Shadow IT Management in 2025: From Risk to Strategic Asset
Shadow IT Management in 2025: From Risk to Strategic Asset

Shadow IT Management in 2025: From Risk to Strategic Asset
Shadow IT management in 2025 is the structured discovery, risk assessment and governance of unsanctioned SaaS, cloud and AI tools so they stay secure, compliant and aligned with business goals. When CIOs and CISOs combine modern discovery tooling with “managed freedom” policies and a 90-day roadmap, shadow IT shifts from a security liability into a governed innovation pipeline.
Introduction
Shadow IT management has quietly become one of the hardest problems in modern IT especially for remote and hybrid teams spread across New York, London and Berlin. Between shadow SaaS, rogue cloud test accounts and unapproved generative AI tools, most enterprises now run dozens (or even hundreds) of unsanctioned applications outside formal IT governance. Research suggests that around 30–40% of enterprise SaaS is effectively shadow IT, with a large majority of SaaS and AI tools going unmanaged.
This guide gives CIOs, CISOs and IT leaders in the US, UK, Germany and wider EU a practical, regulator-ready playbook for shadow IT management in 2025. You’ll get a clear definition, a risk and compliance lens (GDPR/DSGVO, UK GDPR, HIPAA, PCI DSS, SOX, BaFin), tooling options, and a 90-day roadmap that moves you from firefighting to a repeatable, innovation-friendly governance model.
What Is Shadow IT Management in 2025?
Shadow IT management in 2025 means systematically discovering, assessing and governing unsanctioned apps, SaaS and AI tools across your business, rather than pretending they don’t exist. It’s a shift from older, centralized IT governance models to one that assumes business-led IT, citizen developers and BYOD are the default, not the exception.
Definition From Shadow IT to Shadow SaaS and Shadow AI
Shadow IT used to mean a few rogue servers under someone’s desk. Today it’s mostly shadow SaaS and shadow AI: tools like Notion, extra Slack workspaces, Figma, ChatGPT-style assistants and untracked browser extensions that teams adopt without IT approval. Shadow IT management is the process of:
Discovering these tools (SaaS, cloud, mobile, AI)
Assessing their security, compliance and data flows
Deciding whether to block, tolerate, or formally onboard them
Monitoring usage and risk on an ongoing basis
Done well, it becomes a continuous lifecycle, not a one-off cleanup project.
Shadow IT vs Traditional IT Governance
Traditional IT governance was built for centralized stacks: on-prem servers, a short list of approved apps, and strict “command-and-control” change boards. In 2025, that model breaks under SaaS sprawl and business-led IT. Studies show that a majority of employees now use at least one unsanctioned SaaS tool, and IT often discovers 30–40% more apps once discovery tools are deployed.
Modern shadow IT management accepts that business units will experiment. Instead of blanket bans, you define guardrails (data residency, identity, logging, vendor baselines) and then enable safe experimentation. Frameworks like ITIL and COBIT still matter but they’re adapted for distributed cloud and SaaS ecosystems, not just data centres.
Where Shadow IT Lives Today: SaaS, Cloud, Mobile and AI
In 2025, shadow IT hotspots are easy to recognize
Shadow SaaS and unsanctioned cloud apps free tiers of Dropbox or Box, extra Slack or Zoom tenants, rogue Salesforce sandboxes, “just a quick” Trello board for a London project team.
Cloud and Dev environments AWS test accounts, unmanaged GCP projects or Azure subscriptions spun up outside your landing zone, often in non-EU regions.
Mobile and messaging WhatsApp groups in NHS trusts, Telegram for support teams, personal devices accessing corporate Microsoft 365 or Google Workspace.
Shadow AI employees pasting sensitive data into public chatbots or using unapproved AI coding assistants that train on your source code.
A serious shadow IT inventory spans all of these not just SaaS tools already sitting behind SSO.
