DevSecOps Best Practices 2025 Guide for US & Europe
DevSecOps Best Practices 2025 Guide for US & Europe
DevSecOps Best Practices 2025: CI/CD Guide for US & Europe
DevSecOps best practices mean building security into every stage of your CI/CD pipelines code, build, test, deploy and run instead of relying on manual, late-stage reviews. By automating checks, treating security as code and embedding compliance (GDPR/DSGVO, UK-GDPR, HIPAA, PCI DSS, NIS2) into your pipelines, teams in the US, UK and Europe can ship software faster with significantly lower risk.
Why US & European Teams Care
Modern software teams in New York, London, Berlin or San Francisco can’t afford to treat security as an afterthought anymore. Releases are now daily, infrastructure is multi-cloud, and regulations in the US, UK and EU are getting stricter each year.
The global DevSecOps market is already estimated at roughly $7.5B in 2023 and projected to grow to more than $30B by 2030, as organizations turn security into a first-class part of software delivery.
In 2025, DevSecOps best practices are as much about culture as tools: shift-left security in software delivery, security-as-code in DevOps pipelines, automated security testing in CI/CD, and continuous compliance for frameworks like GDPR/DSGVO, UK-GDPR, HIPAA, PCI DSS, SOC 2, ISO 27001 and NIS2. Teams that get this right in the US, UK, Germany and wider EU deliver features quickly and satisfy regulators, auditors and customers.
DevSecOps Best Practices at a Glance
The essential DevSecOps best practices for modern CI/CD pipelines are: shared responsibility culture, shift-left security, automated testing in CI/CD, security-as-code, secure software supply chain, least-privilege access and continuous compliance monitoring. When these practices are wired into GitHub, GitLab, Azure DevOps or Jenkins, your pipelines become both faster and safer instead of security being a blocker.
Top 10 DevSecOps best practices teams must adopt
Here’s a practical checklist you can drop into a leadership or engineering review.
Threat modeling early
Run lightweight threat models during planning for new features, especially for payments, PHI or PII.
Secure coding standards
Adopt OWASP-based standards and linters; enforce via pull request templates and IDE plugins.
Automated SAST
Scan code for injection, auth and crypto issues on every merge request.
DAST in CI/CD
Run dynamic scans against test environments before production.
SCA & SBOMs
Continuously scan open-source dependencies and generate SBOMs to secure your software supply chain.
Secrets management
Use vaults and cloud-native secret stores instead of .env files and hard-coded keys.
Least-privilege access
Apply RBAC in Git repos, CI/CD, Kubernetes and cloud accounts.
Container & Kubernetes hardening
Use minimal base images, signed artifacts, admission controllers and runtime policies.
Cloud guardrails –
Implement policy-as-code for AWS, Azure and GCP to enforce encryption, logging and network segmentation.
Incident response & training
Maintain playbooks, run gamedays and provide continuous security training for devs and SREs.
From DevOps security best practices to full DevSecOps maturity
Traditional “DevOps security best practices” relied on perimeter firewalls, VPNs and occasional penetration tests. That worked when releases were quarterly and most workloads ran in a single US or UK datacenter. Today, with cloud-native apps and daily deploys, those practices alone are not enough.
DevSecOps maturity typically looks like this.
Security tests run automatically on every change.
Developers own fixing vulnerabilities before code ships.
AppSec engineers act as coaches and toolsmiths, not ticket factories.
Evidence for audits is generated by pipelines, not spreadsheets.
