keys where possible.
Least privilege
Grant just enough access for the task for example, read-only access to a database in Frankfurt for a support engineer, not full admin. This maps well to HIPAA, PCI DSS, SOC 2 and ISO 27001 expectations.
Assume breach
Segment critical workloads (payments, patient data, OT systems) so an intrusion can’t freely traverse from a compromised SaaS account to production.
Continuous monitoring
Use logs and analytics to flag anomalies and feed SOC/SIEM/SOAR platforms.
These principles align closely with NIST SP 800-207 and vendor models from Microsoft, IBM and others.
How a Zero Trust Architecture Works Across Identity, Devices, Networks and Data
In a typical zero trust architecture, users authenticate strongly, devices are checked for health, policy engines make decisions, enforcement points apply them, and traffic is logged continuously. If risk rises — say an engineer in Dublin suddenly connects from an unusual country access can be limited or re-authenticated in real time.
A simple request flow.
User → IdP/MFA
A finance analyst in New York signs into the identity provider with MFA (ideally FIDO2/WebAuthn).
Device & context checks
An endpoint management tool confirms the laptop is encrypted, patched and running EDR; geolocation and IP reputation are scored.
Policy engine decision
A central engine evaluates policies: role, time, device health, data sensitivity, and regulatory requirements (e.g., GDPR data residency for records stored in Ireland or Germany).
Enforcement point (ZTNA / proxy / gateway)
A ZTNA or SASE service grants access only to the specific SaaS app, Kubernetes API or internal API not the broader VPC.
Continuous inspection and logging
Traffic is inspected for threats; logs stream to SIEM/SOAR, where AI/ML flag anomalies for security teams in Austin, London or Warsaw.
This pattern works across SaaS, IaaS and on-prem workloads and is already baked into many modern cloud-first architectures.
Microsegmentation, Least Privilege and Continuous Verification
Microsegmentation (or zero trust segmentation, ZTS) breaks networks into small, policy-driven zones: for example, separating payment processing in Paris from analytics clusters in Milan, or isolating pathology lab networks in an NHS trust.
Least-privilege policies and continuous verification help demonstrate compliance with HIPAA Security Rule safeguards in US hospitals, PCI DSS in payment environments, and ISO 27001 / SOC 2 across regulated SaaS platforms. AI-driven anomaly detection tools then watch for suspicious patterns such as mass file access, strange admin logins or unusual data egress from Frankfurt to non-EU regions.
Why Zero Trust Security Matters More in 2025
In 2025, zero trust security is no longer “nice to have” because regulators, attackers and boards all assume networks will be breached at some point. NIS2 in the EU, evolving UK-GDPR guidance, updated HIPAA expectations and new SEC cybersecurity disclosure rules push organisations to show structured, risk-based controls and rapid incident handling which zero trust directly supports.
Ransomware remains a top driver. Recent research suggests average ransomware incident costs around $5–6M, while the median ransom payment in 2025 is still around $1M despite enforcement pressure. At the same time, around 60–80% of organisations say they have implemented or plan to implement a zero trust security strategy in the near term, showing how mainstream the model has become.
Zero trust doesn’t guarantee safety, but it does shrink blast radius, slows attackers down and gives security and legal teams a clearer story when dealing with regulators, insurers and boards in New York, London or Berlin.
US Context
In the US, NIST SP 800-207 and NCCoE reference architectures give federal agencies and enterprises a blueprint for zero trust adoption. Public companies now face SEC cybersecurity disclosure rules that require timely reporting of material incidents and board-level oversight of cyber risk, making “assume breach” architectures attractive to boards and auditors.
Hospitals in New York or Austin can use zero trust security to tighten access to EHRs and medical devices, aligning with HIPAA Security Rule safeguards and proposed updates around MFA, segmentation and encryption.
Financial firms in San Francisco map strong identity controls, microsegmentation and monitoring to PCI DSS, SOC 2 and ISO 27001.
Critical infrastructure in Texas use zero trust segmentation to protect OT/ICS and remote admin access.
UK and NHS Context.