Why Shadow IT Happens and Why It Won’t Go Away
Shadow IT happens because people are trying to get work done faster than your official processes allow. You can’t “policy” that away; you can only design better governance and better services.
Employee Workarounds, Citizen Developers and Business-Led IT
In a London fintech or New York SaaS scale-up, product teams will happily swipe a credit card for a new analytics tool if the official BI stack is too slow. In a US hospital, clinicians might use consumer messaging apps because the approved system is clunky. In the German Mittelstand, engineers may prototype Industrie 4.0 dashboards in a shadow low-code tool when central IT is overwhelmed.
Citizen developers and business-led IT are not going away they’re now a core part of how organizations innovate. Shadow IT management is about partnering with these teams, not shutting them down.
Friction in Official IT: Slow Processes, Legacy Stacks and Gaps
When procurement cycles take months, VPNs are painful, and legacy systems can’t do what teams need, “unsanctioned applications” look like the only realistic choice. Surveys show nearly 60% of IT pros struggle with SaaS sprawl and that around two-thirds of SaaS apps may be adopted without IT’s knowledge.
Reducing shadow IT starts with reducing this friction: faster intake processes, clearer app catalogs, and better integration patterns the same principles Mak It Solutions applies when building cloud-native and low-code platforms for clients across the US, UK and EU. (Mak it Solutions)
Regional Nuances: US Enterprises vs UK Public Sector vs German Mittelstand
US enterprises often push hard on innovation AI pilots in San Francisco, new SaaS tools in New York with frameworks like HIPAA, PCI DSS and SOX defining hard red lines for healthcare and finance.
UK public sector & NHS teams operate under UK GDPR and strict NHS data rules; they tend to tolerate less risk and demand clear DPIAs and ICO-aligned governance.
German/EU organizations prioritize DSGVO/GDPR, BaFin expectations, KRITIS and upcoming EU AI rules, often insisting on EU data residency (Frankfurt, Dublin, Amsterdam).
Your shadow IT strategy has to reflect these GEO realities, not just generic best practices.
Security, Compliance and Regulatory Risks of Shadow IT
For regulated industries, the biggest shadow IT question is simple: what is this doing to our risk and compliance posture?
Top Security Risks: Data Exposure, Account Takeover and Shadow AI Breaches
Unmanaged SaaS and AI tools expand your attack surface in ways legacy controls can’t see.
Data leakage sensitive datasets uploaded to unknown tools or AI models, often stored outside intended regions.
Account takeover weak or recycled passwords on apps that aren’t behind SSO or MFA, making them ideal entry points for attackers.
Uncontrolled AI training data public AI tools may reuse inputs as training data; once customer tables are pasted into a chatbot, you’ve effectively created a shadow data copy.
Recent reports show that a majority of SaaS and AI tools in many organizations are unmanaged, and that a significant share of new SaaS onboarded in 2023–2025 went live without formal IT security review.
Compliance Landmines: GDPR/DSGVO, UK GDPR, HIPAA, PCI DSS, SOX and BaFin
Shadow IT collides directly with regulations.
GDPR/DSGVO & UK GDPR
You must know where personal data is processed, on what legal basis, and with which processors and sub-processors. Shadow SaaS in a non-EU/Azure/AWS region can invalidate your DPIAs overnight.
HIPAA (US healthcare)
EPHI in unapproved SaaS or AI breaks Security Rule safeguards around confidentiality, integrity and availability.
PCI DSS & SOX
Cardholder and financial data in unmanaged apps creates unlogged access paths and kills audit trails.
BaFin, FCA, SEC, PSD2/Open Banking
Regulators increasingly expect clear third-party risk management, with visibility into all processors and critical outsourcing arrangements.
In practice, this means shadow IT must feed into your risk register, ROPA, and vendor management workflows not sit in someone’s browser history.
Shadow IT Risk Assessment Checklist (AEO-Ready Bullet Summary)
A quick, regulator-friendly checklist.