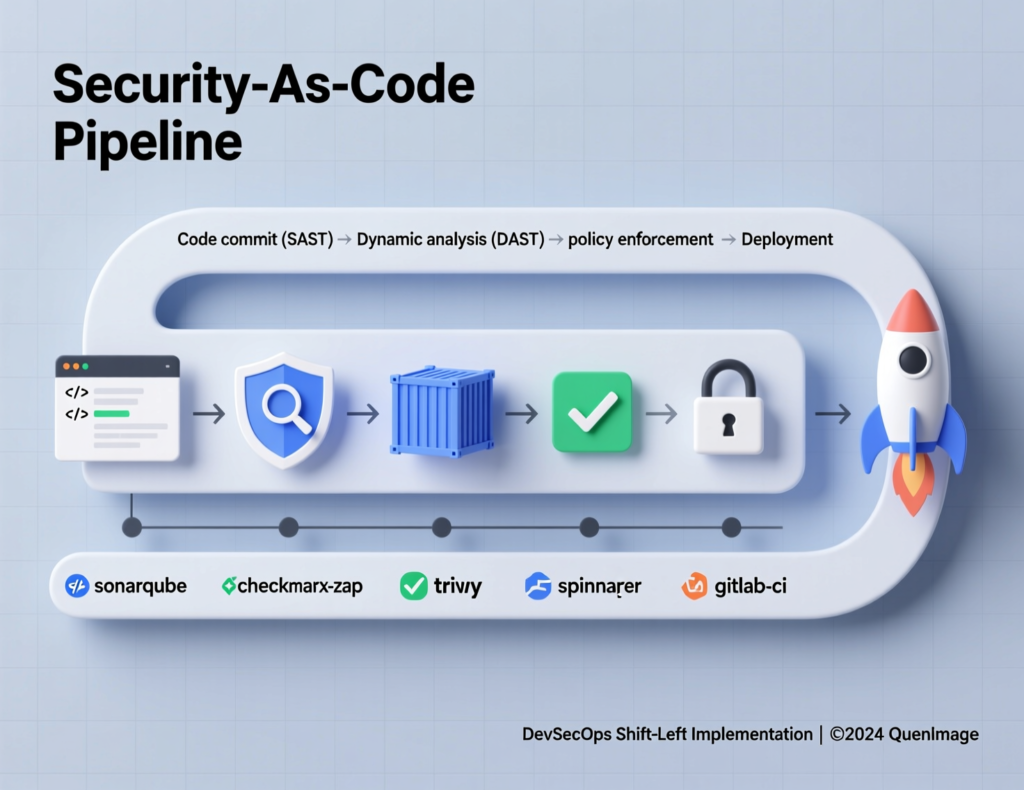
Most teams move through three stages
Security at the end
Manual pen tests, ad-hoc reviews.
Security alongside
SAST/SCA/DAST tools plugged into CI/CD, but optional.
Security inside
Security is part of “definition of done”; builds can’t ship with critical issues or missing controls.
How DevSecOps best practices differ for US, UK and German/EU teams
The core patterns are similar everywhere, but regulation changes the emphasis.
US
SOC 2, HIPAA and PCI DSS drive controls like encryption, logging, access management and incident response, particularly for hospitals and fintechs in New York, Austin or San Francisco.
UK
UK-GDPR, the FCA and NHS/NHS Digital guidance emphasize data minimisation, DPIAs, breach notification and third-party risk for London- and Manchester-based firms.
Germany/EU
DSGVO (GDPR), BaFin and NIS2 add strict data residency, operational resilience and supply chain security requirements for organizations in Berlin, Frankfurt, Munich and across the EU.
Your DevSecOps design should treat compliance as configuration: use the same pipeline patterns everywhere, but attach different policies or stages for workloads subject to HIPAA versus NIS2, or US versus EU data residency.
What Is DevSecOps? Principles, Culture and Roles
DevSecOps is the practice of integrating security into every phase of the software delivery lifecycle so developers, operations and security share ownership of risk. It’s more effective than late-stage security reviews because vulnerabilities are found where they are cheapest to fix inside code and pipelines rather than in production or during an audit.
DevSecOps vs DevOps vs SecOps for modern software teams
DevOps focuses on speed, automation and collaboration between dev and ops.
SecOps focuses on monitoring, incident response and threat detection once systems are running.
DevSecOps connects both: it adds security design, automated controls and checks from planning through deployment and operations.
At Apple-scale organizations and mid-market SaaS companies alike, you’ll typically see:
Product teams owning security for their services (“you build it, you secure it”).
A central platform/DevEx team owning shared CI/CD, Kubernetes and guardrails.
A security team establishing standards, providing tooling and handling complex incidents.
Shift-left, automation and security-as-code
Three principles show up in every successful implementation.
Shift-left security
Move threat modeling, secure design and code scanning earlier in the lifecycle.
Automation-first
Run security checks automatically on every merge/build, not as manual checklists.
Security-as-code
Version policies, access rules, infrastructure and controls in Git alongside application code.
Add one simple rule: if devs can’t run it locally or in a feature branch, they won’t use it. Good DevSecOps design keeps feedback fast and actionable so developers in Boston, London or Munich can see issues before they ever hit staging.