The UK’s NCSC has published zero trust architecture principles and implementation guidance, encouraging organisations to understand their architecture, identities and data flows and to implement continuous verification.
NHS bodies and suppliers, guided by the NCSC Cyber Assessment Framework and NHS-specific cyber charters, are moving toward identity-centric, segmented architectures to reduce the impact of attacks on clinical systems in London, Manchester, Cardiff and Edinburgh. UK-GDPR and data protection laws still require strong safeguards over health and citizen data, with the ICO emphasising “appropriate technical and organisational measures” zero trust gives a concrete way to implement those measures.
For UK SMEs, pragmatic steps like moving from flat VPN access to ZTNA for a few key SaaS apps and segmenting critical servers can materially lower ransomware blast radius without huge budgets.
Germany and Wider EU.
Across Germany and the wider EU, NIS2, GDPR, the Cyber Resilience Act (CRA) and DORA all point toward identity-centric, least-privilege models for operators of essential and important entities. ENISA’s 2025 NIS2 implementation guidance explicitly maps technical measures to risk-management obligations, including access control, segmentation and monitoring all core zero trust security capabilities.
Banks supervised by BaFin or the ECB in Frankfurt, Amsterdam or Dublin, as well as cloud and telecom operators in Berlin, Brussels, Madrid or Warsaw, are therefore turning to zero trust as a practical architecture to demonstrate compliance and resilience.
How to Start Implementing Zero Trust Security in 2025
How Can a Mid-Sized US, UK or EU Organisation Start Without “Big Bang” Risk?
The safest way to begin is to start small: map your most critical identities, applications and data, then apply zero trust security controls to a single high-value use case (for example, remote access to a key SaaS app or privileged access to production). Prove value, refine policies and expand iteratively instead of trying to replace your entire security stack at once.
For a mid-sized organisation in Boston, London or Munich, that usually means bringing together the CISO, CIO, IT operations, security architects and compliance leads, then agreeing on one or two business-critical flows to secure first such as finance systems, EHRs or customer portals.

A Practical Zero Trust Roadmap: 90-Day, 12-Month and Multi-Year Milestones
A simple, realistic roadmap for zero trust security.
0–90 days
Inventory users, admins, devices and critical apps (SaaS and self-hosted).
Roll out phishing-resistant MFA and basic conditional access for key systems.
Launch a small ZTNA pilot for remote workers accessing a sensitive internal app.

3–12 months
Introduce microsegmentation for production workloads in your main regions (e.g., AWS eu-central-1, Azure UK South).
Enforce device posture checks for admin and developer access.
Improve logging, centralise into SIEM and create playbooks for anomalous access.
Multi-year
Move toward policy-as-code, automating approvals and reviews.
Integrate zero trust signals with SOC/SIEM/SOAR and data security platforms.
Continuously tune policies based on incident learnings, new regulations and business changes.
This staged approach keeps business stakeholders onside while still showing visible progress to regulators and boards within the first 6–12 months.
Typical Challenges with Legacy Systems, Multi-Cloud and Remote Workforces
Zero trust security meets reality when you hit.
Legacy VPNs, mainframes and OT/ICS
You can’t always bolt modern agents onto a mainframe in Zurich or a SCADA system near Warsaw. Start with gateways and compensating controls ZTNA in front of legacy protocols, bastion hosts and strong identity for admins.
Cloud sprawl
AWS, Azure and Google Cloud plus sovereign or local providers across the EU quickly get messy. Use consistent identity, tagging and segmentation patterns; Mak It Solutions covers this in more depth in guides like Future of Cloud Hosting and Cloud Cost Optimization.
Remote and hybrid work
Globally distributed teams, contractors and third parties demand internet-facing access. Zero trust-style ZTNA and SASE give those users controlled, auditable paths without opening whole networks.
Evaluating Zero Trust Platforms, ZTNA and SASE Vendors
ZTNA vs VPN vs SASE.
ZTNA provides identity-aware, application-level access based on policies, while classic VPNs create broad network tunnels; SASE bundles zero trust networking with secure web gateway, CASB and other controls delivered as a cloud service. In 2025, most organisations use ZTNA or SASE to replace or heavily augment legacy VPNs, especially for remote and third-party access.