Data
What data types are processed (PII, ePHI, card data, source code, trade secrets)?
Location
Where is data stored and processed (regions, availability zones, backups)?
Processor
Who is the vendor? Are there sub-processors? Are they SOC 2 / ISO 27001 certified?
Access controls
Is SSO/MFA enforced? Are roles and least-privilege defined?
Logging & retention
Are access logs, admin actions and exports logged, retained and reviewable?
Regimes
Which regulations apply (GDPR/DSGVO, UK GDPR, HIPAA, PCI DSS, SOX, BaFin, KRITIS)?
Review
Has the CISO/DPO (or delegate) approved the risk and documented the decision?
Lift this into a one-page template and you have a simple, repeatable review flow.
Designing a Shadow IT Governance Framework
The goal isn’t to block every unsanctioned application; it’s to create a “managed freedom” model that balances innovation with safety.
Principles of “Managed Freedom” Governing, Not Banning
A workable shadow IT governance framework is built on a few principles.
Assume discovery will reveal more than you expect your first-pass inventory will be incomplete.
Encourage safe experimentation e.g., innovation sandboxes where data is synthetic or anonymised.
Default to SSO and MFA route apps through Okta, Azure AD, JumpCloud or similar where possible.
Tier risk marketing tools vs tools touching patient records or payment data.
Be transparent publish policies and approved catalogs so teams know how to stay compliant.
Mak It Solutions often pairs this with modern cloud architectures — for example, clear AWS/Azure/GCP landing zones and data domains so governance lives in the platform, not just in PDFs. (Mak it Solutions)
Shadow IT Policy Building Blocks and RACI
Your shadow IT policy shouldn’t be a door-stop. Aim for a concise, living document that covers:
Scope & definitions shadow IT, shadow SaaS, shadow AI, business-led IT, citizen development.
Classification low/medium/high-risk apps based on data and criticality.
Approval paths fast-track for low-risk tools; formal onboarding for high-risk or regulated data.
Data residency & sovereignty – EU/UK/US region rules, Schrems II considerations, local KRITIS requirements.
Vendor due diligence SOC 2, ISO 27001, pen-test evidence, DPA terms, DPAs for processors.
RACI who does what (CIO, CISO, DPO, line-of-business owners, platform teams, procurement).
Many organizations align this with their existing ITIL/COBIT and business intelligence governance models, so app, data and analytics decisions are treated consistently. (Mak it Solutions)

Operating Model.
Operationally, think of a simple intake-to-approval pipeline:
Intake a self-service portal (ServiceNow, Jira, custom form) where teams request tools or declare existing usage.
Screening automated checks (domain, data category, region) plus quick security review for low-risk apps.
Formal review for tools in healthcare, finance or public sector, involving security, legal, DPO and sometimes works councils.
Onboarding SSO integration, role design, DLP policies, logging, backup, incident response integration.
Continuous governance periodic recertification, license and usage reviews, de-provisioning as part of off-boarding.
US, UK and German/EU organizations will vary in detail but the core steps are similar, with local regulators shaping the depth and speed of review.
Tools and Techniques to Discover and Manage Shadow IT
The fastest way to lose the shadow IT battle is to rely on manual spreadsheets. Discovery and management need proper tooling.
Discovery Methods: Network, SSO, Browser and Expense-Based Detection
No single method sees everything; combine several.
Network & firewall logs
Classic shadow IT detection via outbound DNS/HTTP to new SaaS domains.
SSO/IDaaS logs
Okta, Azure AD, JumpCloud and similar already know who’s logging into what; they also highlight logins outside your approved catalog.
Browser-based discovery
Endpoint agents or secure browser plugins (e.g., tools like LastPass SaaS Protect or similar SaaS visibility extensions) track app usage without heavy device agents.
Expense & procurement data
Card statements and expense claims surface self-serve SaaS and AI subscriptions.