Building a culture of shared responsibility across dev, ops and security
Culture change is the hardest part, especially for US healthcare providers, UK SMEs or German Mittelstand manufacturers modernising legacy systems.
Practical moves:
Security champions
Nominate a developer in each squad to pair with AppSec and evangelize best practices.
Blameless postmortems
Treat security incidents like other outages; focus on learning, not blame.
Embedded AppSec
Pair AppSec engineers with high-risk products (payments, PHI, identity) for design and code reviews.
Aligned incentives
Make secure delivery part of engineering KPIs, not just uptime or feature throughput.
Embedding Security into CI/CD Pipelines
Embedding security into DevOps pipelines is more effective than periodic pen tests because every change is checked consistently and automatically. The trick is to map checks to each pipeline stage, add lightweight security gates and codify policies so your CI/CD platform can enforce them.
Mapping DevSecOps checks to each pipeline stage (plan, code, build, test, deploy)
A simple stage-by-stage pattern looks like this.
Plan
Capture data classification, threat model and regulatory impact (e.g., “touches card data → PCI DSS”).
Code
Enforce secure coding standards, secret scanning and SAST on every pull/merge request.
Build
Run SCA and container scans, generate SBOMs and sign artifacts.
Test
Run DAST, API security tests and fuzzing against ephemeral test environments.
Deploy & run
Apply infrastructure-as-code scanning, Kubernetes admission policies, runtime monitoring and anomaly detection.
This model works whether you’re running on AWS, Azure or GCP, or in hybrid setups described in Mak It Solutions’ cloud repatriation and multi-cloud strategy guides. ([makitsol.com][8])
Security gates and policy-as-code that don’t block delivery
Security gates should be risk-based, not absolutist.
Block builds only on critical issues (e.g., RCE, leaked keys, missing encryption).
Warn on medium/low issues and backlog them with clear SLAs.
Use tools like Open Policy Agent and cloud-native policy engines to encode rules as code. ([Amazon Web Services,
For teams in New York, London or Berlin, that might mea.
Branch protection rules requiring passing SAST/SCA checks before merge.
Per-environment approvals (e.g., extra review for production in EU regions).
Different policy bundles for US HIPAA workloads versus German BaFin-regulated systems.
Tools & Automation for DevSecOps in the Cloud
Modern DevSecOps toolchains combine SAST, DAST, SCA, container/Kubernetes security and cloud-native controls wired into your CI/CD platforms. For teams on AWS, Azure and GCP, the winning pattern is to standardize on a small set of opinionated tools rather than dozens of overlapping scanners.
A 2025 GitLab survey found 53% of DevSecOps teams use more than five security tools and lose around seven hours per week to inefficient processes. That’s exactly the kind of sprawl you want to avoid in busy US and European engineering orgs.
SAST, DAST and SCA tools for application security in DevSecOps pipelines
SAST
Catches coding flaws (injection, insecure deserialization, auth issues) before build.
DAST
Probes running apps for misconfigurations and exploitable flows.
SCA
Tracks third-party libraries, licenses and known CVEs.
Platforms like Checkmarx, Snyk, Wiz, Kiuwan and others plug directly into GitHub, GitLab and Azure DevOps, providing pull-request feedback for US fintechs, UK Open Banking platforms and EU SaaS providers. Most can also push findings into ticketing systems so remediation is tracked, not just reported.
Container, Kubernetes and cloud-native security on AWS, Azure and GCP
For cloud-native apps
Use container scanning in CI/CD and signed images in registries.
Enforce Kubernetes policies via admission controllers and tools like Gatekeeper.
Follow AWS, Azure and GCP DevSecOps reference architectures that show how to integrate CI/CD, scanning, artifact registries and Binary Authorization. ([Amazon Web Services, Inc.][4])
This is also where Mak It Solutions’ content on cloud cost optimization, serverless architectures and multi-cloud hosting ties in: security controls should be designed alongside performance and cost, not bolted on afterwards.
Automating DevSecOps for regulated sectors (US, UK, Germany/EU)
Sector-specific examples:
US healthcare (HIPAA)
Encrypt PHI, enforce multi-factor access, log all access to ePHI and prove risk analysis is ongoing.
US fintech / PCI DSS
Segment cardholder data environments, monitor access and run continuous vulnerability scans.