As a rule of thumb.
VPN: simple, but high lateral-movement risk and poor visibility.
ZTNA: a good fit for app-centric access to internal HTTP/SSH/RDP services.
SASE: best for distributed workforces needing secure access to web, SaaS and private apps from many locations.
What to Look For in Zero Trust Security Vendors in the US, UK and EU
When shortlisting ZTNA/SASE platforms (e.g., Microsoft Security, Google Cloud, CrowdStrike, Zscaler, IBM, HPE, NordLayer and others), focus on.
Identity integration: deep support for Okta, Entra ID and on-prem directories.
Policy engine & logging: fine-grained policies and exportable, structured logs to your SIEM.
Compliance & GEO: data residency controls, GDPR/UK-GDPR/NIS2 alignment, HIPAA-friendly options for healthcare, and regulatory readiness for BaFin/FCA-supervised entities.
Open standards and integrations: SAML/OIDC, SCIM, modern APIs and connectors into your existing SOC/SIEM/SOAR stack.
If you’re evaluating options and architectures, Mak It Solutions’ teams who build secure web development, back-end APIs and mobile apps can help validate how different vendors will behave in your actual stack.
Industry-Specific Examples: Healthcare, Financial Services and Public Sector
Healthcare (NHS & US hospitals)
Zero trust security restricts who can access EHRs and connected devices, enforces encryption and supports HIPAA and NHS cyber requirements.
Financial services
Banks in Frankfurt or Amsterdam map ZTNA, strong identity and network segmentation to DORA, PCI DSS and Open Banking/PSD2-PSD3 requirements.
Public sector and critical infrastructure
Ministries in Brussels or Warsaw use zero trust to secure remote admin access, OT gateways and citizen portals, often alongside multi-cloud and sovereign cloud strategies.
If you want a sector-specific maturity assessment, you can also draw on Mak It Solutions’ work across business intelligence and analytics, digital marketing and web properties and recent cloud-focused guides such as AWS vs Azure vs Google Cloud Comparison 2025.
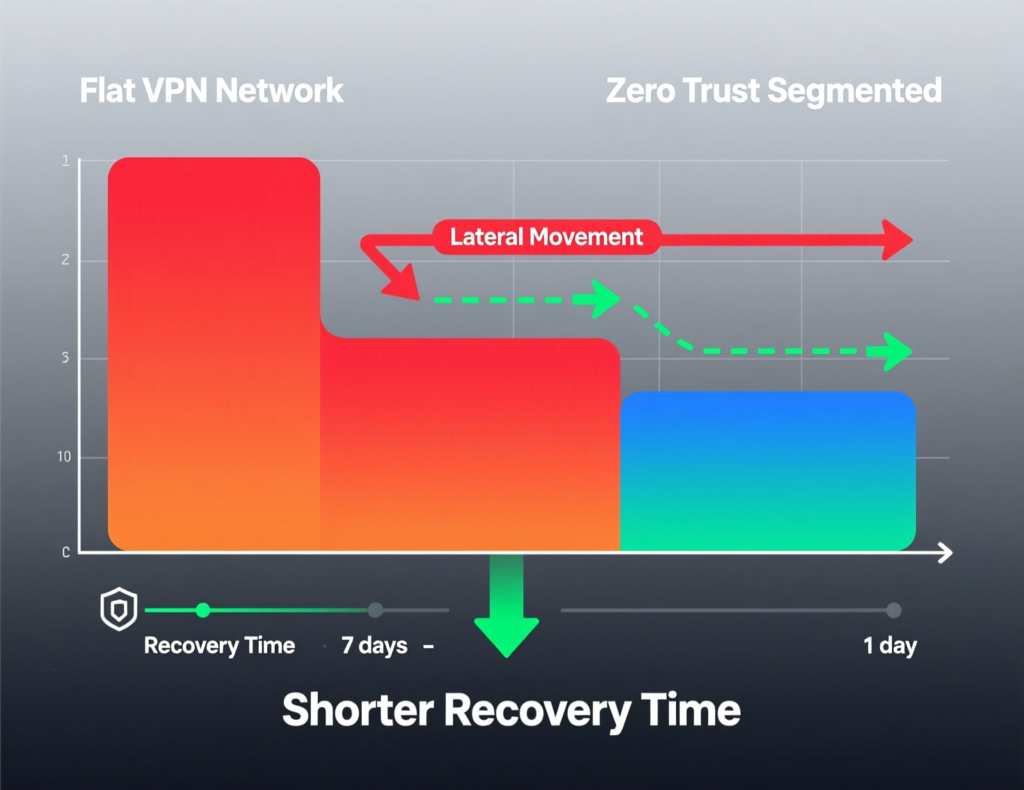
Concluding Remarks
Zero trust security is no longer a buzzword it’s a practical, identity-centric way to reduce breach impact, align with 2025 regulations like NIS2, GDPR/UK-GDPR, HIPAA and SEC rules, and prove resilience to boards and regulators. Instead of chasing a perfect end state, successful organisations in the US, UK, Germany and across the EU start with focused pilots, learn fast and expand iteratively.