Together, these build a living map of shadow SaaS and shadow AI across cloud, web and devices.
SaaS Management and Security Platforms for Shadow IT
Once you know what’s out there, you need somewhere to manage it.
SaaS management platforms
Tools like Zylo, Zluri or similar consolidate license data, usage, costs and risk.
Identity & access (IDaaS/SSO)
Okta, Azure AD, Google Workspace, JumpCloud unify authentication, apply MFA, and give you de-provisioning control.
Security stack
CASB/SSE, DLP, CSPM and EDR/XDR (e.g., CrowdStrike, Fortinet, IBM, Wiz) to enforce policies across SaaS, cloud and endpoints.
ITSM & CMDB
ServiceNow or similar to tie shadow IT into change, incident and asset management.
Mak It Solutions typically helps clients integrate these platforms into a cohesive operating model, rather than yet another siloed dashboard. (Mak it Solutions)
Selection Criteria for US, UK and German/EU Organizations
When evaluating vendors, your GEO lens matters.
EU & Germany
EU hosting options, clear data residency (Frankfurt, Dublin, Amsterdam), Schrems II posture and strong GDPR documentation. (EUR-Lex)
US healthcare & finance
HIPAA BAAs, PCI DSS alignment and evidence of SOC 2/ISO 27001 controls. (HHS)
UK public sector & regulated firms
UK GDPR, ICO guidance, NHS and FCA expectations around data sharing and outsourcing.
Also check integration with your core cloud (AWS, Azure, Google Cloud), Microsoft 365 or Google Workspace, plus any low-code platforms you plan to standardise on. (Mak it Solutions)
Turning Shadow IT and Shadow AI into an Innovation Asset
Shadow IT isn’t just a security headache; it’s a signal of where teams see value and where official tools fall short.
From Security Menace to Innovation Signal
Clusters of shadow SaaS or shadow AI around specific workflows onboarding, financial forecasting, marketing analytics tell you where teams are willing to invest their own time and budget. Instead of shutting everything down, treat these patterns as user research:
Which tools are gaining traction?
What features do they provide that your official stack doesn’t?
How can you meet that need in a governed way?
Many successful CIOs now explicitly track “innovation shadow IT” as a discovery source for future platform investments.
Governance Patterns.
Three patterns work well across US, UK and EU enterprises.
Innovation sandboxes pre-approved environments with synthetic or anonymised data, where teams can trial new SaaS and AI tools under clear constraints.
Curated catalogs an internal app store of approved tools and bundles (e.g., Microsoft 365 plus a small set of sanctioned AI copilots) with clear GEO/compliance tags.
Citizen development platforms standardised low-code/no-code platforms with governance baked in, instead of random spreadsheets or apps. (Mak it Solutions)
Measuring Value: KPIs for CIOs and CISOs
To show that shadow IT management creates value, track:
Reduction in unmanaged applications over 12–18 months
Time-to-approve new tools (especially for low-risk tiers)
Percentage of SaaS and AI apps behind SSO and MFA
Drop in audit findings related to third-party apps and data mapping
Business outcomes for example, faster onboarding flows in New York or Berlin, improved analytics in London or Frankfurt teams
A simple “Shadow IT Management 2025 KPIs” dashboard for German DSGVO-regulated companies (Shadow IT Management 2025 für deutsche Unternehmen – DSGVO-konform) helps keep this visible at board level.