UK FCA-regulated firms & NHS suppliers
Implement strong access controls, audit trails and DPIAs for systems handling patient or financial data.
BaFin-regulated German banks (and NIS2 operators)
Design resilient, well-monitored infrastructure with strong supply chain security and incident reporting workflows. ([Digital Strategy][7])
In all cases, automate evidence collection: policy results, logs and reports should be stored centrally for auditors rather than rebuilt manually each year.
Note
This article shares general DevSecOps and compliance patterns and is not legal, regulatory or financial advice. Always work with your legal and compliance teams when interpreting frameworks like GDPR, HIPAA, PCI DSS or NIS2.
GDPR, HIPAA, PCI DSS, NIS2 & More
Compliance-driven DevSecOps turns legal requirements like GDPR/DSGVO, UK-GDPR, HIPAA, PCI DSS, SOC 2, ISO 27001 and NIS2 into automated controls and evidence inside your pipelines. Instead of “compliance projects” every few years, you maintain continuous compliance.
Translating GDPR/DSGVO, UK-GDPR, CCPA and NIS2 into DevSecOps controls
From regulations to pipeline rules.
Data minimisation → CI checks that new fields are justified and properly classified; schema reviews for personal data. ([Eur-Lex][13])
Encryption in transit/at rest → IaC policies banning plaintext protocols and unencrypted storage.
Access controls & logging → Policy-as-code enforcing least privilege and mandatory audit trails.
DPIAs → Threat modeling as part of design for high-risk processing (e.g., profiling, sensitive health data).
Breach notification → Automated incident playbooks and centralised logging/alerting to detect and triage potential breaches.
NIS2, in particular, pushes EU organizations to adopt stronger risk management, incident reporting and supply chain controls perfectly aligned with DevSecOps practices.

DevSecOps patterns for HIPAA, PCI DSS, SOC 2 and ISO 27001 evidence
For US, UK and EU organizations targeting multiple frameworks:
Maintain a control matrix mapping each pipeline control to HIPAA, PCI DSS, SOC 2 and ISO 27001 clauses. ([HHS][14])
Attach pipeline logs, reports and change histories as evidence artifacts.
Use central GRC platforms or even versioned folders in Git to store signed reports.
The goal is that when auditors ask “prove that code handling card data is always scanned for vulnerabilities,” you can show a CI job that runs on every commit, plus months of run history.
NHS suppliers, US healthcare and German BaFin-regulated banks
NHS suppliers and UK healthtech
Need DevSecOps pipelines that demonstrate secure handling of NHS data, strict access controls and incident response processes aligned to NHS Digital guidance.
US hospitals
Often run hybrid pipelines with on-prem and cloud workloads; DevSecOps here focuses on ePHI encryption, network segmentation, continuous vulnerability management and robust backups.
BaFin-regulated banks in Berlin, Frankfurt, Munich
Must demonstrate operational resilience and effective risk management, including for cloud and third-party services. DevSecOps practices around software supply chain security and NIS2-aligned controls directly support this.
How to Implement DevSecOps Without Slowing Delivery
The safest way to implement DevSecOps best practices without hurting delivery is to start with a focused 90-day pilot, automate the highest-value checks first, then scale across teams with clear KPIs and coaching. You’re aiming for small, visible wins in one product stream in San Francisco, London or Berlin then repeating the pattern.
90-day DevSecOps rollout roadmap for existing DevOps teams
Use this as your high-level playbook:
Days 1–15 – Assess
Inventory your CI/CD pipelines, cloud accounts and repos.
Identify critical systems (payments, PHI, identity, core banking).
Days 16–30 – Choose one value stream
Pick a product or service team (e.g., a payments API in New York or a patient portal for a UK NHS supplier).
Map current controls and gaps.
Days 31–60 – Implement minimum controls
Add SAST, SCA and secret scanning.
Introduce basic IaC scanning and container scans.
Define simple, risk-based security gates.
Days 61–75 – Improve visibility & training
Build dashboards for vulnerabilities, pipeline health and compliance coverage.
Run security workshops for developers and SREs.
Days 76–90 – Iterate and plan scale-out
Address top recurring issues.
Document patterns and templates to reuse in other teams.
Governance, KPIs and dashboards for DevSecOps success
Executives and CISOs in US, UK and EU organizations care about trends, not individual vulnerabilities. Useful KPIs include.
Mean time to remediate (MTTR) for critical vulnerabilities.