Mak It Solutions can help you map your current estate, prioritise high-value use cases and design a zero trust security roadmap that fits your budget and regulatory footprint.
If you’re a CISO, CIO or security lead wondering how “never trust, always verify” should look in your actual environment, you don’t need to figure it out alone. Share your top three critical systems, your main regions (US, UK, EU) and your compliance drivers, and the Mak It Solutions team can shape a scoped zero trust roadmap.
Request a short, no-obligation consultation to review your architecture, or ask us to run a 90-day zero trust pilot plan that your internal teams can execute with or without further help.( Click Here’s )
FAQs
Q : Is zero trust security required for NIS2 or other EU regulations, or just “nice to have”?
A : Zero trust security is not named explicitly in NIS2 or GDPR, but the underlying ideas strict access control, segmentation, continuous monitoring and incident reporting are core expectations. Many operators of essential and important entities in the EU now treat zero trust as the most practical way to meet risk-management and governance obligations. In Germany and other EU states, supervisors increasingly expect identity-centric, least-privilege architectures when assessing NIS2 readiness.
Q : Can zero trust work alongside legacy VPNs, mainframes and on-prem applications, or do we need to replace everything first?
A : You don’t have to replace everything upfront; most organisations run zero trust security alongside legacy tech for several years. Typically, you put ZTNA or secure gateways in front of old apps, limit broad VPN access and gradually migrate users and workloads to more granular zero trust patterns. For mainframes and OT systems that can’t run modern agents, you use segmented network zones, bastion hosts and strong identity for admins as compensating controls. Over time, the VPN shrinks to a niche role or disappears.
Q : How long does a typical zero trust rollout take for a mid-sized organisation in the US, UK or EU?
A : A realistic timeline is 3–6 months for initial pilots, 12–24 months to cover the most critical systems and several years to fully embed zero trust across multi-cloud and on-prem environments. The pace depends on legacy complexity, regulatory deadlines and budget. Many organisations aim to show visible progress (MFA, ZTNA pilots, some segmentation) within the first 6–12 months to reassure boards, regulators and customers that they are moving beyond perimeter-only security.
Q : What impact does zero trust have on employee experience and performance for remote and hybrid workers?
A : Done badly, zero trust can feel like more prompts and friction; done well, it often improves experience compared with clunky VPNs. ZTNA and SASE tools can give users in New York, London or Berlin fast, direct connections to apps without hair-pinning traffic through a central data centre. Modern identity-first experiences with passwordless login and smart session management can also reduce login fatigue. The key is to design policies around risk and user journeys, not just technology.
Q : How much budget should we plan for a zero trust security programme compared with traditional perimeter upgrades?
A : Most surveys show that zero trust typically consumes a minority share of the overall cyber budget often under 25% but the range is wide. You’ll invest in identity, ZTNA/SASE, logging and analytics rather than more perimeter appliances. The business case often looks stronger when you factor in reduced breach impact, lower VPN overhead, simplified remote access and regulatory confidence. A good first step is a small pilot with clear before/after metrics on risk, user experience and operational complexity