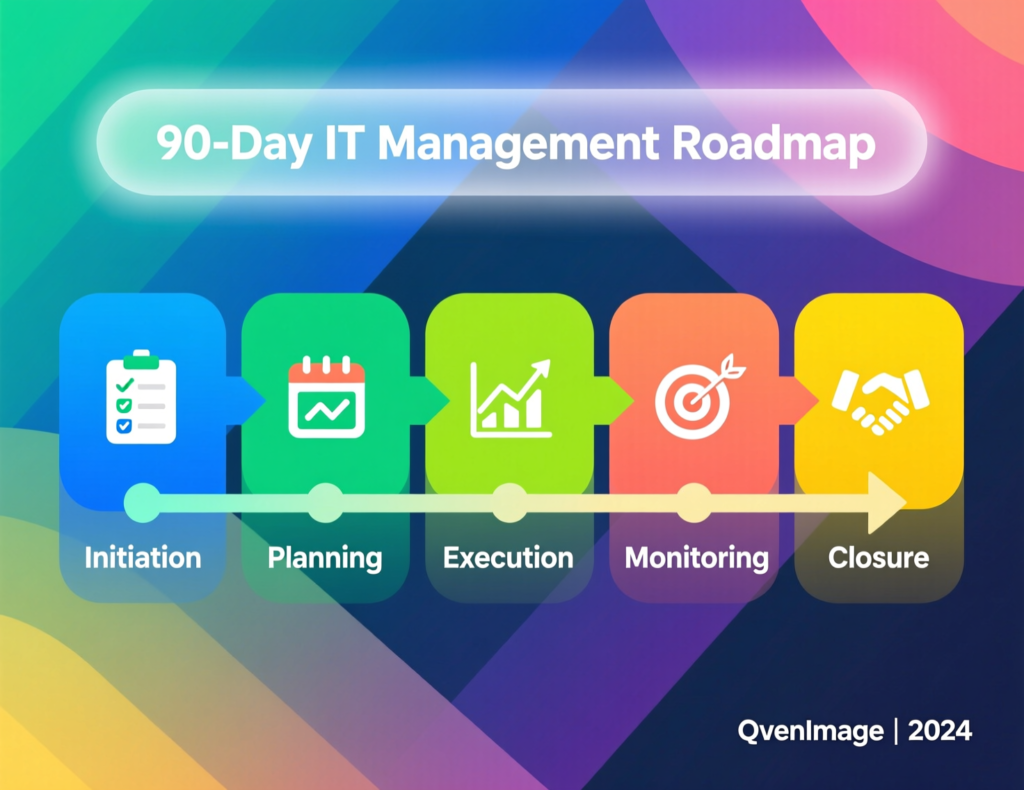
90-Day Shadow IT Management Roadmap for Global IT Leaders
You don’t need a two-year program to get started. Here’s a pragmatic 90-day shadow IT management roadmap you can adapt for US, UK and EU contexts.
Days 1–30 — Discover and Baseline Risk
Deploy discovery (network, SSO, browser, expenses) and build a first-pass shadow SaaS and AI inventory.
Map “crown-jewel” data (customer PII, ePHI, card data, source code) to the tools using it.
Identify high-risk apps (e.g., PHI in unsanctioned SaaS, EU personal data outside approved regions) and apply emergency controls or shutdowns where necessary.
Brief senior leadership on findings and immediate risk hotspots.
Days 31–60 — Design Policies, Governance and Tooling Stack
Draft your shadow IT policy, risk tiers and RACI; align with existing cyber, data and BI governance.
Stand up an intake and review process integrated with your ITSM tool.
Shortlist or pilot SaaS management, CASB/SSE, and identity platforms with GEO/data residency filters.
Align with legal, DPO and works councils (especially in Germany/EU) on data flows and DPIA expectations.
Days 61–90 — Roll Out, Communicate and Iterate Globally
Launch a communication campaign explaining why and how employees should declare or request tools.
Run pilots in at least three environments for example, a New York business unit, a London/NHS or FCA-regulated team, and a Munich or Berlin office.
Tune your policies and tooling based on real feedback; don’t be afraid to relax controls that create unnecessary friction.
For broader execution, consider partnering with a consultancy or platform team like Mak It Solutions to integrate governance into your web, mobile and cloud roadmaps, not bolt it on later. (Mak it Solutions)
Key Takeaways
Shadow IT management in 2025 is about continuous discovery and governance of shadow SaaS and shadow AI, not one-off cleanup projects.