Percentage of builds passing all security checks.
Percentage of services with SBOM and supply chain coverage.
Compliance coverage by region (US, UK, EU) and framework.
Dashboards in tools like GitLab, Azure DevOps or custom BI stacks (for example, the analytics approaches Mak It Solutions covers in its BI vs analytics content) can aggregate this for leadership.
Choosing DevSecOps partners, platforms and internal champions
When selecting platforms and partners.
Prioritize developer experience Clear feedback, minimal false positives.
Check data residency options for EU and UK workloads.
Evaluate coverage across AppSec, infra, cloud, AI and software supply chain risks.
Mak It Solutions often helps teams evaluate trade-offs across AWS, Azure and GCP, drawing on prior work comparing cloud providers, cloud repatriation options and Middle East or EU data localization strategies.
Internally, identify security champions in Austin, Manchester or Munich who can bridge central security and local product teams.

To Sum Up
Security is no longer a separate function that “approves” releases. For organizations across the US, UK, Germany and wider Europe, DevSecOps best practices turn security into a built-in property of your CI/CD pipelines and cloud platforms. The next step is to assess where you are today and design a 90-day path toward a safer, faster, more compliant delivery model.
Key Takeaways
DevSecOps best practices bring security into every CI/CD stage rather than relying on late reviews.
Regulations like GDPR/DSGVO, UK-GDPR, HIPAA, PCI DSS and NIS2 can be translated into pipeline controls and automated evidence.
A 90-day pilot on one product is the fastest way to prove value without slowing delivery.
Toolchain sprawl hurts; aim for a streamlined, integrated platform across AppSec, infra and cloud.
Culture and incentives matter as much as scanners: security champions, training and shared KPIs are essential.
If you’re unsure where your current pipelines stand, start with the self-assessment above and pick one high-impact product as your pilot. Mak It Solutions can help you review your CI/CD stack, design a DevSecOps reference architecture for AWS, Azure or GCP, and align it with US, UK and EU regulatory requirements.
Book a short DevSecOps discovery session and we’ll walk through your current pipelines, risks and a practical 90-day roadmap tailored to your teams. ( Click Here’s )
FAQs
Q : How do DevSecOps responsibilities differ between security engineers and developers?
A : Developers are responsible for writing secure code, fixing vulnerabilities surfaced by tools and following secure coding standards in their day-to-day work. Security engineers focus on setting policies, choosing and integrating tools, threat modeling and responding to complex incidents. In a healthy DevSecOps culture, security engineers coach and enable developers, while developers own the security of the services they build.
Q : Do we need a dedicated DevSecOps engineer or team, or can existing roles cover it?
A : Many teams start by upskilling existing DevOps and security staff, plus appointing security champions in each squad. As pipelines, regulations and tooling become more complex, a dedicated DevSecOps engineer or platform security team often emerges to own shared templates, policies and guardrails. The key is that someone is accountable for the security of your CI/CD platforms, even if it’s initially a part-time hat.
Q : How should startups vs large enterprises prioritize DevSecOps investments in 2025?
A : Startups in the US, UK or EU should focus on the basics: SAST, SCA, secret scanning, strong access control and hardened cloud environments for their main product. Large enterprises with multiple business units and regions need to prioritize standardizing CI/CD platforms, building shared security services and mapping controls to frameworks like SOC 2, ISO 27001, HIPAA, PCI DSS and NIS2. In both cases, a focused 90-day pilot is the best way to prove value before scaling.
Q : What are effective DevSecOps KPIs and dashboards for engineering leaders and CISOs?
A : Effective DevSecOps KPIs combine engineering and security metrics: vulnerability MTTR, percentage of builds passing security checks, coverage of SAST/SCA/DAST across services, incident frequency and time to contain, and compliance coverage by region and framework. Dashboards should let leaders in New York, London or Munich quickly compare teams, spot bottlenecks and decide where to invest in training or tooling.
Q : How can teams safely use AI code assistants inside a DevSecOps pipeline without increasing risk?
A : AI code assistants can boost productivity, but they can also introduce insecure patterns or license risks. To use them safely, enforce SAST/SCA on all AI-generated code, tune coding guidelines and restrict assistants from accessing sensitive production data. Many organizations also add review requirements for AI-suggested changes in critical modules and log which commits used AI assistance to support future audits especially for regulated sectors.