The biggest risks are invisible data flows, weak access controls and regulatory gaps across GDPR/DSGVO, UK GDPR, HIPAA, PCI DSS, SOX and BaFin.
“Managed freedom” frameworks innovation sandboxes, curated catalogs and citizen-dev platforms let you control risk without killing innovation.
Tooling matters: combine network, SSO, browser and expense discovery with SaaS management, identity, DLP/CSPM and ITSM integration.
A 90-day roadmap (discover → design → roll-out) is enough to create visibility, address urgent risk and build a scalable operating model.
Partners with deep cloud, data and governance experience such as Mak It Solutions can help align shadow IT management with broader modernization and CIO agendas. (Mak it Solutions)
If you’re looking at your own SaaS and AI sprawl and suspect you’re only seeing half the picture, you’re not alone. Mak It Solutions already helps CIOs and CISOs in the US, UK, Germany and wider Europe design cloud, data and application architectures that make shadow IT visible, governable and genuinely useful.( Click Here’s )
Share your current landscape and regulatory constraints, and we’ll help you scope a 90-day shadow IT management plan from discovery and policy design to tooling integration across AWS, Azure, Google Cloud and your existing web and mobile platforms. Start by reaching out via the Mak It Solutions contact page and we’ll line up a focused working session with your team. (Mak it Solutions)
FAQs
Q : How much shadow IT is acceptable in a modern enterprise before it becomes unmanageable?
A : Some level of shadow IT is inevitable and even healthy in modern, cloud-driven enterprises. The tipping point is when you no longer have a reliable inventory of apps touching sensitive data, or when audits surface tools you’ve never heard of. A practical target is to ensure that all applications handling regulated or business-critical data are known, risk-assessed and behind SSO/MFA, while low-risk tools can be tolerated or managed via lighter-weight guardrails.
Q : Who should own shadow IT management CIO, CISO, or individual business units?
A : Ownership should be shared but clearly defined. The CIO typically owns the overall application and data strategy, while the CISO owns security and risk baselines; business units own the business outcomes and day-to-day use of tools. A simple model is: CIO sets the platform and catalog, CISO sets guardrails and monitoring, and business leaders own tool selection within those guardrails all coordinated through an IT steering or risk committee.
Q : What are practical examples of shadow IT in healthcare, finance and public sector organizations?
A : In healthcare, clinicians might use consumer file-sharing or messaging apps to share ePHI, or upload records to unapproved AI transcription tools. In finance, analysts could plug trading or customer data into unvetted SaaS analytics, bypassing PCI DSS and SOX controls. In public sector or NHS organizations, staff often spin up collaboration spaces or low-code apps outside central IT, sometimes hosted in regions that don’t meet local residency expectations. Each example illustrates why visibility, data mapping and governance are critical.
Q : How can mid-size companies with no dedicated CISO start managing shadow IT on a small budget?
A : Mid-size companies can start with lightweight but high-impact steps: turn on SSO and MFA wherever possible, use existing firewall/secure web gateway logs for basic discovery, and review expense data for rogue subscriptions. A part-time security lead (or virtual CISO) can define a simple policy, risk tiers and an intake process. From there, you can pilot affordable SaaS management or CASB tools and evolve controls as the business grows, rather than trying to copy a Fortune 500 security stack on day one.
Q : How should shadow IT findings be reported to boards and regulators during audits or incidents?
A : Boards and regulators expect transparency and a clear plan, not perfection. For routine reporting, summarize the number and type of unmanaged apps discovered, how many now sit behind SSO/MFA, and any remaining high-risk gaps with remediation timelines. During incidents, be ready to show how you identified affected tools, which data categories were involved, and what controls existed at the time. Align your narrative with frameworks like GDPR accountability, HIPAA Security Rule safeguards and PCI DSS principles so stakeholders can map your actions to familiar standards.


